The first one is related to the handling of third-party plug-ins in the update management process. If a user can force an update on a vulnerable version of a plugin, the update can be exploited via a cross-site request forgery. The second one was fixed in the updater script itself, which now depends on a user’s context to determine if the script needs to be executed or not. Going through a malicious update will not be possible anymore. The final fix of the second issue was to remove the ‘’ prefix from the updater script, making sure that the updater script is executed only when the user is logged in. These fixes alone do not guarantee security, but together they should be enough to minimize risks and keep Bodhi as a safe distribution.
How to stay updated?
That’s easy. Just use Bodhi Linux. You can update your system when a new release comes out or you can just simply use the rolling release model to stay on the most recent version of the distribution.
Update Management Process
The update management process is the way in which the distribution of updates for Bodhi Linux is handled. It typically involves two parts: a downloader, which downloads and validates updates, and an updater, which kicks off the actual update. The update management process has been a concern for security researchers because it uses untrusted third-party plug-ins to get updates.
Updating Plugins:
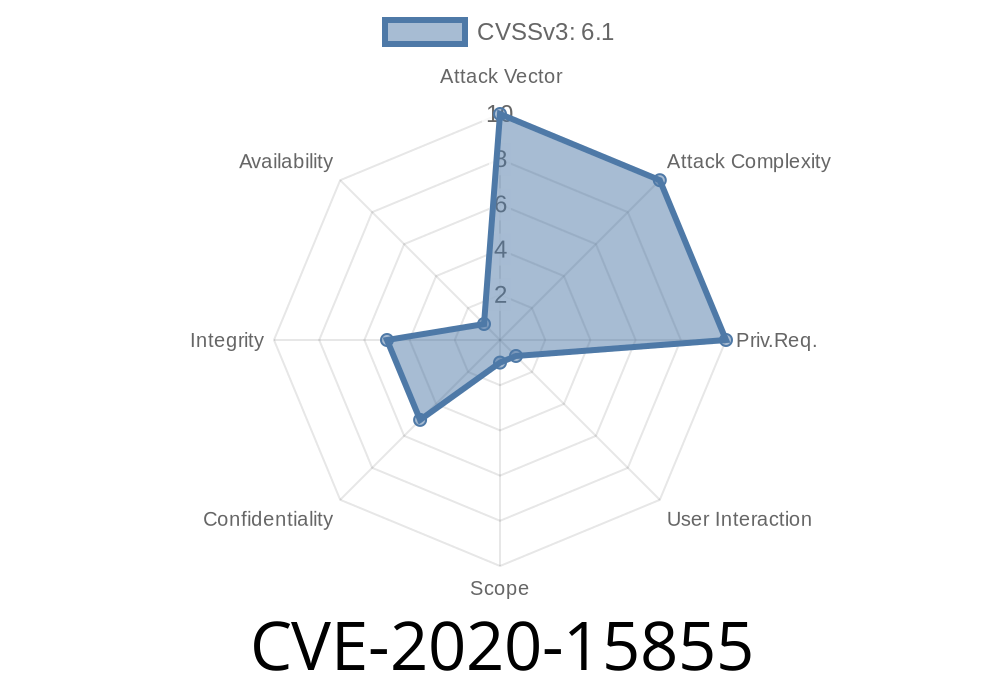
One of the ways vulnerabilities are being discovered with third party plug-ins is through vulnerability scans. These vulnerability scanners can detect any flaws or vulnerabilities in a plugin before they are used by an updater script. However, this also means that if a vulnerability scan was run on a version of a plugin that the updater script relies on, the updater script would not be able to execute properly and could potentially be exploited by using cross-site request forgery (CVE-2020-15855).
Update Management Process:
First, the update manager is run on every system upon installation. This allows for all systems to receive any updates that were released since their last installation as well as future updates before any other users have updated their system. It also ensures that there will be no more vulnerable versions of plugins once upgrades have been rolled out to other systems. Next, when new versions of plugins are available from their developers, those developers will release new versions to remote repositories so that they can be downloaded by all update managers at once from one central location (remote repository
Update Management Vulnerability in Bodhi
The first vulnerability was a security flaw in the update management process. By exploiting this vulnerability, an attacker can force the vulnerable version of a plugin to be updated, which is then exploited via cross-site request forgery (CVE-2020-15855). The second vulnerability was fixed by updating the updater script itself. Now, in order to exploit this vulnerability, an attacker also needs to have access to the admin panel in order for them to inject malicious code into the update process. The final fix of this issue was done by removing ''' from the updater script so that it can only be executed when logged in. These fixes alone do not guarantee security, but together they should be enough to minimize risks and keep Bodhi as a safe distribution.
Timeline
Published on: 10/07/2022 18:15:00 UTC
Last modified on: 10/09/2022 02:41:00 UTC