This results in a potential for a malicious third party to steal login information, along with other sensitive data if the user had opened the malicious URL in their browser. To avoid being redirected to malicious sites, be sure to update Kibana to version 7.13.0 or higher.
If you are using Kibana on a production server, it is recommended that you apply the following mitigations to limit the impact of this issue on your business.
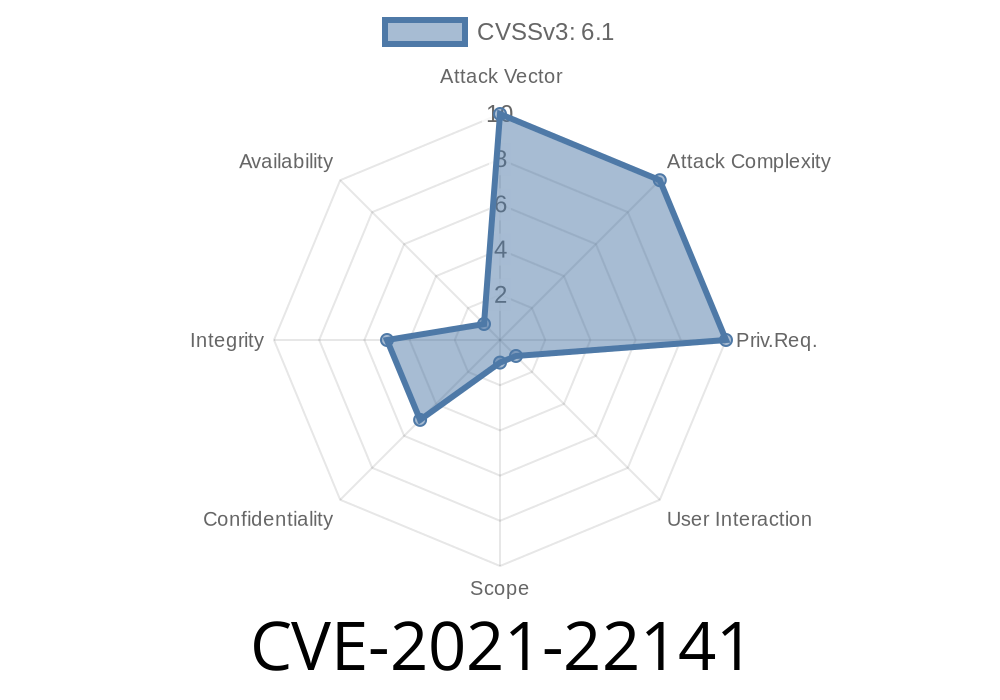
An open redirect flaw was found in Kibana versions before 7.13.0 and 6.8.16. If a logged in user browses to a malicious URL, it could result in Kibana redirecting the user to an arbitrary website.
Redirects can be used maliciously to trick users into revealing information or taking actions that they did not intend to take. When an open redirect flaw is present, you should immediately review logs to identify instances where users were redirected to sites they did not intend to visit.
Redirects can be used maliciously to trick users into revealing information or taking actions that they did not intend to take. When an open redirect flaw is present, you should immediately review logs to identify instances where users were redirected to sites they did not intend to visit.
Redirects can be used maliciously to trick users into revealing information or taking actions that they did not intend to take. When an open redirect flaw is present, you should immediately review logs to identify instances where
What is an Open Redirect?
An open redirect is a type of vulnerability that allows an attacker to "hijack" a user's browser and redirect the user to a malicious website or webpage. With an open redirect, the attacker takes control of the browser's address bar and replaces the original URL with one that they control. When users visit this malicious site, they are then automatically redirected to another site or webpage controlled by the attacker. This can potentially expose user information and create avenues for fraud.
What is a Redirect?
Redirects occur when a user follows a link to a website and is then redirected to another site. For example, when someone clicks on the URL http://www.example.com/page.html, they are redirected to http://www.example2.com/page2.html without any interaction from the user.
How to limit impact of this flaw on your business
The following mitigation steps should be taken to limit the impact of this issue on your business:
1. Upgrade to Kibana version 7.13.0 or higher, which is not vulnerable to this issue
2. Review logs to identify instances where users were redirected to sites they did not intend to visit
3. Implement other mitigations as needed
Timeline
Published on: 11/18/2022 23:15:00 UTC
Last modified on: 11/22/2022 21:13:00 UTC