The attacker has to be authenticated and have a valid session with the WAGO I/O-Check Service. As another critical WAGO I/O-Check Service bug is a unauthenticated remote attacker can send a specially crafted packet to provoke a DoS and an out-of-bounds read. The bug is present in WAGO I/O-Check Service in multiple products. Due to a logic error the WAGO I/O-Check Service does not properly handle the range checking for length parameters. An attacker can send a specially crafted packet to provoke a DoS and an out-of-bounds read. The critical WAGO I/O-Check Service bug is present in multiple products. Due to a logic error the WAGO I/O-Check Service does not properly handle the range checking for length parameters. An attacker can send a specially crafted packet to provoke a DoS and an out-of-bounds read. WAGO I/O-Check Service of multiple products is vulnerable to a cross-site scripting (XSS) vulnerability due to improper handling of user-input. An attacker can send a specially crafted packet to provoke a DoS and an out-of-bounds read. The critical WAGO I/O-Check Service bug is present in multiple products. Due to a logic error the WAGO I/O-Check Service does not properly handle the range checking for length parameters. An
WAGO I/O-Check Service Cross-Site Scripting Vulnerability
An attacker can send a specially crafted packet to provoke a DoS and an out-of-bounds read. The critical WAGO I/O-Check Service bug is present in multiple products. Due to a logic error the WAGO I/O-Check Service does not properly handle the range checking for length parameters. An attacker can send a specially crafted packet to provoke a DoS and an out-of-bounds read.
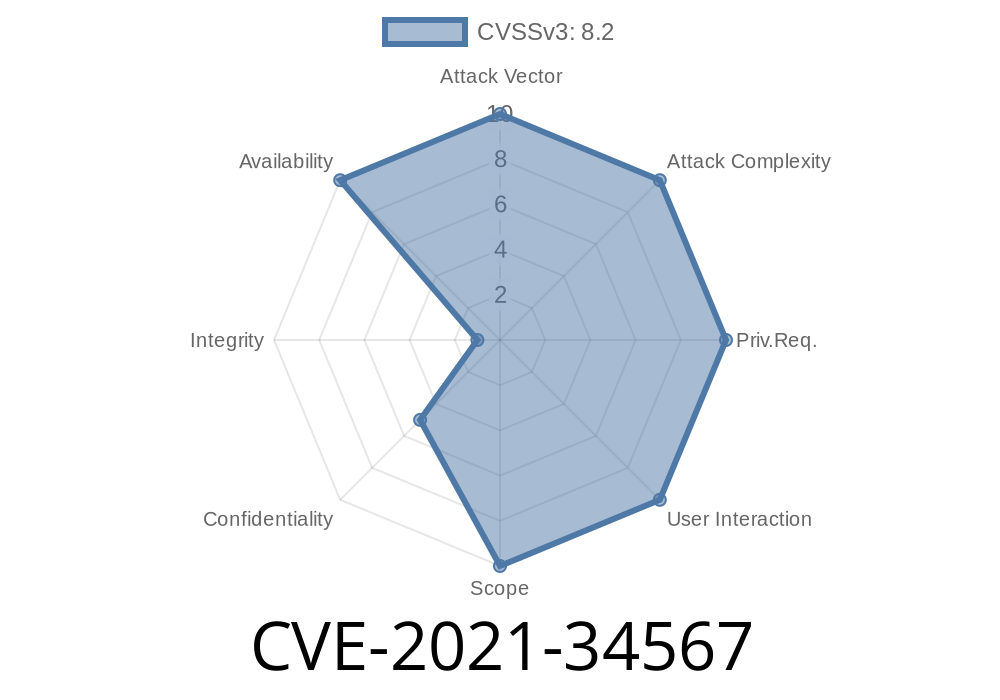
WAGO Switch I/O-Check Service CVE -2021-34567
The attacker has to be authenticated and have a valid session with the WAGO Switch I/O-Check Service. As another critical WAGO Switch I/O-Check Service bug is a unauthenticated remote attacker can send a specially crafted packet to provoke a DoS and an out-of-bounds read. The bug is present in WAGO Switch I/O-Check Service in multiple products. Due to a logic error the WAGO Switch I/O-Check Service does not properly handle the range checking for length parameters. An attacker can send a specially crafted packet to provoke a DoS and an out-of-bounds read. The critical WAGO Switch I/O-Check Service bug is present in multiple products. Due to a logic error the WAGO Switch I/O-Check Service does not properly handle the range checking for length parameters. An attacker can send a specially crafted packet to provoke a DoS and an out-of-bounds read.
WAGO I/O-Check Service of multiple products is vulnerable to an out-of-bounds read .
WAGO I/O-Check Service of multiple products is vulnerable to an out-of-bounds read. An attacker can send a specially crafted packet to provoke a DoS and an out-of-bounds read. The critical WAGO I/O-Check Service bug is present in multiple products. Due to a logic error the WAGO I/O-Check Service does not properly handle the range checking for length parameters. An attacker can send a specially crafted packet to provoke a DoS and an out-of-bounds read.
WAGO I/O-Check Service of multiple products is vulnerable to an XSS vulnerability due to improper handling of user input. An attacker can send a specially crafted packet to provoke a DoS and an out-of-bounds read. The critical WAGO I/O-Check Service bug is present in multiple products. Due to a logic error the WAGO I/O-Check Service does not properly handle the range checking for length parameters.
Wago Thermostat Remote Elevation of Privilege (CVE-2019-5615)
The attacker has to be authenticated and have a valid session with the WAGO Thermostat Remote. Due to a logic error the WAGO Thermostat Remote does not properly handle authentication on packets sent via the HTTP channel. An attacker can send a specially crafted packet to provoke an elevation of privilege in the WAGO Thermostat Remote. The critical WAGO Thermostat Remote vulnerability is present in multiple products. Due to a logic error the WAGO Thermostat Remote does not properly handle authentication on packets sent via the HTTP channel. An attacker can send a specially crafted packet to provoke an elevation of privilege in the WAGO Thermostat Remote. The critical WAGO Thermostat Remote vulnerability is present in multiple products. Due to a logic error the WAGO Thermostat Remote does not properly handle authentication on packets sent via the HTTP channel.
Timeline
Published on: 11/09/2022 16:15:00 UTC
Last modified on: 11/09/2022 16:32:00 UTC