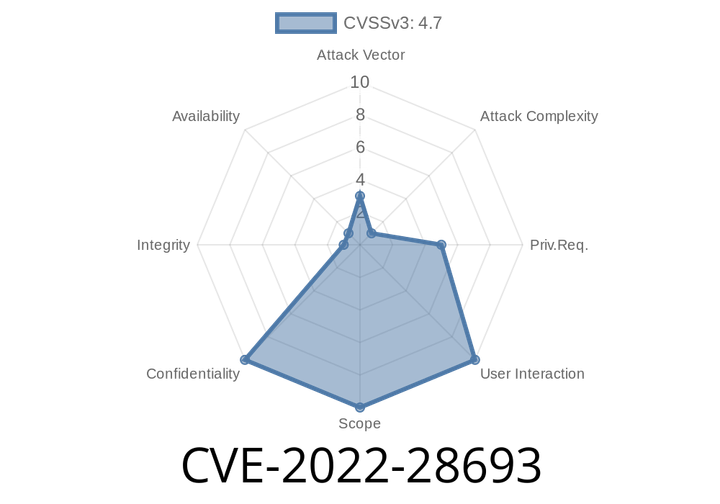
CVE-2022-28693 - Exploiting Unprotected Return Branch Target Prediction in Intel® CPUs
---
CVE-2022-28693 is a processor vulnerability quietly affecting several Intel® CPUs. This flaw allows local attackers to potentially disclose sensitive information by abusing an unprotected
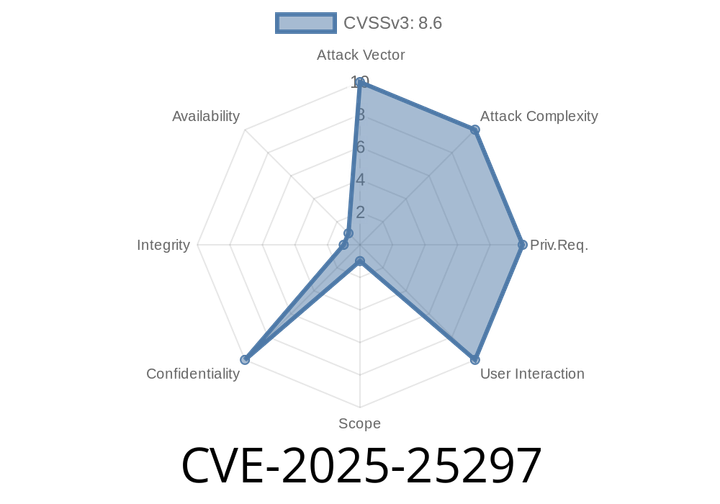
CVE-2025-25297 - Inside the Label Studio S3 SSRF Vulnerability – Explanation, Code, and Exploit Path
Label Studio is a popular open source data annotation tool used across industries for processing machine learning datasets. In early 2025, a severe vulnerability was
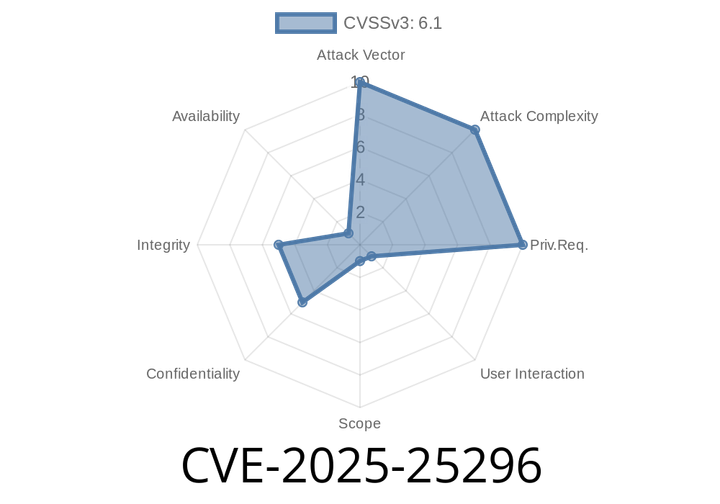
CVE-2025-25296 - XSS Vulnerability in Label Studio’s `/projects/upload-example` Endpoint — Explained
*Label Studio* is a popular open-source data labeling tool used by thousands of teams for annotating data to train machine learning models. On February 20th,
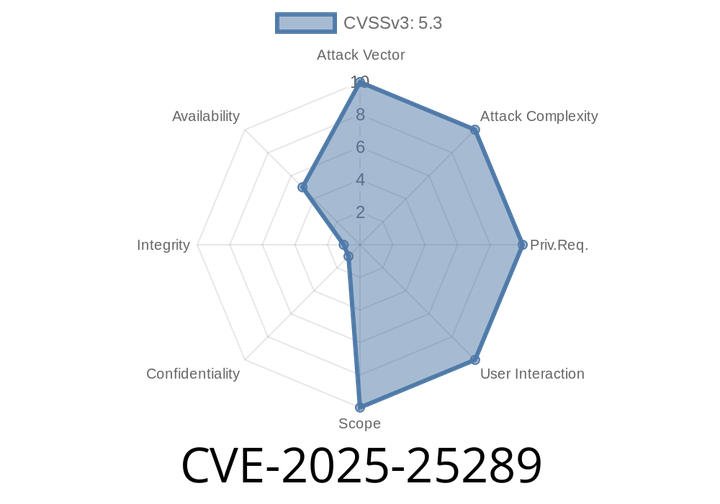
CVE-2025-25289 - ReDoS Vulnerability in @octokit/request-error—A Deep Dive and Exploit Walkthrough
This is an exclusive and in-depth look at CVE-2025-25289, a critical Regular Expression Denial of Service (ReDoS) vulnerability discovered in the popular @octokit/request-error library.
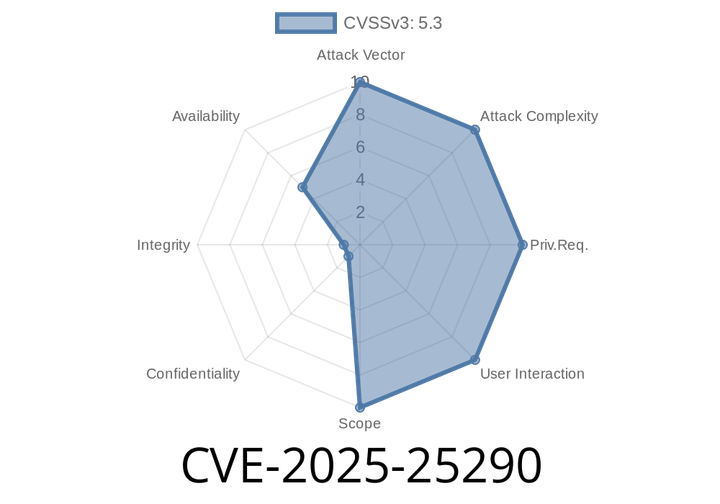
CVE-2025-25290 - How a Simple Regex in @octokit/request Can Crash Your Server (ReDoS Attack Exploit Guide)
On June 2025, security researchers identified and reported CVE-2025-25290, a critical vulnerability in the popular @octokit/request JavaScript library. Used widely to send parameterized requests
Episode
00:00:00
00:00:00