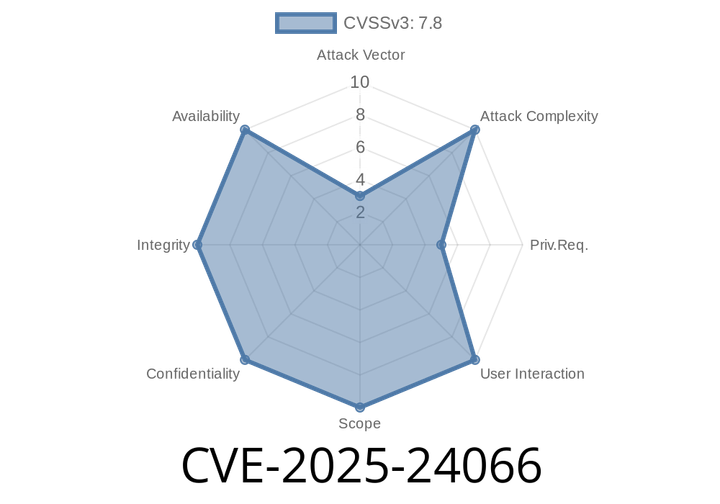
CVE-2025-24066 - Heap-based Buffer Overflow in Windows Kernel-Mode Drivers Lets Attackers Elevate Local Privileges
---
In early June 2025, security researchers disclosed a new vulnerability in various Microsoft Windows kernel-mode drivers. The vulnerability, officially tracked as CVE-2025-24066, allows attackers
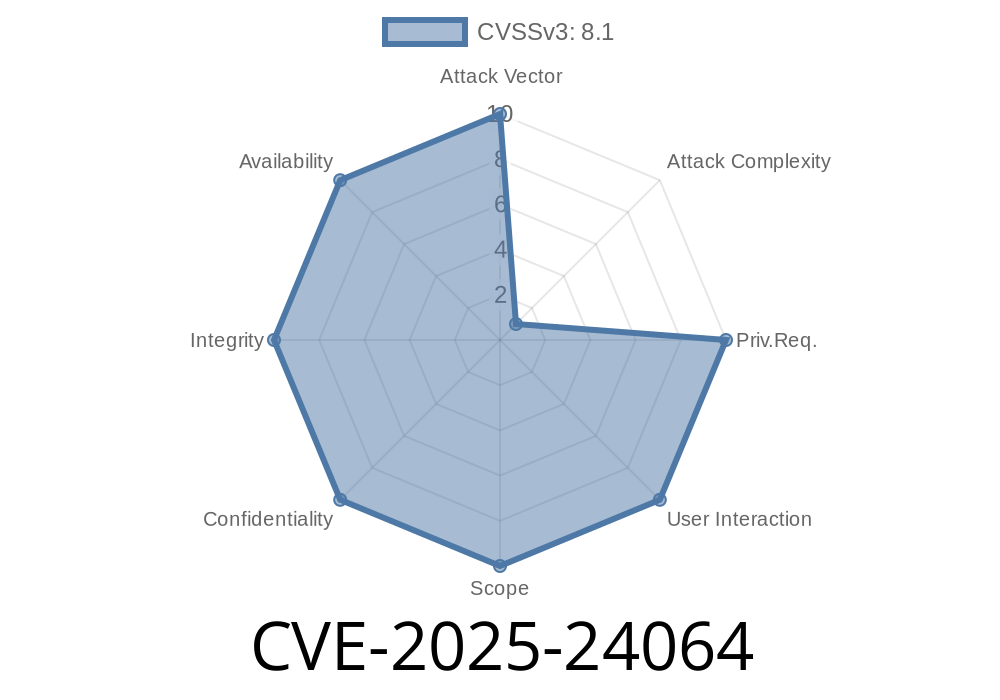
CVE-2025-24064 - Use-After-Free in DNS Server Lets Remote Attackers Execute Code
On February 2025, CVE-2025-24064 was uncovered—a serious "use-after-free" bug in several popular DNS server implementations. If you're running a DNS
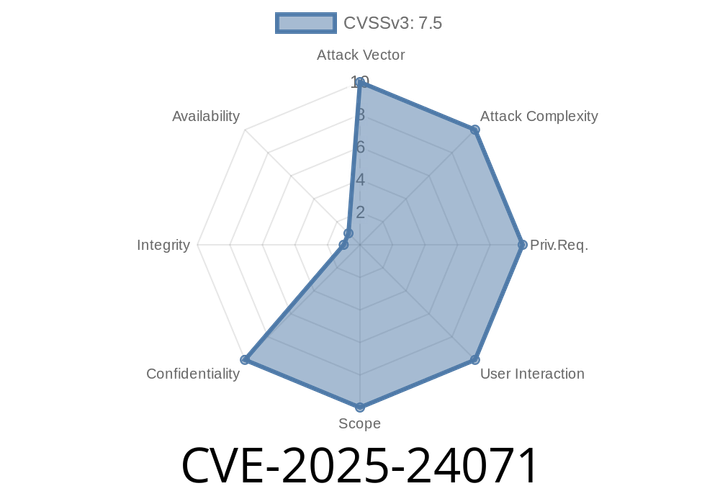
CVE-2025-24071 - Exploiting Windows File Explorer's Network Spoofing to Steal Sensitive Info
*Published: July 2024*
