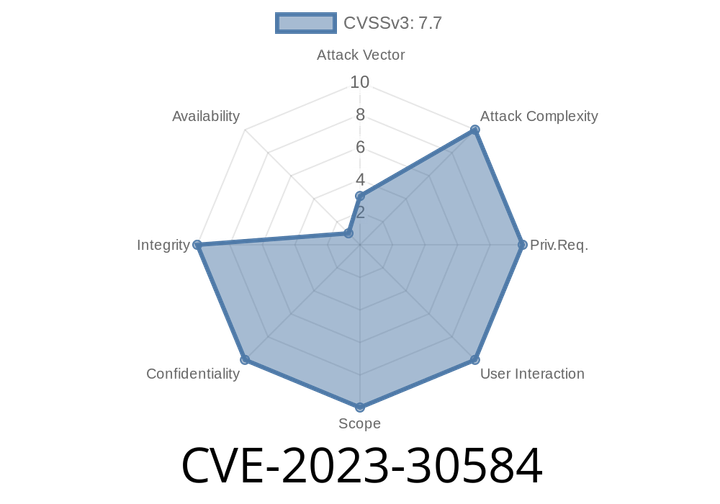
CVE-2023-30584 - Path Traversal Bypass in Node.js 20 Experimental Permission Model
Node.js is one of the world’s most popular server-side runtimes, powering everything from small apps to large-scale services. In early 2023, a vulnerability
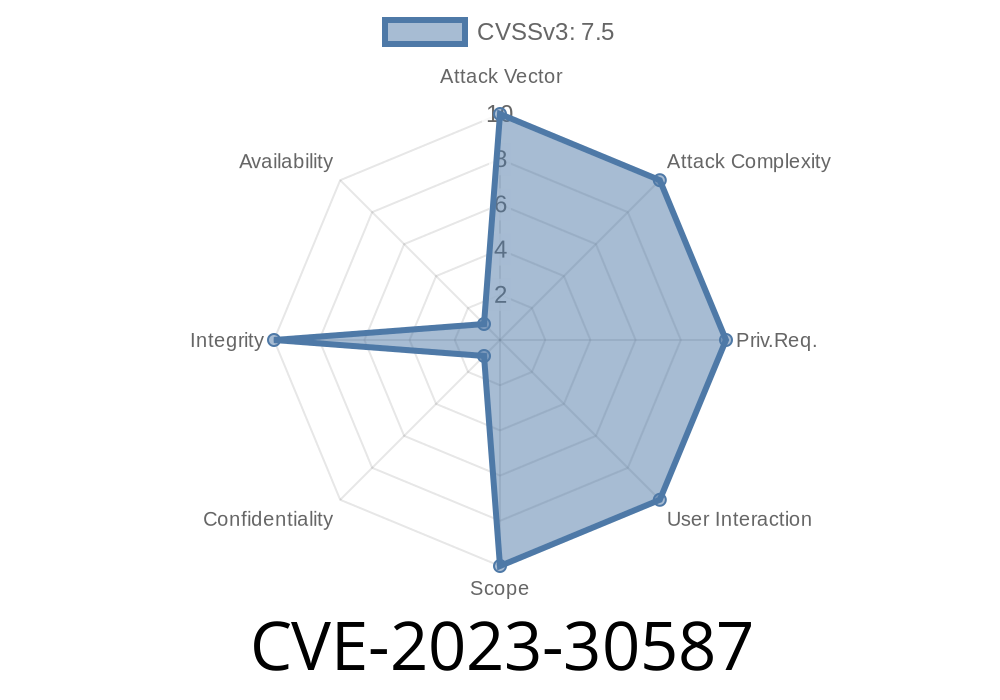
CVE-2023-30587 - Permission Model Bypass in Node.js 20 via node:inspector and Worker Internal API
The Node.js platform is used by millions of developers worldwide to build scalable and efficient server-side applications. One of its emerging security features is
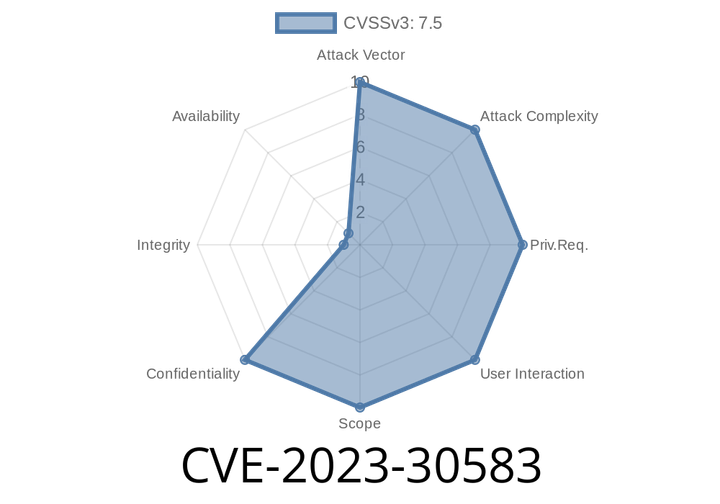
CVE-2023-30583 - How fs.openAsBlob() Bypassed Node.js 20’s File System Read Protection (Full Exploit Explained)
Node.js version affected: 20.x
