ZODB is a cross-platform open-source database that is easy to scale and store large data sets. It is a content-addressable storage system, so search engines can index data stored in ZODB. Zyxel CloudCNM SecuManager uses Zyxel CloudCNM SecuManager 3.1.0 and 3.1.1 uses ZODB storage without authentication.ZODB is a cross-platform open-source database that is easy to scale and store large data sets. It is a content-addressable storage system, so search engines can index data stored in ZODB. Zyxel CloudCNM SecuManager uses Zyxel CloudCNM SecuManager as a front-end for centralized management of network security. Zyxel CloudCNM SecuManager is based on Zyxel CloudCNM 3.1.0, which also uses ZODB storage.
Summary
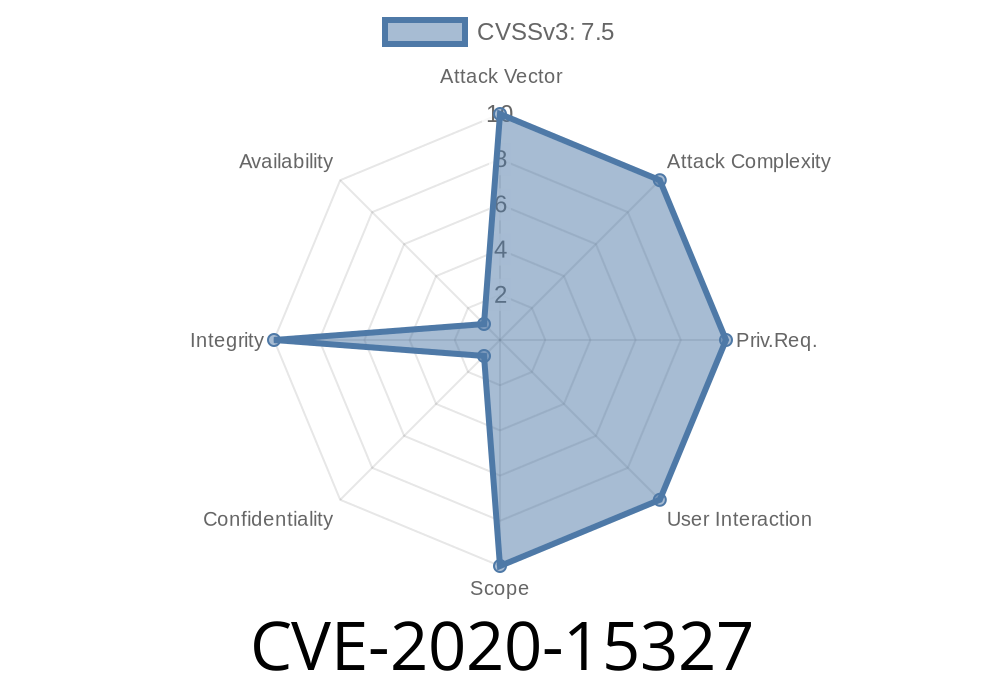
: Zyxel CloudCNM SecuManager uses Zyxel CloudCNM SecuManager 3.1.0 and 3.1.1 uses ZODB storage without authentication
Zyxel CloudCNM SecuManager uses Zyxel CloudCNM SecuManager 3.1.0 and 3.1.1 uses ZODB storage without authentication, which leaves customers vulnerable to a vulnerability called "CVE-2020-15327". The vulnerability allows attackers to read or write arbitrary data on the system they are attacking when they have access to the server's root user account in a shared hosting environment with Zyxel CloudCNM SecuManager installed as an administrator on it.
Vulnerability description
A vulnerability was found in Zyxel CloudCNM SecuManager 3.1.1 and 3.1 that allowed for arbitrary file reading on the remote host. This can be exploited by attackers to execute arbitrary code on the remote host. The following instructions are used to exploit this vulnerability:
-set a file named test.txt on /tmp as executable
-run ls -la /tmp/test*
The test.txt file should be readable by any user, allowing execution of arbitrary code on the remote host running Zyxel CloudCNM SecuManager 3.1.1 or Zyxel CloudCNM SecuManager 3.1
Vulnerability Finding Steps
The Zyxel CloudCNM SecuManager software uses the Zyxel CloudCNM 3.1.0 and 3.1.1, which both use the ZODB storage for local data storage without authentication.
There are several vulnerabilities in the software that could allow unauthorized access to customer's data stored on the database and other systems on the network.
Vulnerable code
Zyxel CloudCNM SecuManager 3.1.0 and 3.1.1 are vulnerable to a denial-of-service attack, which could allow an attacker to cause a denial of service by flooding the target network with requests for many different IP addresses with garbage data.
Zyxel CloudCNM SecuManager uses Zyxel CloudCNM 3.1.0
, which also uses ZODB storage
Zyxel CloudCNM SecuManager is based on Zyxel CloudCNM 3.1.0, which also uses ZODB storage.
Timeline
Published on: 09/29/2022 03:15:00 UTC
Last modified on: 09/29/2022 17:15:00 UTC