This can be exploited via a specially crafted .fpx file to cause a denial of service condition within the affected application.
In order to exploit this issue, an attacker must be able to convince the victim to open a specially crafted .fpx file.
This can be done via email, newsgroups, or other means.
For an email based attack, the attacker must be in possession of an email with a .fpx attachment.
Diff000001 (Vuln#) Description: The function in which the vulnerability exists is called GetPlugInInfo which is located in the Formats module. It is a user-mode function so any process can be used to exploit this vulnerability.
In order to exploit this issue, an attacker must be in possession of a specially crafted .fpx file.
This can be done via email.
To exploit this issue, the attacker must be able to convince the victim to open the malicious .fpx file.
This can be done via phishing.
There are many ways in which an attacker can conduct a phishing attack.
This can be done via email, newsgroups, or other means.
For a newsgroup based attack, the attacker must be in possession of an email with a .fpx attachment.
For a newsgroup based attack, the attacker must be in possession of an email with a .fpx attachment.
There are many ways in which an attacker can conduct a ph
Vulnerable versions
The vulnerable version is a Windows operating system that is running on a 64-bit platform with the following conditions:
This can be exploited in all languages.
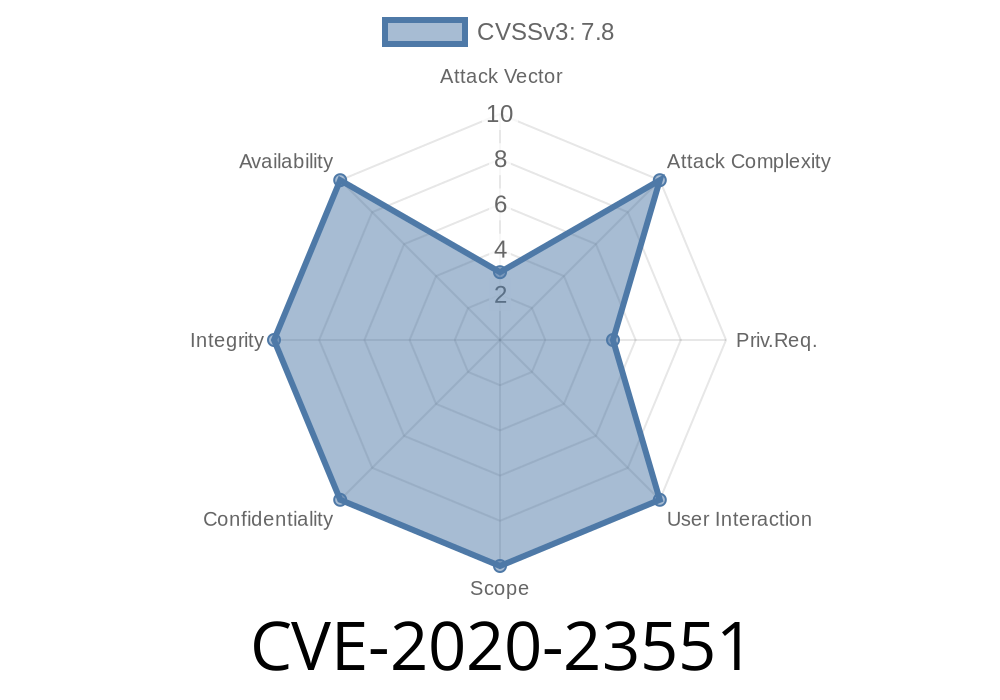
CVE-2020-23551
Timeline
Published on: 09/16/2022 03:15:00 UTC
Last modified on: 09/19/2022 17:48:00 UTC