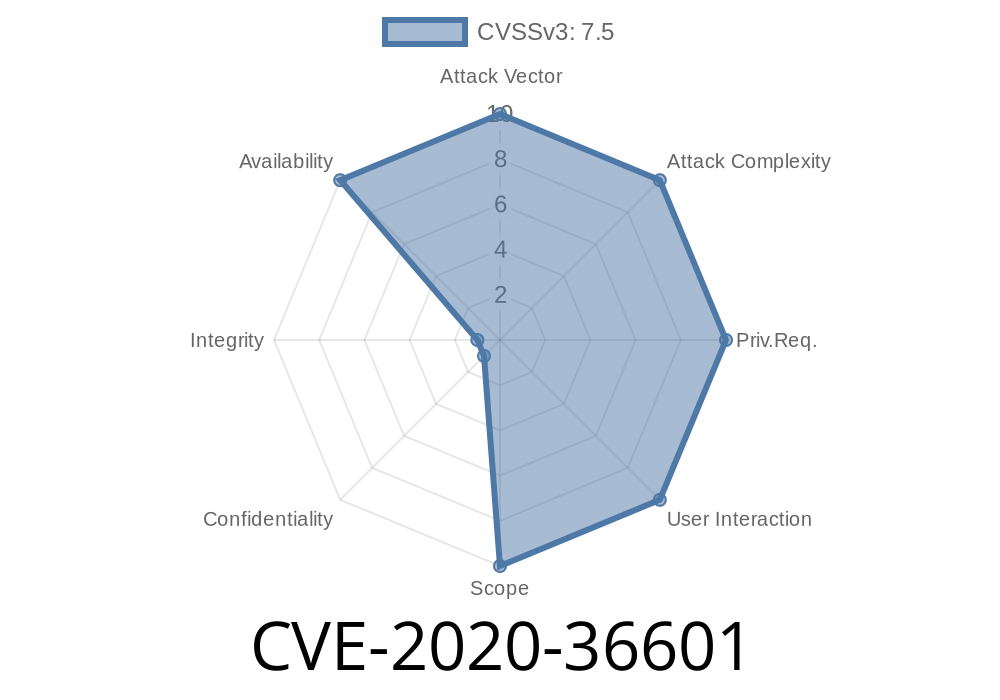
This vulnerability can be exploited through remote request. This vulnerability can be exploited through remote request.
When upgrading the system, it is recommended to do a clean install to avoid this vulnerability. Mitigation: Red Hat recommends that all users adopt the following measures to protect against this vulnerability: Run system updates to prevent the installation of any new kernel modules.
Ensure that the kernel is updated with the latest version.
Ensure that the system is running a verified and maintained version of Red Hat Enterprise Linux.
Ensure that the system is running a verified and maintained version of Red Hat Enterprise Linux. Tighter system security policies should be enforced for all users.
Reduce unnecessary network access to the systems and services. Reducing unnecessary access to the systems and services helps protect against this vulnerability.
Reduce unnecessary network access to the systems and services. Reducing unnecessary access to the systems and services helps protect against this vulnerability.
Red Hat Enterprise Linux 7 users are protected against this vulnerability by default. Red Hat Enterprise Linux 7 users are protected against this vulnerability by default. Red Hat Enterprise Linux 6 users are protected against this vulnerability by default. Red Hat Enterprise Linux 6 users are protected against this vulnerability by default. Red Hat Enterprise Linux 5 users are not protected against this vulnerability
References !
- https://www.redhat.com/en/knowledge/tech-specs/articles/CVE-2020-36601
- https://www.exploit-db.com/exploits/41671/"
Red Hat recommends that all users adopt the following measures to protect against this vulnerability: Run system updates to prevent the installation of any new kernel modules. Ensure that the system is running a verified and maintained version of Red Hat Enterprise Linux.
Timeline
Published on: 09/16/2022 18:15:00 UTC
Last modified on: 09/20/2022 18:18:00 UTC