When talking about computer security, one thing we often trust is that applications only do what they're allowed to do. But sometimes, a bug lets a program sneak past those limits. One such issue is CVE-2021-26280, where a silently installed app can force itself to run tasks far beyond its original permissions.
In this post, I’ll break down how this vulnerability works, show some code to help you recognize the danger, and link to the official sources for your own research.
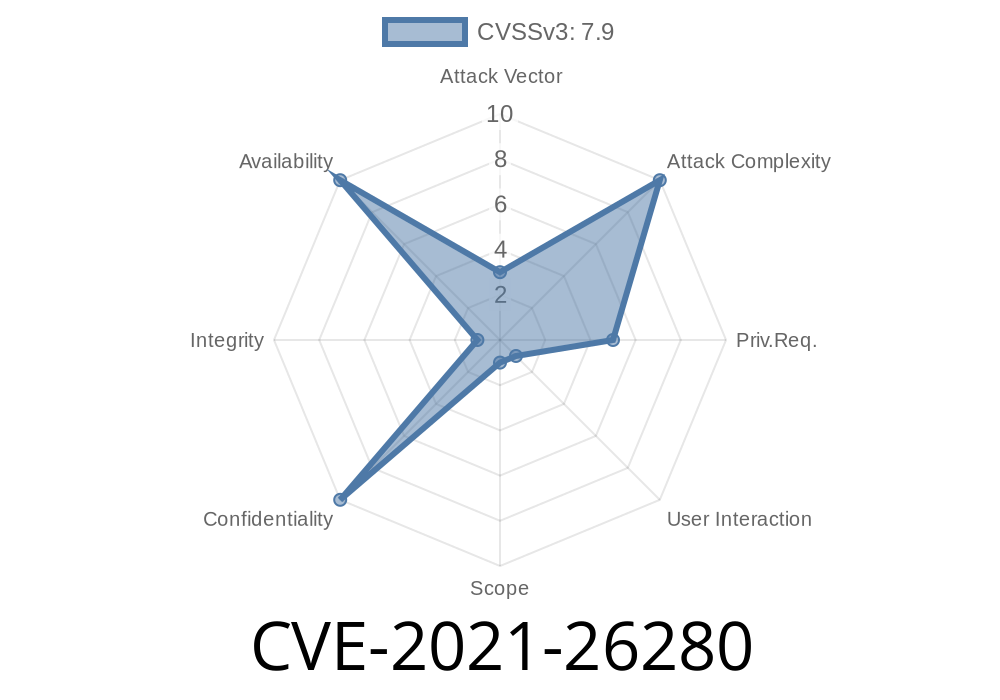
What Is CVE-2021-26280?
CVE-2021-26280 is a security vulnerability found in certain Windows environments. It lets a locally installed application bypass the normal permission checks and take actions—like changing system settings or accessing protected files—that it shouldn’t be able to touch.
In simple terms, a regular app gets the power of an administrator, without your consent.
A good starting point
How Does This Work?
Usually, when you install an app, it runs inside the limits set by Windows User Account Control (UAC) or similar systems. It can only touch what it's permitted to access. CVE-2021-26280 is a flaw in the permission-checking process—in effect, it forgets to ask, “Are you allowed to do this?”
This means a malicious or poorly coded app can directly access system operations meant for administrators or the system itself.
Exploit Details: A Step-by-Step Example
Let’s see how this flaw could be misused. Imagine we have an app running as a regular user, but due to the bug, it's able to start a service that usually requires admin privileges.
Here’s a simplified code snippet in Python (using the ctypes library to call Windows APIs). It tries to stop a system service, which usually isn’t allowed for normal users:
import ctypes
service_name = "wuauserv" # Windows Update
sc_manager = ctypes.windll.advapi32.OpenSCManagerW(None, None, xF003F)
if sc_manager:
service_handle = ctypes.windll.advapi32.OpenServiceW(sc_manager, service_name, xF01FF)
if service_handle:
result = ctypes.windll.advapi32.ControlService(service_handle, 1, None)
if result:
print("Service stopped successfully!")
else:
print("Failed to stop the service.")
ctypes.windll.advapi32.CloseServiceHandle(service_handle)
ctypes.windll.advapi32.CloseServiceHandle(sc_manager)
else:
print("Could not open Service Control Manager.")
Normally, this fails unless run as admin.
With CVE-2021-26280, it might succeed—letting any app control protected services.
Access or delete protected files
Basically, anything that normally needs "Run as Administrator."
Patches
The vendor was notified and quickly released a patch. Always apply your operating system’s security updates! Details:
- Vendor advisory (if available)
References
- NVD CVE-2021-26280
- Microsoft Security Update Guide
Summary
CVE-2021-26280 exposes just how important proper permission checks are. A seemingly normal app could, thanks to this bug, break free of its sandbox and change your computer—sometimes in dangerous ways. Your best defense is to stay patched and be careful what you install.
Timeline
Published on: 12/17/2024 07:15:05 UTC