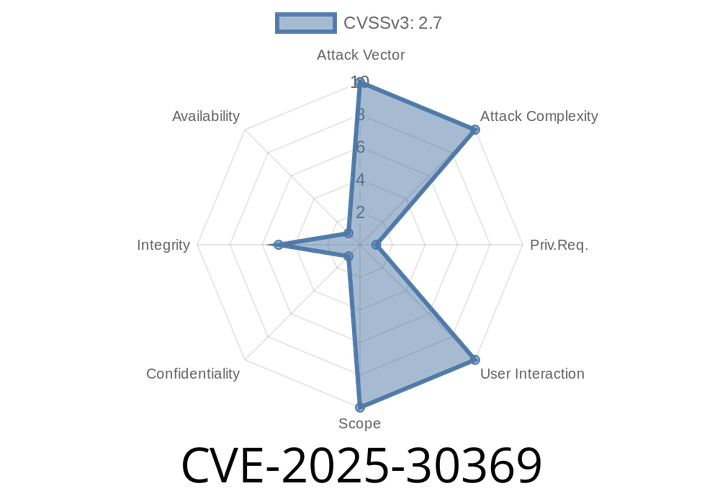
CVE-2025-30369 - Zulip Custom Profile Field Deletion Vulnerability (Explained with Code and Exploit Details)
CVE-2025-30369 is a newly reported vulnerability that affects Zulip, a popular open-source team chat platform. If you’re an IT admin or developer using Zulip
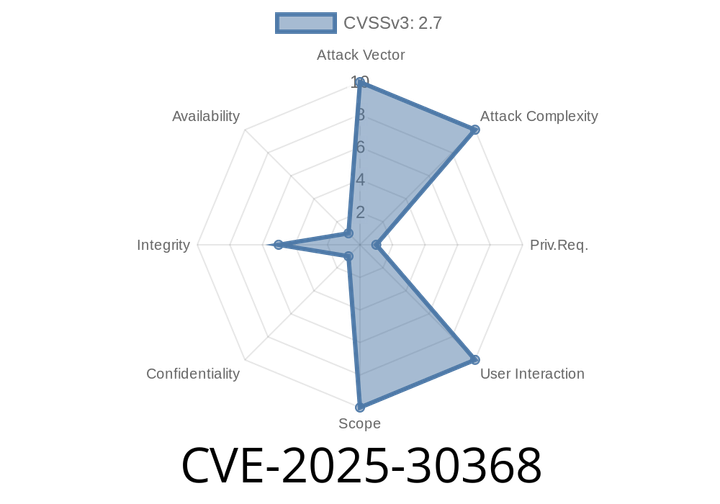
CVE-2025-30368 - How a Zulip API Permission Bug Let Admins Delete Data Across Organizations
Zulip is one of the go-to open-source chat platforms for teams, similar to Slack but with unique topic-based threading. Like any software, Zulip has its
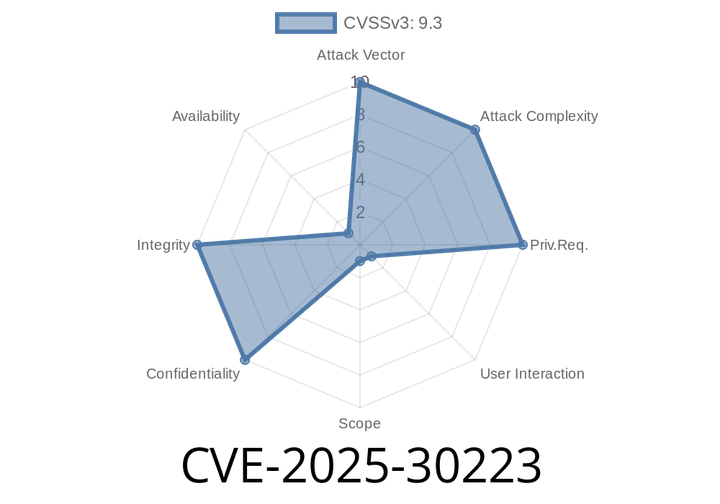
CVE-2025-30223 - XSS Vulnerability in Beego’s RenderForm() Function — What You Need to Know
