CVE-2022-31667 - How to Exploit Harbor's Robot Account Permission Bypass
> Exclusive Long Read: Understand and Exploit a Subtle but Serious Harbor Security Bug
What is Harbor?
Harbor is an open-source registry for storing, signing,
CVE-2022-31666 - Harbor Webhook Policy Permissions Flaw Explained & Exploited
Harbor is an open-source container image registry trusted by many organizations to safely store and manage their Docker images. In 2022, a critical security flaw—
CVE-2024-9693 - How a GitLab Kubernetes Agent Flaw Risked Your Cluster – Explained with Code and Exploit Details
In early 2024, GitLab disclosed a serious vulnerability (CVE-2024-9693) affecting its Community Edition (CE) and Enterprise Edition (EE) products. This vulnerability put countless Kubernetes clusters
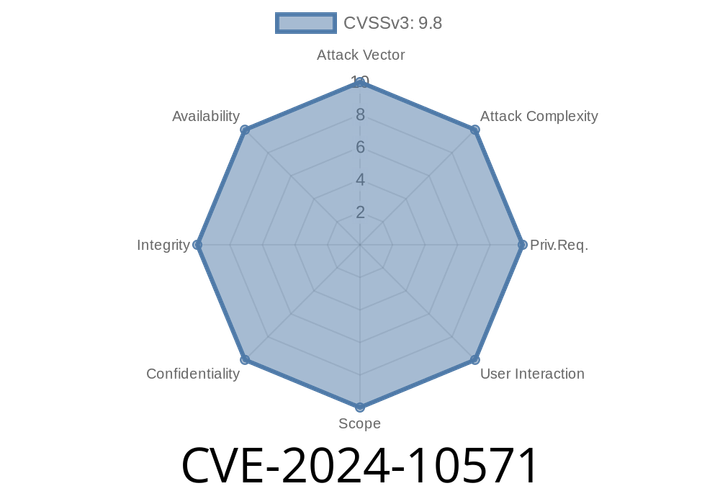
CVE-2024-10571 - Local File Inclusion (LFI) Flaw in Chartify – WordPress Chart Plugin
CVE-2024-10571 identifies a serious Local File Inclusion (LFI) vulnerability in the Chartify – WordPress Chart Plugin, affecting all versions up to and including 2.9.5.
CVE-2023-4134 - Use-After-Free in Linux cyttsp4_core Driver – Understanding the Exploit and Impact
Security in the Linux kernel is a constant arms race. One slip can create vulnerabilities that local attackers might use to crash systems or — in
Episode
00:00:00
00:00:00