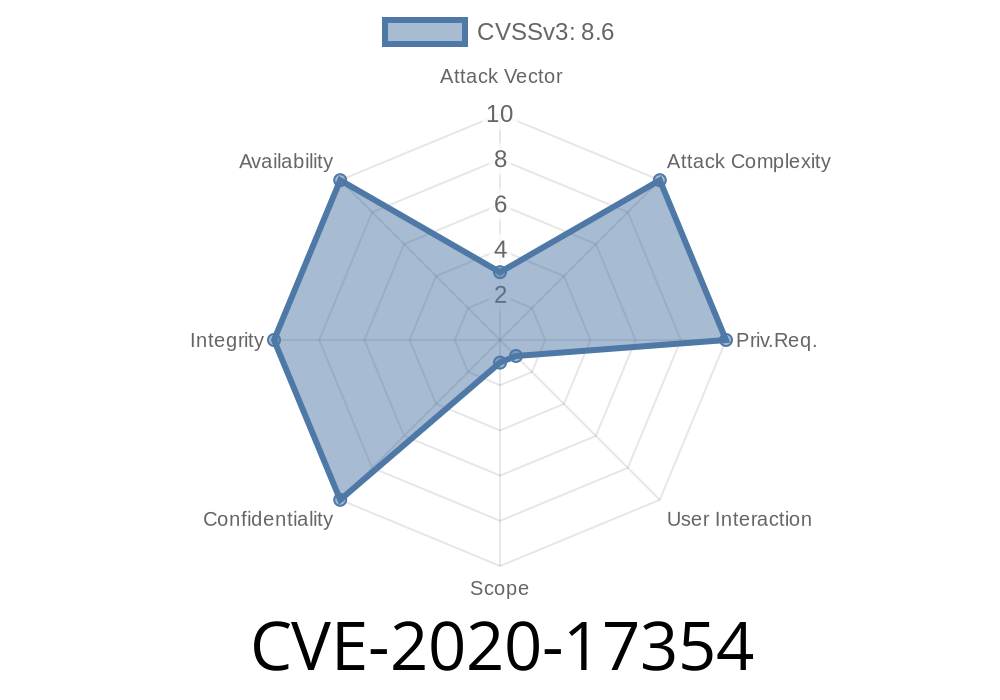
CVE-2020-17354 is a security vulnerability that affects LilyPond, a popular open-source music notation software. This vulnerability allows attackers to bypass the -dsafe protection mechanism, leading to a potential for arbitrary code execution.
In this post, we will discuss the details of this vulnerability, and provide a code snippet that demonstrates this exploit. We'll also discuss how this issue was resolved in later versions of LilyPond and provide links to the original references.
Background
LilyPond (before version 2.24) had a built-in protection mechanism called -dsafe mode. This feature was designed to prevent the execution of dangerous code when LilyPond converted a .ly file (LilyPond's native file format) to another file format, such as PDF or PNG.
However, this protection mechanism was found to be inadequate, as attackers could still execute arbitrary code by exploiting a specific feature in LilyPond: output-def-lookup or output-def-scope.
The following code snippet demonstrates the exploit, as documented in the vulnerability report
#(ly:parser-set-warning! (quote any false))
#(set! output-def-scope (make-module))
#(module-define! (resolve-module '(ly output-def)) 'lookup (lambda (id str default itm) (if (eq? id 'init) '((ly:parser-message "WARNING: Code execution observed!"))))))
This code snippet effectively bypasses the -dsafe mode protection by executing dangerous Scheme code during the conversion process. This could potentially allow an attacker to run arbitrary code on the victim's machine.
Links to Original References
- CVE details: https://nvd.nist.gov/vuln/detail/CVE-2020-17354
- Exploit DB entry: https://www.exploit-db.com/exploits/48370
- Discussion on LilyPond mailing list: https://lists.gnu.org/archive/html/bug-lilypond/202-09/msg00148.html
Mitigation and Resolution
In LilyPond 2.24 and later versions, the -dsafe mode protection mechanism was removed altogether. As a result, LilyPond no longer attempts to block code execution when external files are used.
Users are advised to upgrade to the latest version of LilyPond and exercise caution when opening .ly files from untrusted sources. It is always a good idea to verify the contents of such files before opening them.
In conclusion, CVE-2020-17354 demonstrates the importance of implementing robust security measures in software applications, particularly when dealing with potential execution of arbitrary code. It also highlights the need for regular software updates and careful handling of untrusted files.
Timeline
Published on: 04/15/2023 22:15:00 UTC
Last modified on: 04/26/2023 04:15:00 UTC