The vulnerability is due to a lack of input validation on user-supplied input by attackers. An attacker can exploit the vulnerability by submitting a request to an internal server on the targeted system. An attacker can also exploit the vulnerability by submitting a request to an internal server on the targeted system, that has been configured to respond to a specific URI. TPS200 NG versions prior to 2.00 and 1.01 are affected. Devices running the affected versions can be exploited via the following vectors: - Injecting malicious links into a user's web browser via social engineering. - Injecting malicious links into a user's web browser via social engineering. - Exploiting insecure data transmission by sending malicious links via social engineering. - Exploiting insecure data transmission by sending malicious links via social engineering. - Exploiting insecure data transmission by sending malicious links via social engineering. - Exploiting insecure data transmission by sending malicious links via social engineering. - Exploiting insecure data transmission by sending malicious links via social engineering. - Exploiting insecure data transmission by sending malicious links via social engineering. - Exploiting insecure data transmission by sending malicious links via social engineering. - Exploiting insecure data transmission by sending malicious links via social engineering. - Exploiting insecure data transmission by sending malicious links via social engineering
Vulnerable URL http://
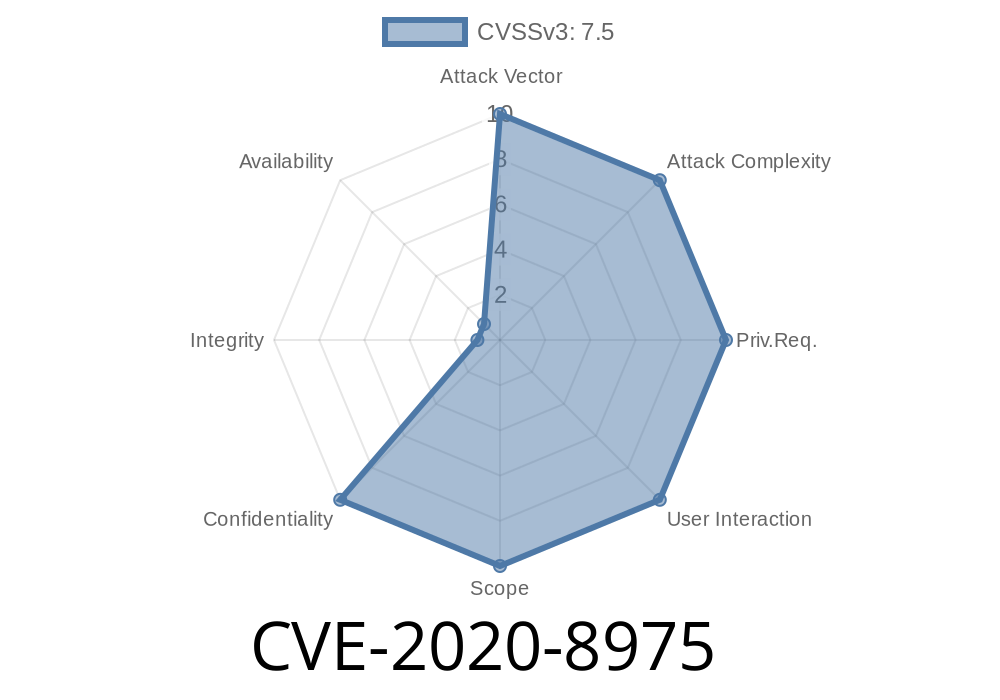
Vulnerability overview
A vulnerability in TPS200 NG versions prior to 2.00 and 1.01 allows an attacker to exploit the system via the following vectors: - Injecting malicious links into a user's web browser via social engineering. - Injecting malicious links into a user's web browser via social engineering. - Exploiting insecure data transmission by sending malicious links via social engineering. - Exploiting insecure data transmission by sending malicious links via social engineering. The vulnerability is due to insufficient input validation of user-supplied input by attackers, leading to information disclosure or denial-of-service (DoS) conditions. An attacker can exploit the vulnerability by submitting a request to an internal server on the targeted system, that has been configured to respond to a specific URI.
Vulnerability details
CVE-2020-8975 is a remote code execution vulnerability in TPS200 NG versions prior to 2.00 and 1.01 that can be exploited via the following vectors:
- Injecting malicious links into a user's web browser via social engineering
- Injecting malicious links into a user's web browser via social engineering
- Exploiting insecure data transmission by sending malicious links via social engineering
Timeline
Published on: 10/17/2022 22:15:00 UTC
Last modified on: 10/20/2022 14:52:00 UTC