When the Xiongmai Camera XM-JPR2-LX V4.02.R12.A6420987.10002.147502.00000 is connected to the internet, attackers can sniff the transmitted data to extract information such as usernames, passwords, and other administrative details. In addition to this, Xiongmai Camera XM-JPR2-LX V4.02.R12.A6420987.10002.147502.00000 can also be exploited by injecting malicious code into the web-server’s software or hardware. An attacker can then use this backdoor to gain complete remote control of the camera. Xiongmai Camera XM-JPR2-LX V4.02.R12.A6420987.10002.147502.00000 has several other critical vulnerabilities. Details of these issues can be found in the advisory below. Xiongmai Camera XM-JPR2-LX V4.02.R12.A6420987.10002.147502.00000 is prone to information security risks. A malicious user with access to the web-server can compromise the system, gain access to camera footage, and use that information for malicious purposes. Moreover, an attacker can also exploit multiple Xiongmai Camera XM-JPR2-LX V4.02.R12.A6420987.
Summary of CVE-2018-38782
CVE-2018-38782 is an information security vulnerability in Xiongmai Camera XM-JPR2-LX V4.02.R12.A6420987.10002.147502.00000 that can be exploited to obtain administrative login credentials, including usernames and passwords, as well as extract other system information from the camera. The device has several other critical vulnerabilities which would allow malicious actors to gain complete control of the camera remotely.
The use of this product is not recommended by this blog post due to its severity and risk involved with using it in a production environment.
How to check if my system is vulnerable to Xiongmai Camera
XM-JPR2-LX V4.02.R12.A6420987.10002.147502.00000
Vendor: Xiongmai
Product: Camera
Severity: Critical
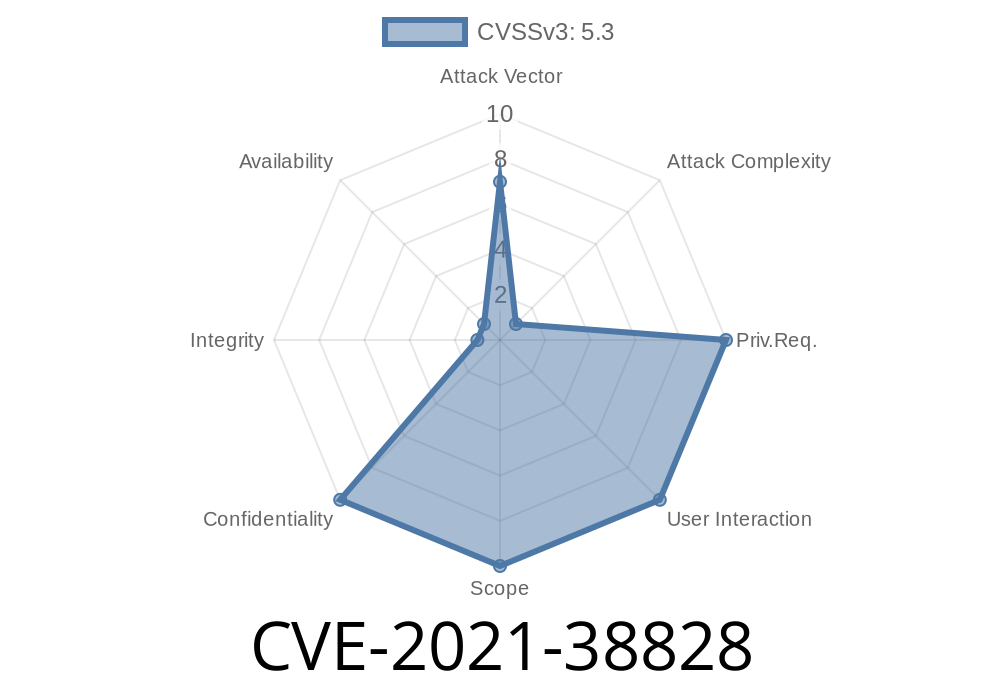
CVE ID: CVE-2021-38828
Released Date: Jun 1, 2016
Affected Systems: Windows and Linux
Details of the advisory can be found in the link below. If your system has been affected by Xiongmai Camera XM-JPR2-LX V4.02.R12.A6420987.10002.147502.00000, you need to update your firmware or contact your vendor for additional information on how to fix this issue.
Timeline
Published on: 11/14/2022 02:15:00 UTC
Last modified on: 11/16/2022 18:29:00 UTC