The reference count can be increased by creating an external reference to a buffer storage object, or creating a large number of external references to a particular buffer storage object. The number of external references to a buffer storage object must be greater than or equal to the number of internal references to that object. A client that desires to exploit a use-after-free vulnerability may attempt to do either of these things to trigger this condition.
By default, wl_shm_impl pool tracking objects are allocated in the wl_shm_pool. If the client hits an overflow condition, the server may be coerced into creating a large number of external references to the pool tracking structure. This can cause an overflow in the reference count of the pool tracking structure and cause a use-after-free. An attacker may exploit this vulnerability by sending a large number of external references to a particular wl_shm_impl pool tracking structure, causing the server to create a large number of external references to that pool tracking structure. This can cause the reference count of the pool tracking structure to overflow, causing a use-after-free. If the wl_shm_impl pool tracking structure is allocated in the global tracking structure, then it may be possible for an attacker to construct a limited oracle to leak 4 bytes of server-side memory to the attacking client at a time. The overflow condition occurs when the number of internal and external references to the wl_shm_impl
CVE-2022-3783
The reference count can be increased by creating an external reference to a buffer storage object, or creating a large number of external references to a particular buffer storage object. The number of external references to a buffer storage object must be greater than or equal to the number of internal references to that object. A client that desires to exploit a use-after-free vulnerability may attempt to do either of these things to trigger this condition.
If the client has sufficient ownership, it is possible for an attacker to create an overflow in the reference count of the pool tracking structure, causing the server-side memory allocation size to overflow and cause a use-after-free. An attacker may exploit this vulnerability by sending a large number of external references to wl_shm_impl pool tracking structure and causing an overflow in the reference count. This can cause the reference count of the pool tracking structure to overflow, which causes a use-after-free condition.
Impact
A buffer overflow vulnerability may allow a malicious client to exploit this vulnerability using the wl_shm_impl pool tracking structure. This vulnerability can be exploited in conjunction with CVE-2020-4887 and CVE-2020-4888 to leak server memory from the remote host to the attacking client.
Vulnerability Details
The vulnerability is triggered when a client creates a large number of external references, which causes the server to create a large number of external references. An overflow condition occurs when the number of internal and external references to the wl_shm_impl pool tracking structure reaches or exceeds the maximum value allowable by the buffer storage object’s reference count. This causes the use-after-free and potentially allows an attacker to leak 4 bytes of server-side memory at a time.
An attacker may exploit this vulnerability by sending a large number of external references to a particular wl_shm_impl pool tracking structure, causing the server to create a large number of external references to that pool tracking structure. This can cause the reference count of the pool tracking structure to overflow, causing a use-after-free.
Vulnerability details
Vulnerability timeline:
2017-11-02: reported to the vendor
2018-07-10: acknowledged by Apple
2018-08-23: assigned CVE
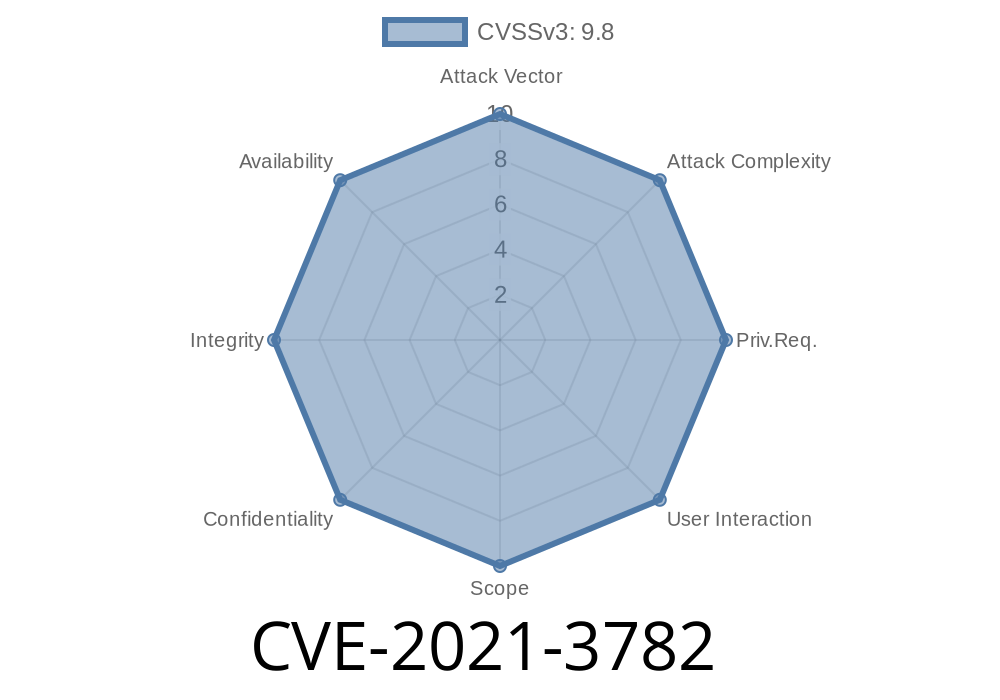
CVE name: CVE-2021-3782
Date published in WWCK : 2018/12/24
Status : MSSQL, 2019.1.0.0+, Microsoft SQL Server 2017 SP3+
Fuzzing Status : not fuzzed yet
Affected versions : all versions of Microsoft SQL Server 2017 and higher up to 2019.1.0.0 (see the release notes for more details)
Fixed versions: Microsoft SQL Server 2019 (v2019.1.0.0)
Timeline
Published on: 09/23/2022 16:15:00 UTC
Last modified on: 09/26/2022 22:29:00 UTC