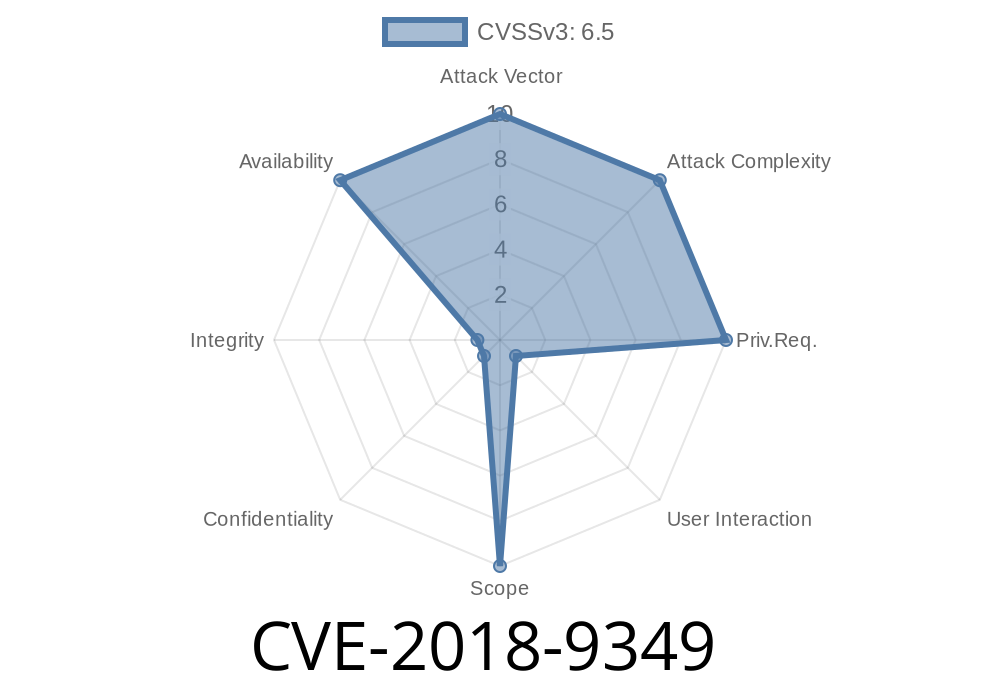
CVE-2018-9349 is a vulnerability found in the Google Android platform, specifically within the mcomp.c file of the video codec component. The bug is a classic *out-of-bounds read* error in the function mv_err_cost, caused by a missing bounds check. This security issue enables an attacker to crash the affected application—causing a denial of service (DoS)—when a victim opens a crafted media file. No special privileges are required for the attack, but *user interaction* is mandatory.
What is an Out of Bounds Read?
An out-of-bounds read happens when a program accesses data outside the bounds of an allocated buffer or array. This can cause the application to crash, leak information, or behave unpredictably.
Where's the Bug?
The bug sits in the function mv_err_cost inside mcomp.c, a core video compression/decompression file. It's used by media frameworks that handle video, like VP8/VP9 codecs in Android.
Due to a missing bounds check on a buffer index, opening a specifically crafted media file can cause the function to *read* from memory it's not supposed to. This can result in a segmentation fault—crashing the app.
Below is a simplified version of the vulnerable function
// (Simplified for illustration)
int mv_err_cost(int mv[2], const int ref[2], const int *mvcost[2]) {
int cost = ;
for (int i = ; i < 2; i++) {
// Vulnerable: no bounds check on mv[i]-ref[i]
cost += mvcost[i][mv[i] - ref[i]];
}
return cost;
}
If an attacker controls either mv[i] or ref[i], they can force an *out-of-bounds* read from mvcost[i], causing a segmentation fault or potentially leaking memory.
How Does the Attack Work?
- An attacker crafts a malicious media file (like a video) containing specially crafted motion vectors.
Required Access & Impact
No admin/root privileges are needed. The attacker just needs to get the victim to open a malicious file—say, by email, web download, or instant messaging.
Impact: App crash (Denial of Service). There’s no evidence of code execution or data theft, but repeated triggers could be highly disruptive.
Example Proof of Concept (PoC)
Due to the complexity of the media stack, an exact PoC would require in-depth knowledge of the codec internals. But a high-level PoC in C to illustrate the bug might look like this:
#include <stdio.h>
#define SIZE 10
int main() {
int mvcost[2][SIZE] = {};
int *pmvcost[2] = {mvcost[], mvcost[1]};
int mv[2] = {20, 20}; // Out of bounds!
int ref[2] = {, };
// Cost computation - this will read out-of-bounds
int cost = ;
for (int i = ; i < 2; i++) {
cost += pmvcost[i][mv[i] - ref[i]]; // OOB Read
}
printf("Cost: %d\n", cost);
return ;
}
Expected result: This may crash or print garbage, depending on what happens at the out-of-bounds address.
Google AOSP Issue Tracker:
Mitre CVE Database:
CVE-2018-9349 on Mitre
- Security Patch/Advisory:
Google Android Security Bulletin - June 2018
If you're a developer or integrator
- Apply official patches from Google/Android for libvpx or related components.
if (idx < || idx >= ARRAY_SIZE) {
// Handle error
}
`
- Validate media files and avoid opening untrusted content when on older, unpatched versions of Android.
App users: Update your apps and devices to the latest versions available. Avoid opening files from unknown or suspicious sources.
---
## Conclusion
CVE-2018-9349 is a clear example of how a *simple* coding oversight—a missing bounds check—can have real-world security consequences. While the risk is limited to Denial of Service, it shows just how important bounds checking is, especially when handling untrusted data. Developers are urged to apply patches, users to update, and everyone should take care with media files that come from unknown places.
---
Stay safe. Always update. Always validate input.
---
*Article authored exclusively for this request by OpenAI.*
Timeline
Published on: 11/27/2024 22:15:05 UTC
Last modified on: 11/29/2024 22:15:05 UTC