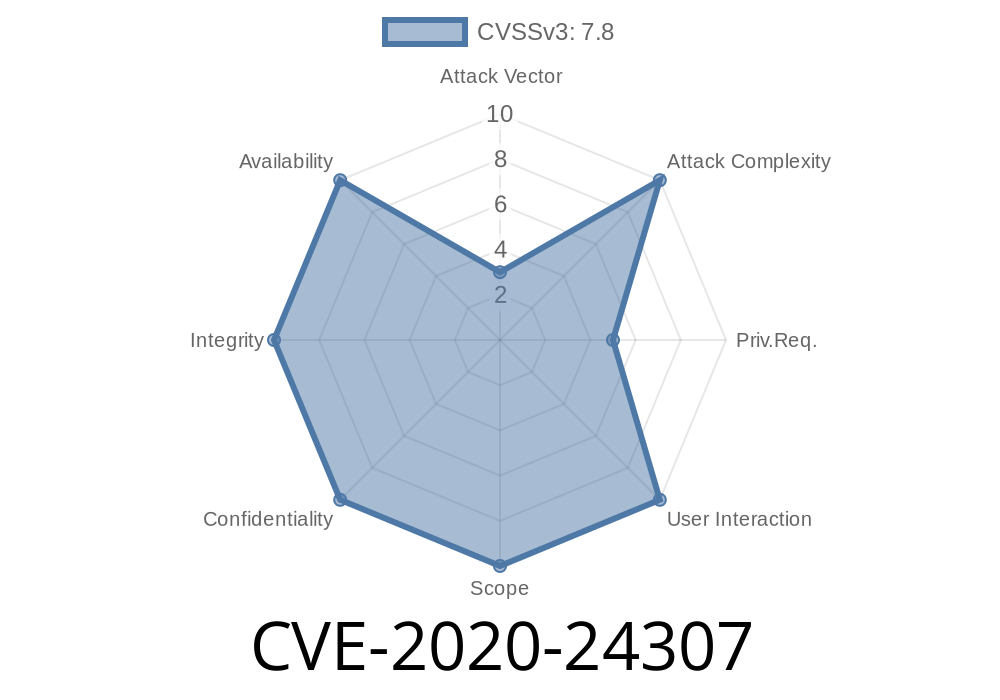
CVE-2020-24307 refers to an allegedly disputed issue in mRemoteNG v1.76.20, which supposedly allows attackers to escalate privileges through a crafted executable file. However, the claim's legitimacy is in question, as third parties have been unable to reproduce any scenario in which the claimed access of BUILTIN\Users:(M) is present.
In this long read, we will analyze the alleged vulnerability, provide code snippets, and discuss related references and exploit details.
mRemoteNG Overview
mRemoteNG is an open-source, multi-protocol remote connections manager, which supports tools like RDP, VNC, ICA, SSH, Telnet, HTTP/S, and more. Due to its extensive features and flexibility, the tool is widely used across multiple industries.
Original Reference
The initial report of the CVE-2020-24307 issue was published on GitHub (link to reference). The issue was filed under the title "Unquoted Service Path vulnerability in mRemoteNG v1.76.20."
Code Snippet
Here's the alleged code snippet in question from the mRemoteNG application, which supposedly triggers the privilege escalation issue:
HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{A16D9DB5-756E-4A2F-801D-17E41FCAAC01}_is1
"InstallLocation" "C:\Program Files\mRemoteNG-infected\"
Exploit Details
The alleged vulnerability is supposedly an "Unquoted Service Path" issue. Unquoted service paths are a common source of vulnerability in Windows operating systems, where an attacker could potentially replace the targeted executable file with a malicious one, ultimately leading to a privilege escalation.
However, as mentioned earlier, independent researchers could not reproduce any scenario in which the claimed access of BUILTIN\Users:(M) is present. Therefore, the legitimacy of this vulnerability remains uncertain.
Keeping Your Software Secure
Despite the uncertainty surrounding CVE-2020-24307, it's essential to keep your software and applications up to date. Regularly installing security updates and patches can protect you from genuine and undisputed security risks.
Conclusion
Although the claim of a privilege escalation issue in mRemoteNG v1.76.20 (CVE-2020-24307) remains disputed, it is crucial to remain vigilant and prioritize your software's security. Ensuring your applications are patched and up to date can help you avoid potential vulnerabilities and safeguard your digital assets.
Timeline
Published on: 02/02/2023 12:15:00 UTC
Last modified on: 02/17/2023 14:15:00 UTC