*Severity: High*
*Affected: Windows 10, 11, Server editions (details below)*
TL;DR:
CVE-2025-24071 reveals how Windows File Explorer leaks sensitive info over
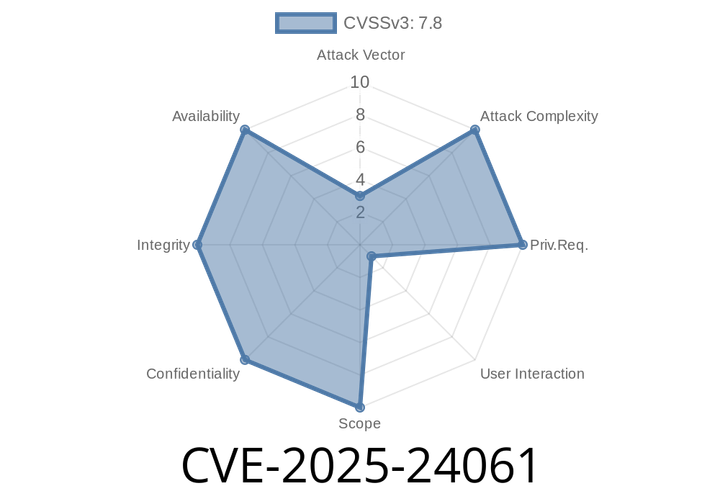
CVE-2025-24061 - Exploiting Windows Mark of the Web (MOTW) Protection Failure
---
Introduction
In 2025, a significant security issue was discovered in Microsoft Windows' Mark of the Web (MOTW) system: CVE-2025-24061. With this protection mechanism
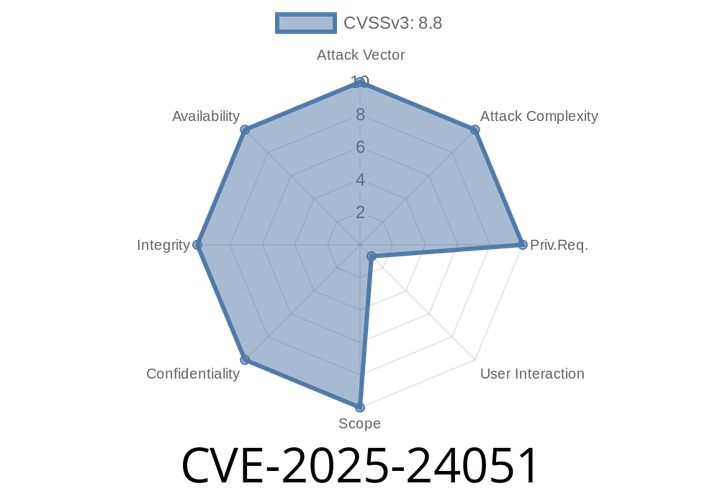
CVE-2025-24051 - Heap-Based Buffer Overflow in Windows RRAS—What You Need to Know
On February 13, 2025, Microsoft patched a critical vulnerability identified as CVE-2025-24051 in the Routing and Remote Access Service (RRAS) component of Windows. This flaw
Episode
00:00:00
00:00:00