This issue was addressed through improved input validation.
Improper authentication in subsystem for Intel(R) AMT before versions 11.8.93, 11.22.93, 11.12.93, 12.0.92, 14.1.67, 15.0.42, 16.1.25 may allow a privileged user to potentially enable escalation of privilege via remote access.
This issue was addressed through improved input validation.
Improper authentication in subsystem for Intel(R) AMT before versions 11.8.93, 11.22.93, 11.12.93, 12.0.92, 14.1.67, 15.0.42, 16.1.25 may allow a privileged user to potentially enable escalation of privilege via local access.
This issue was addressed through improved input validation.
Improper authentication in subsystem for Intel(R) AMT before versions 11.8.93, 11.22.93, 11.12.93, 12.0.92, 14.1.67, 15.0.42, 16.1.25 may allow a privileged user to potentially enable escalation of privilege via remote access.
This issue was addressed through improved input validation.
Improper authentication in subsystem for Intel(R) AMT before versions 11.8.93, 11.22.93, 11.12.93, 12.0.92, 14.
Credit: https://www.intel.com/content/www/us/en/security-center/advisories/cve-2021-33159.html
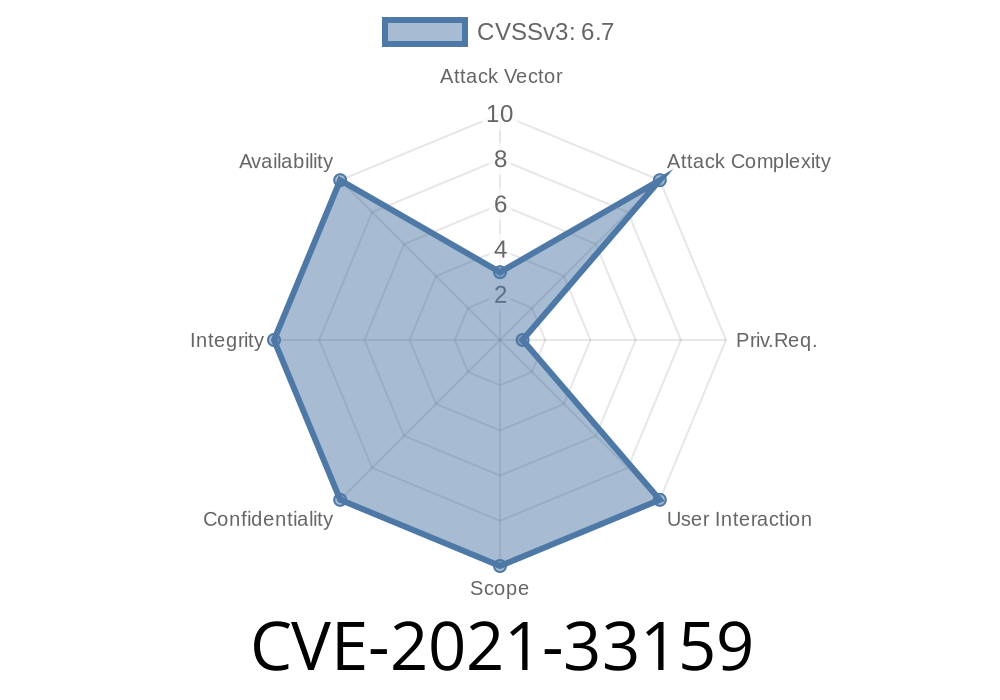
Improper input validation in subsystems for Intel(R) AMT before versions 11.8.93, 11.22.93, 11.12.93, 12.0.92, 14.1.67, 15.0.42, 16.1.25 may allow a privileged user to potentially enable escalation of privilege via remote access or local access
Cisco Nexus Switching Software and Process es
Input validation vulnerability in Cisco Nexus Switching Software and Processes could allow an unauthenticated, remote attacker to cause a denial of service (DoS) condition or crash the target system.
This issue was addressed through improved input validation.
Timeline
Published on: 11/11/2022 16:15:00 UTC
Last modified on: 11/17/2022 21:15:00 UTC