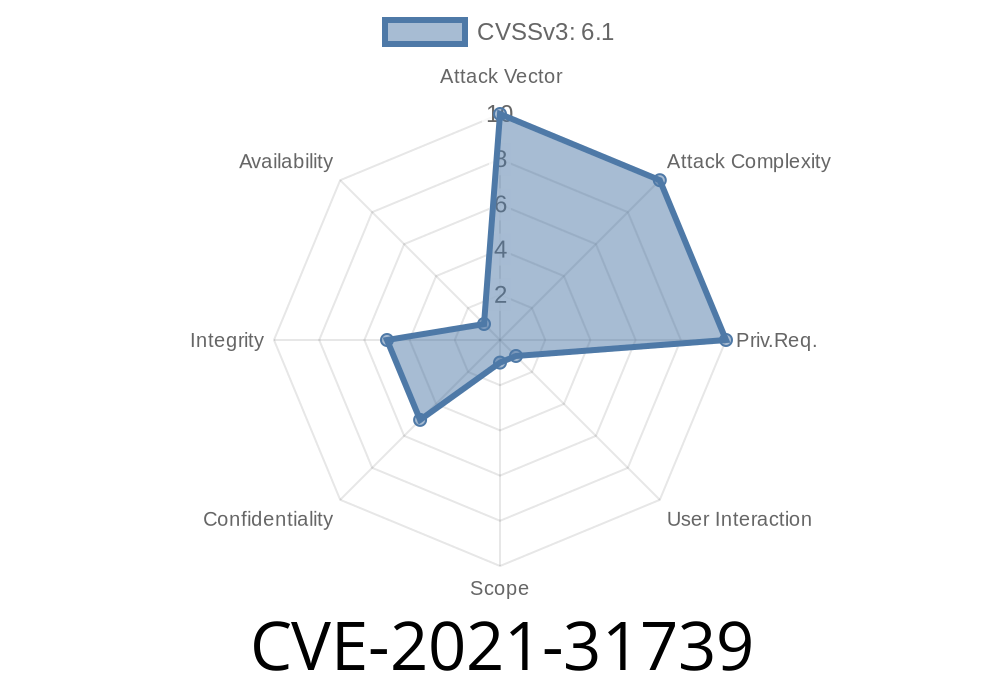
HTML tags are not filtered, and user input is not properly sanitized or encoded when sending an email message.
XSS can lead to a remote code execution attack. It can be exploited to steal sensitive information, modify system settings or launch phishing attacks. XSS can also be exploited by third parties, to conduct email spoofing attacks. There is no protection against XSS, when sending email messages. The only reliable solution for emailing is using a dedicated email server.
HTML Injection
Injection of HTML tags into email messages is a common vulnerability and the most serious risk to email users. Inclusion of these tags in emails allows attackers to execute custom JavaScript code on the victim’s device. If an attacker is able to successfully exploit this vulnerability, they have control of the victim’s computer and can also steal sensitive information.
The attack vectors for HTML injection include email attachment links, third-party web applications, links to file hosting services or online storage services, embedded images and media files, social media profile links and even links to the Microsoft Windows Live Messenger application. To reduce the risk of RCE attacks, users should only click on attachments that are known to be safe or use a dedicated email server that is not connected to any other networked systems.
How to protect your email from XSS?
For a sender to mitigate the risk of XSS, they should not directly input user-supplied data into an email message. For example, if a user enters their username in an email message and sends it from their personal account, attackers can try sending the same email from a different account. If the username is changed to "test" or "user", the email will be delivered without problems.
The following are some general recommendations for mitigating XSS attacks:
Allowing only authorized users to send emails
Removing unsafe HTML tags before sending
Ensure your business has a dedicated email server
CVE-2021-31741
HTML tags are not filtered, and user input is not properly sanitized or encoded when sending an email message.
This vulnerability can lead to a remote code execution attack. It can be exploited to steal sensitive information, modify system settings or launch phishing attacks. XSS can also be exploited by third parties, to conduct email spoofing attacks. There is no protection against XSS, when sending email messages. The only reliable solution for emailing is using a dedicated email server.
Timeline
Published on: 11/18/2022 23:15:00 UTC
Last modified on: 11/22/2022 20:44:00 UTC