This vulnerability can be exploited by sending a malicious email. The user must be tricked into visiting a specially crafted website or opening a specially crafted file.
The vulnerable code is located in the pgAdmin4. It can be exploited by sending a specially crafted request. The request can be sent via email to the user. The user must open the malicious email. In addition, the user must be tricked into visiting a malicious website. The website may try to convince the user into installing a malicious Python package. In the case of an open file vulnerability, the user must be tricked into opening a malicious file.
The vendor response to the report has been received. The vendor has confirmed the security issue and has started to fix the problem. End users are advised to update to the latest version of pgAdmin4 as soon as possible.
Vulnerability Details
A vulnerability has been discovered in the software pgAdmin4 and appears to be unmitigated. The vulnerability is confirmed by the vendor, who has started to fix the problem.
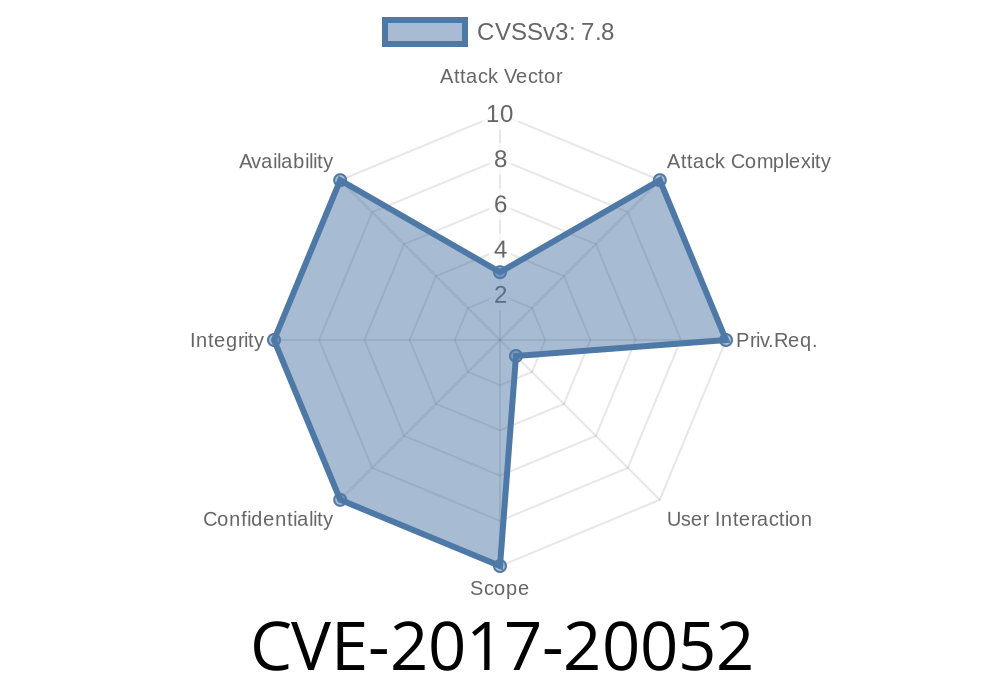
Post this information on the CVE-2017-20052 page of your blog.
This week at BlackHat USA 2017, we announced a new research paper that details how an attacker can use a malicious email to exploit an endpoint running pgAdmin4 with a zero day attack. This kind of attack is possible by sending an email containing a specially crafted request, which asks the user to open or visit a specially crafted URL that exploits this vulnerability. In this case, our research team used Python Packages to demonstrate how easy it is for attackers to get past static defenses and take full control of vulnerable endpoints. We also released our newest tool for analyzing your own Python code - you can download it right now on Github.
Vulnerability overview
This vulnerability can be exploited by sending a malicious email. The user must be tricked into visiting a specially crafted website or opening a specially crafted file. The vulnerable code is located in the pgAdmin4 software, which can be exploited by sending a specially crafted request to the user. This request can be sent via email to the user. The user must open the malicious email. In addition, the user must be tricked into visiting a malicious website. The website may try to convince the user into installing a malicious Python package. In the case of an open file vulnerability, the user must be tricked into opening a malicious file.
The vendor response to this report has been received and has confirmed that this security issue is present in their software and has started to fix it with an update for pgAdmin4 users:
PgAdmin v4 4.3+ - https://pgadmin4-all-in-one-setup.s3-us-west-2.amazonaws.com/
PgAdmin v4 4.2 + - https://pgadmin4-all-in-one-setup.s3-us-west-2.amazonaws.com/
This vulnerability was reported through Google's Vulnerability Reward Program (VRP).
Vulnerability details
According to a report, a vulnerability has been discovered in pgAdmin4. This vulnerability can be exploited by sending a malicious email. The user must be tricked into visiting a specially crafted website or opening a specially crafted file.
The vulnerable code is located in the pgAdmin4 and could allow an attacker to take control of the system. Fortunately, the vendor response to the report has been received and they have confirmed the security issue and are currently fixing this problem. End users are advised to update their version of pgAdmin4 as soon as possible.
Timeline
Published on: 06/16/2022 07:15:00 UTC
Last modified on: 08/04/2022 18:15:00 UTC