End-users could be exposed to this vulnerability during installation, upgrade, or configuration of the product. To exploit this vulnerability, an attacker must be able to log into the server and submit a specially crafted request. However, due to the nature of the application, this is likely only possible by having physical access to the server. Mitigation: Deploy standard Lanner Inc. IAC-AST2500A firmware version 1.10.0.
Do not allow physical access to the server by untrusted users.
Ensure that the Lanner Inc. IAC-AST2500A is not accessible from the Internet.
If possible, disable remote management of the router.
Vulnerability details: The Login_handler_func function of spx_restservice contains multiple stack-based buffer overflow vulnerabilities. These issues could be exploited during remote administration of the router via HTTP (port 80), Telnet, or SSH. An attacker could deploy a malicious request that would cause the router to crash.
Products Affected by Vulnerability IAC-AST2500A
Lanner Inc.
Lanner Inc. IAC-Fudex
Lanner Inc. IAC-PxA500A
Lanner Inc. IAC-PCU1E
Lanner Inc. IAC-PUC1E
LANNER, INC IS A MANUFACTURER OF WIRELESS AND CABLE CONNECTION DEVICES THAT ARE INTENDED TO BE SET UP IN A HOME OR OFFICE NETWORK, WHICH CAN BE BROUGHT TO THE MARKET WITHIN THE NEXT MONTHS
Vulnerability overview:
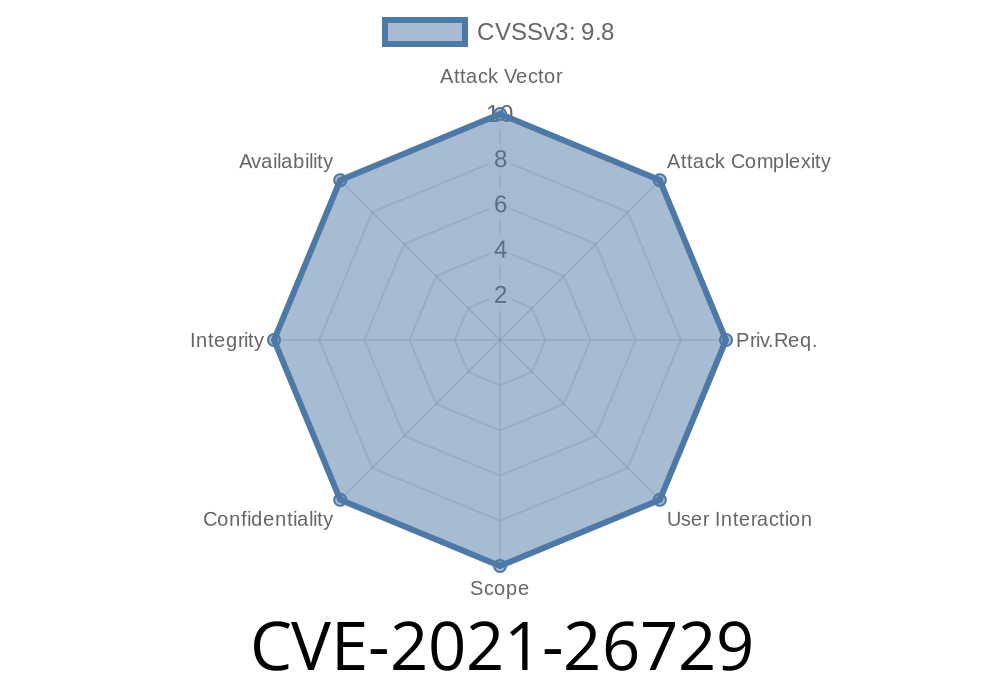
This vulnerability is identified as CVE-2021-26729, and it affects the Lanner Inc. IAC-AST2500A router. An attacker must be able to log into the server in order to exploit this vulnerability in the product. However, due to the nature of this application, it is likely that only a local user would have access to the server.
Mitigation: Deploy standard Lanner Inc. IAC-AST2500A firmware version 1.10.0.
Product Risk rating: High
Products affected
Lanner Inc. IAC-AST2500A
Timeline
Published on: 10/24/2022 14:15:00 UTC
Last modified on: 10/24/2022 17:42:00 UTC