Security risk: Medium-High (Experimental feature, but can be critical if adopted)
Exploitability: Trivial if using the feature
CVE page:
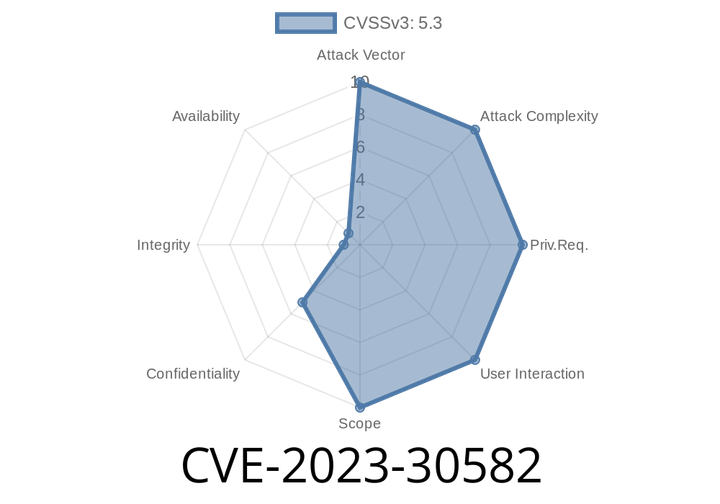
CVE-2023-30582 - Node.js Experimental Permission Bypass Through `fs.watchFile`
_Node.js version 20 introduced an experimental permission model to help restrict what code can do—such as reading files—using flags like --allow-fs-read. However,
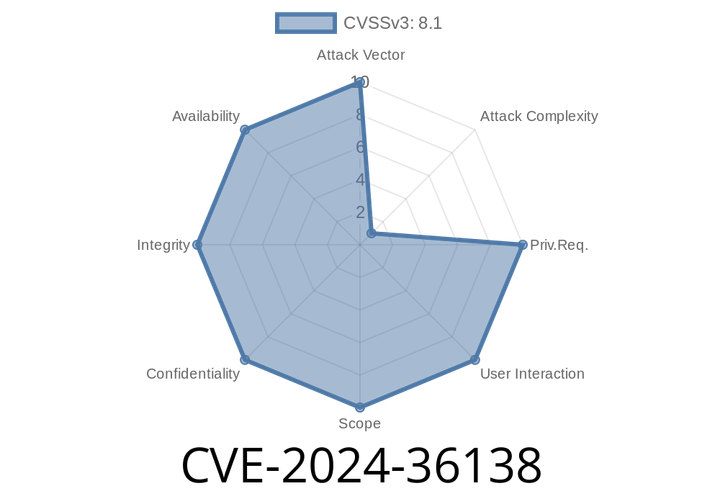
CVE-2024-36138 - Exploit and Technical Deep Dive—Bypassing the Incomplete Fix of CVE-2024-27980 in Node.js child_process.spawn without `shell` Option
---
Introduction
In April 2024, the Node.js community patched CVE-2024-27980, addressing a critical issue with command injection in the child_process.spawn function. The
Episode
00:00:00
00:00:00