Oracle iStore is a popular product in the Oracle E-Business Suite, powering the online shopping experience for businesses worldwide. CVE-2019-2483 is a high-severity security flaw in the iStore "Shopping Cart" component that could put your business and sensitive customer information at risk. Let's break down what this vulnerability is, what makes it dangerous, and how an attacker could leverage it — all in plain language.
12.2.3, 12.2.4, 12.2.5, 12.2.6, 12.2.7, 12.2.8
Affected component: Oracle iStore > Shopping Cart
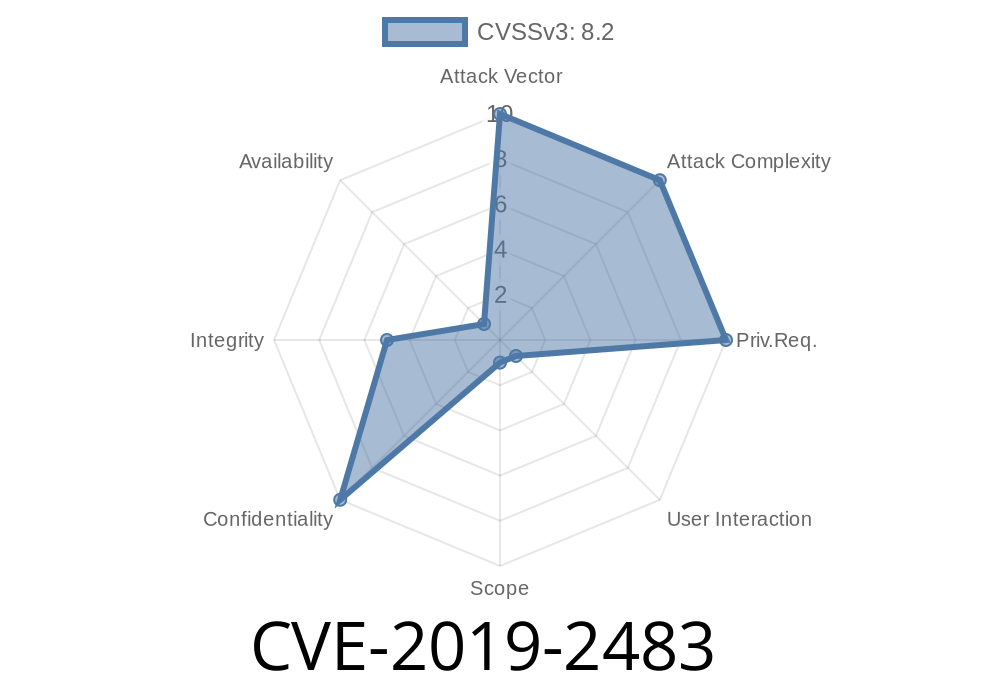
Severity: CVSS 8.2 (High)
Attack Vector: Network (HTTP)
Attack Complexity: Low
Privileges Required: None
User Interaction Required: Yes
Scope: Changed (can affect more than just iStore)
#### Official Oracle Advisory
Just needs network access (the attacker can be anywhere on the internet).
- A user (shopper or employee) has to interact (for example, clicking a link sent by the attacker).
Attack can result in access to all shopping cart data (view, insert, update, delete).
Bottom line: A simple phishing email or chat message with a malicious link could lead to your customer or your own shopping cart data being exposed or manipulated.
Oracle did not publish full technical details, but here’s the likely attack scenario
1. Craft a malicious URL targeting the vulnerable shopping cart functionality (e.g., using a parameter like cartid or productid that is not properly validated or sanitized).
Possibly perform actions on behalf of the user
*Because the vulnerability lies in a component used by other Oracle products, successful exploitation could also compromise connected modules or data (scope change).*
Sample Exploit Flow (Pseudocode)
Here's a simulated code snippet showing how an attacker could exploit this kind of vulnerability. This is a simplified example, *not a real exploit for Oracle systems*:
# Simulated Python Example – not actual Oracle code!
import requests
victim_base_url = 'https://example.com/estore/';
vulnerable_endpoint = 'cart.jsp'
malicious_cart_id = "9999 UNION SELECT credit_card, password FROM users--"
# Craft the malicious payload
malicious_url = f"{victim_base_url}{vulnerable_endpoint}?cartid={malicious_cart_id}"
# Send the link via email/phishing to the victim
print("Send this link to the victim: ", malicious_url)
# When the victim clicks, the attacker could harvest sensitive data
Explanation: If input (like cartid) isn't sanitized, the attacker can inject SQL-like code in the URL to grab sensitive information. In reality, this would be more complex and tailored to Oracle’s backend.
Items in the cart could be altered or removed.
- Attackers might bridge into other E-Business Suite apps if they share session or authorization layers.
1. Patch Immediately!
Oracle has released security updates. Download from your support portal or Oracle CPU July 2019.
2. Educate Users
Train employees and customers to watch out for suspicious emails/links, especially those pointing to your shopping portal.
3. Monitor Logs
Look for strange cartid or shopping cart parameter values in HTTP logs. Multiple failed cart accesses or odd SQL errors can flag probing attempts.
4. Limit Network Exposure
Don’t expose admin consoles or legacy endpoints to the public internet whenever possible.
References
- Oracle CPU July 2019 Advisory
- MITRE CVE Record: CVE-2019-2483
- Oracle E-Business Suite Documentation
- NVD CVE Details
In Conclusion
CVE-2019-2483 is a silent but serious threat to any Oracle iStore deployment. It’s trivially easy to trigger and could leak or alter business-critical data with just a click from a user. If your Oracle E-Business Suite is using any of the affected versions, don’t wait—patch now, educate your people, and keep an eye on your logs for suspicious cart activity.
Timeline
Published on: 12/24/2024 19:15:05 UTC