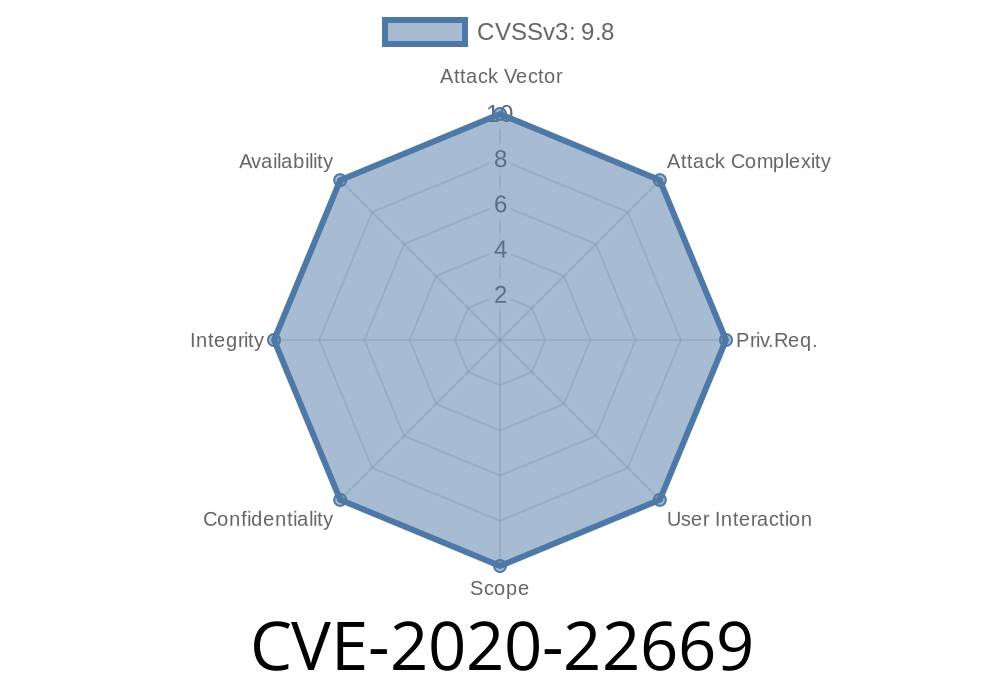
This issue is rated at a severity level of 2.1 by OWASP and has been assigned the ID of 20164. A attacker can exploit this vulnerability to bypass the WAF protection and inject malicious code into the database of an application or server. This can result in data manipulation, session hijacking, illicit financial transactions, or any other type of malicious activity that can be accomplished by executing SQL statements in an application's database. Paranoia level at PL1 is the severity level used by Modsecurity to indicate a high level of risk for potential critical security problems.
Overview
An SQL injection vulnerability exists in the application or server. This can allow an attacker to bypass the WAF protection and inject malicious code into the database of an application or server. This can result in data manipulation, session hijacking, illicit financial transactions, or any other type of malicious activity that can be accomplished by executing SQL statements in an application's database.
Vulnerability Overview:
How to avoid exploitation of this vulnerability
This vulnerability can be exploited by a remote attacker if the backend database is vulnerable. The best way to avoid exploits of this vulnerability is to use an application firewall such as Modsecurity that can detect and block suspicious activity. If your application does not have advanced security features, then you should consider implementing one in order to stop multiple vulnerabilities from being exploited.
Vulnerable corner case
This is a dangerous vulnerability that can be exploited by an attacker to execute SQL queries in the database of an application and gain access to sensitive information. The severity level is rated at a PL1 level, indicating a high risk of critical security problems. A good example of how this would be exploited is if an attacker could inject malicious code into the database and affect the integrity of data stored within. This would cause anything from illicit financial transactions, to data manipulation or session hijacking.
Timeline
Published on: 09/02/2022 18:15:00 UTC
Last modified on: 09/08/2022 03:25:00 UTC