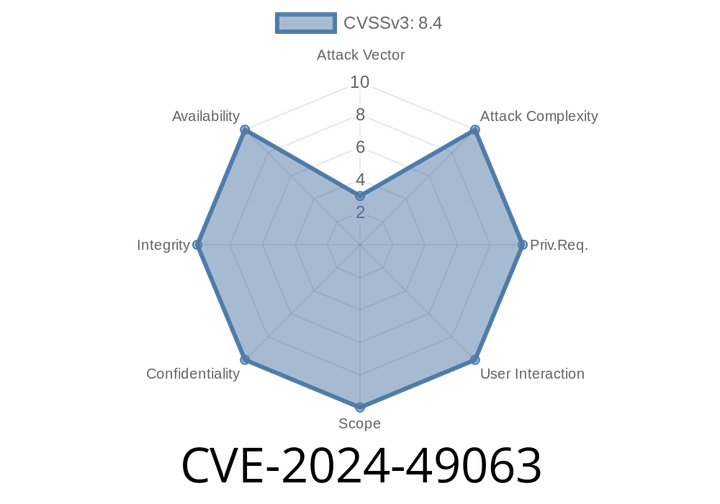
CVE-2024-49063 - Unpacking the Microsoft Muzic Remote Code Execution Vulnerability
> Disclaimer:
> This post is for educational purposes only. Do not attempt to exploit vulnerabilities on systems you do not own.
Introduction
In May
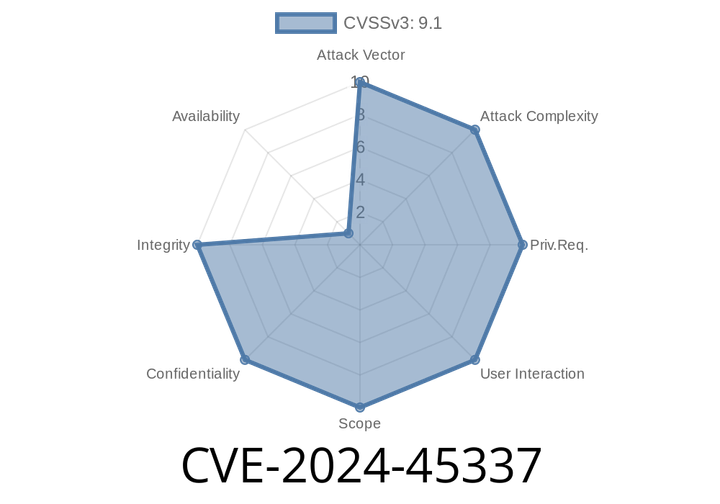
CVE-2024-45337 - Understanding the SSH Authorization Bypass Vulnerability in Golang Applications
Published: 2024-06-XX
Introduction
In June 2024, a significant vulnerability was discovered in the way some Go (golang) SSH servers handle public key authentication. Tracked as
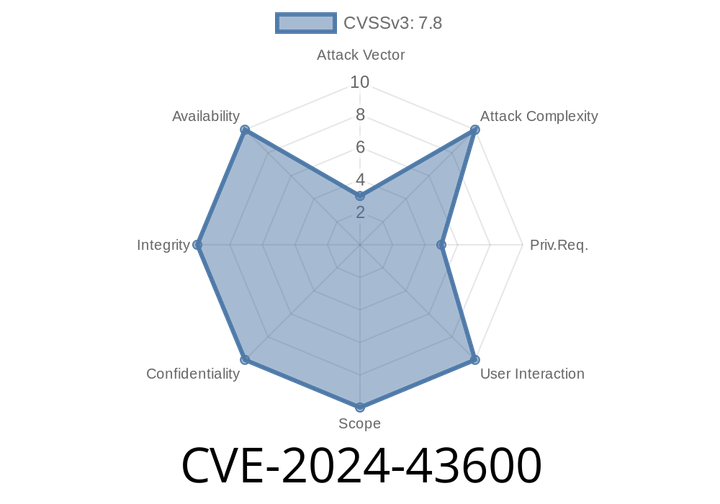
CVE-2024-43600 - Microsoft Office Elevation of Privilege Vulnerability Explained
In May 2024, Microsoft disclosed a significant security flaw identified as CVE-2024-43600. This vulnerability affects multiple versions of Microsoft Office, allowing attackers to escalate their
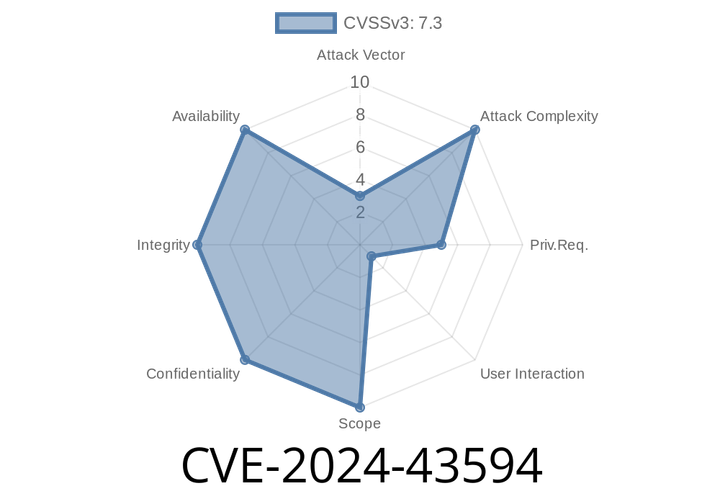
CVE-2024-43594 - Microsoft System Center Elevation of Privilege Vulnerability Explained with Example
---
Security vulnerabilities keep popping up everywhere, and every IT admin should take them seriously. One such threat in 2024 is CVE-2024-43594, an elevation of
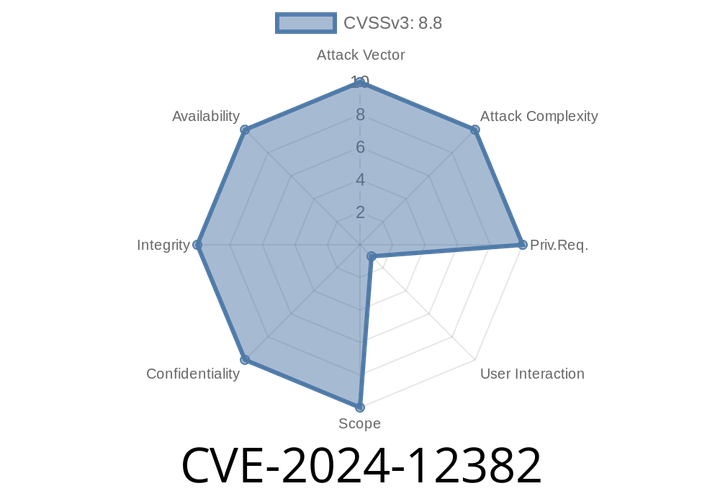
CVE-2024-12382 - Exploiting Use-After-Free in Chrome’s Translate – How Attackers Can Achieve Heap Corruption (With Code Example)
In April 2024, Google patched a high-severity bug in Chrome, tracked as CVE-2024-12382. This use-after-free vulnerability lurked within the browser’s translation subsystem, risking the
Episode
00:00:00
00:00:00