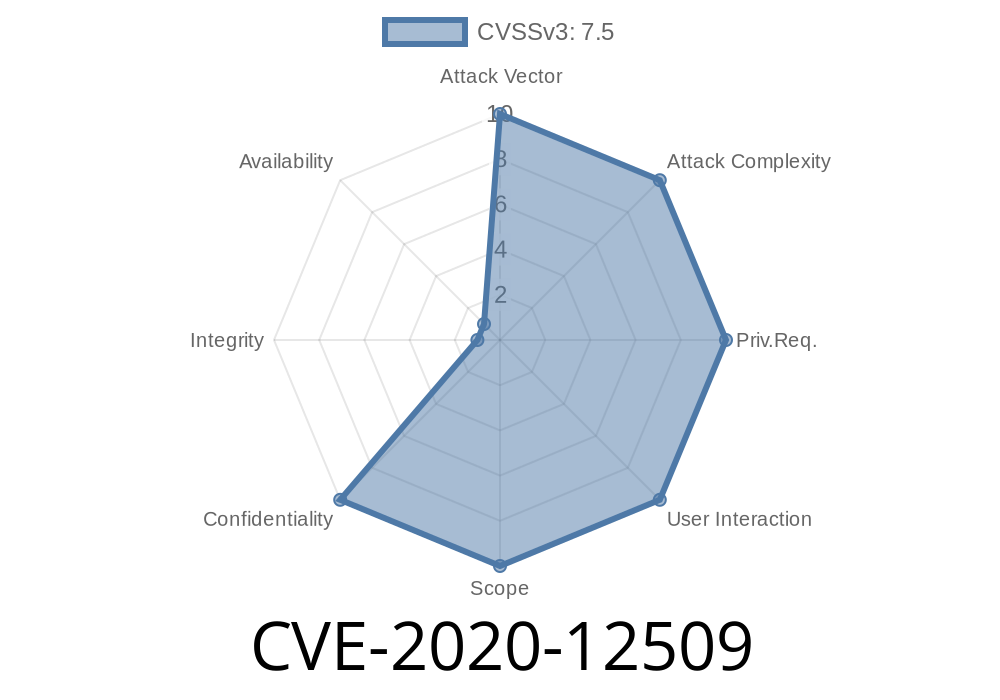
In version 4.2 and later, this issue was fixed by requiring a valid access token for the user to access the file.
In s::can moni::tools in versions below 4.2 an unauthenticated attacker could get any file from the device by path traversal in the camera-file module. In version 4.2 and later, this issue was fixed by requiring a valid access token for the user to access the file. An unauthenticated attacker could inject malicious JavaScript code into the website that will be executed in the browser of the user visiting the website.
In s::can moni::tools in versions below 4.2 an unauthenticated attacker could inject malicious JavaScript code into the website that will be executed in the browser of the user visiting the website. In s::can moni::tools in versions below 4.2 an unauthenticated attacker could inject malicious CSS code into the website that will be executed in the browser of the user visiting the website.
In s::can moni::tools in versions below 4.2 an unauthenticated attacker could inject malicious CSS code into the website that will be executed in the browser of the user visiting the website. In some cases, the camera-cloud module allowed unauthenticated users to upload files to the cloud.
In some cases, the camera-cloud module allowed unauthenticated users to upload files to the cloud. In some cases, the camera-cloud module allowed un
s::can moni::tools has been patched
s::can moni::tools has been patched.
Timeline
Published on: 11/07/2022 10:15:00 UTC