CVE-2025-24032 - How a Default PAM-PKCS#11 Setting Exposes Linux Systems to Certificate-Based Impersonation
CVE-2025-24032 highlights a critical security flaw in the PAM-PKCS#11 Linux Pluggable Authentication Module, used to let users authenticate using X.509 certificates (smart cards,
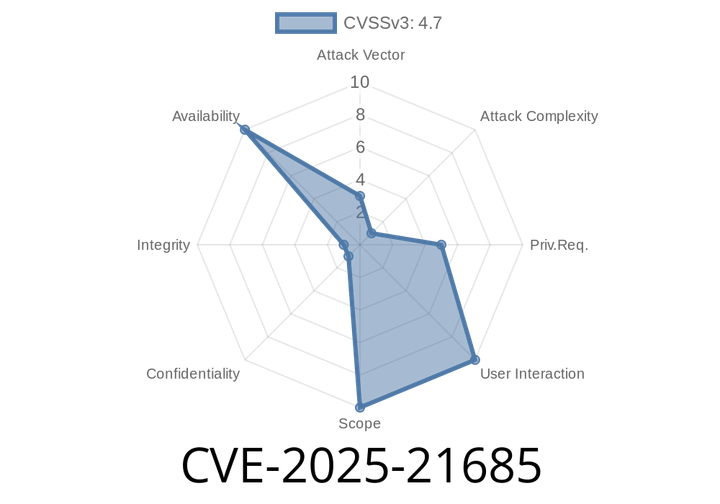
CVE-2025-21685 - Race Condition in Linux Kernel’s Lenovo Yoga Tab2 Pro Fast Charger Driver (Quick Fix Explained)
A dangerous race condition (CVE-2025-21685) in the Linux kernel’s Lenovo Yoga Tab2 Pro 138 Fast Charger driver could let attackers crash your device — or
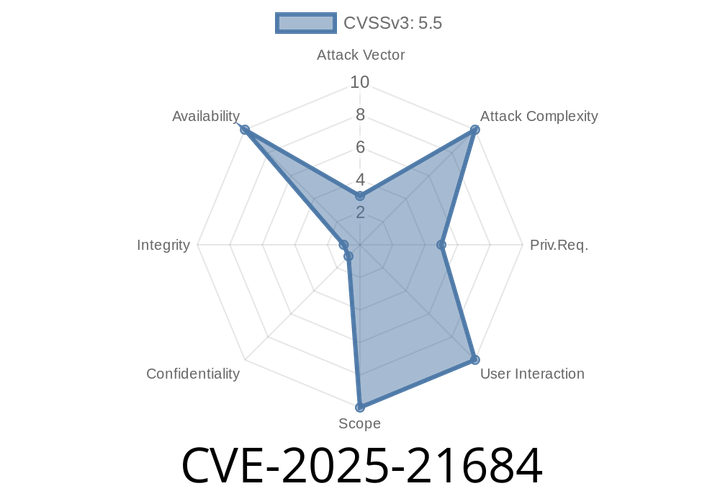
CVE-2025-21684 - Linux Kernel Xilinx GPIO Race Condition Fixed — Technical Deep Dive and Exploit Details
In early 2025, security researchers and kernel developers identified and resolved a subtle but potentially dangerous bug in the Linux kernel's handling of
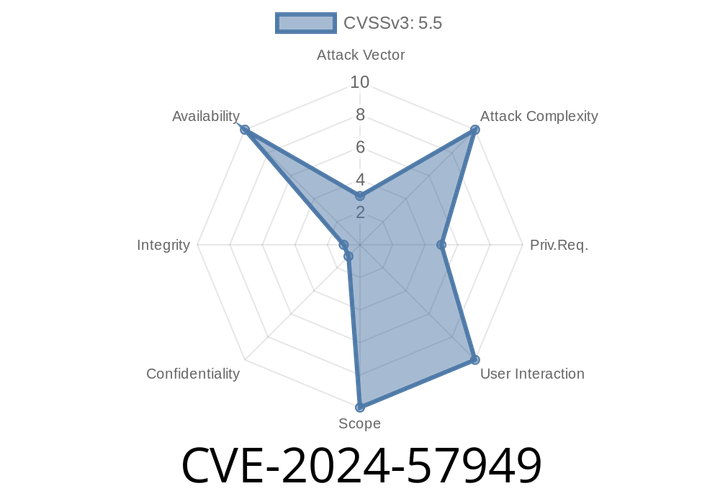
CVE-2024-57949 - Nested Interrupt Bug in Linux Kernel GIC-V3 ITS Fixed
On June 2024, a critical bug (now tracked as CVE-2024-57949) was found and patched in the Linux kernel’s irqchip/gic-v3-its subsystem. This vulnerability could
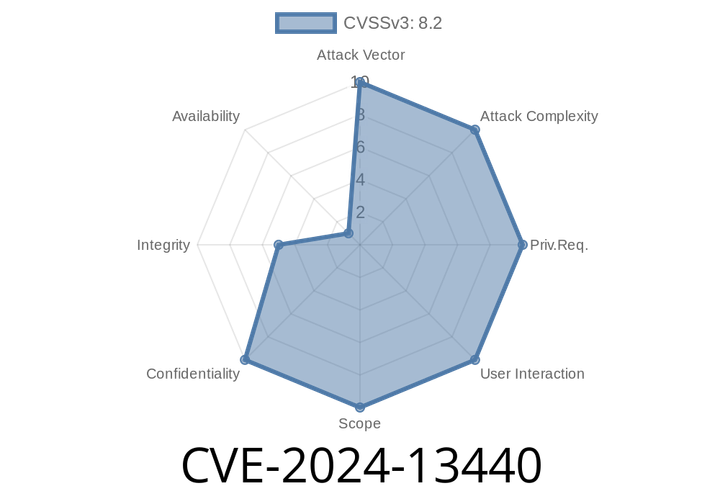
CVE-2024-13440 - Critical SQL Injection in Super Store Finder WordPress Plugin (Up to v7.) — How It Works, Exploit Details & Code Example
CVE-2024-13440 is a newly identified vulnerability found in the popular Super Store Finder plugin for WordPress. If you’re running any version up to 7.
Episode
00:00:00
00:00:00