Beego is a popular open-source web framework for the Go programming language. If you’re building web applications in Go, chances are you’ve run
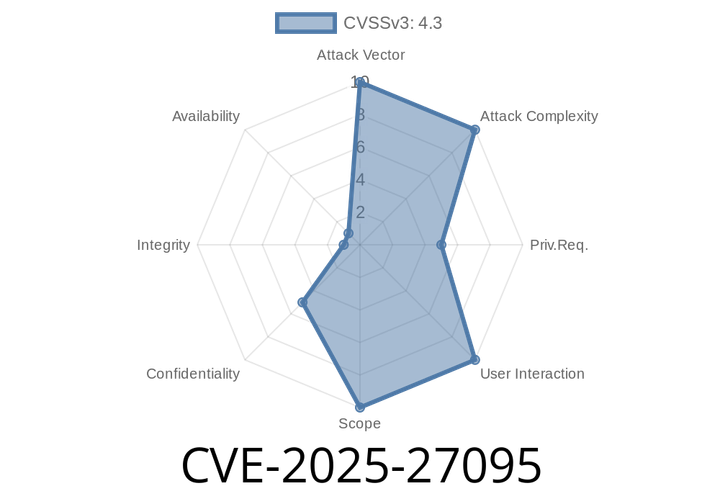
CVE-2025-27095 - JumpServer Kubernetes Session Vulnerability Explained (With Exploit Example)
JumpServer is a popular open-source bastion host used by organizations worldwide for secure access to internal systems and for operation and maintenance security auditing. It
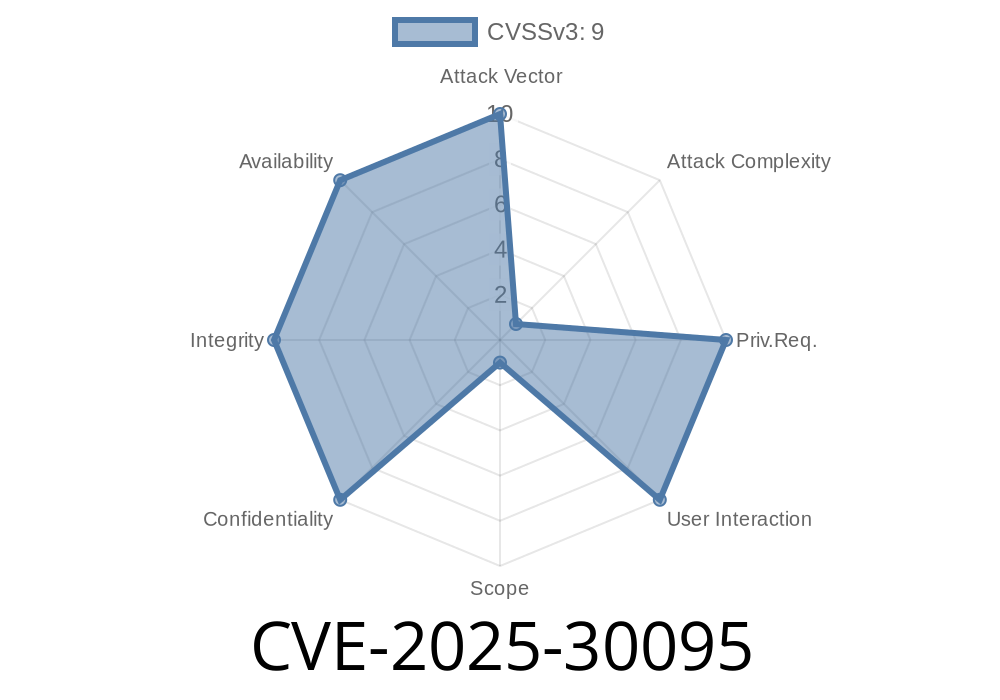
CVE-2025-30095 - Dropbear Host Key Reuse Exposes VyOS and Debian-based Systems to SSH MITM Attacks
In early 2025, a serious security weakness has been revealed affecting VyOS versions 1.3 through 1.5 (with a fix in 1.4.2)
Episode
00:00:00
00:00:00