An attacker can leverage this weakness to decrypt or alter data. Red Hat Ceph Storage is prone to a key length validation flaw, which can be exploited by an attacker to decrypt or alter data. Red Hat Ceph Storage does not validate the key length when generating encryption keys. An attacker with knowledge of this flaw can exploit it to generate a key with a length that is below that required for the encryption algorithm. As a result, the encryption key generated by Red Hat Ceph Storage is not as strong as it should be. This issues can be exploited by an attacker to decrypt or alter data in Red Hat Ceph Storage by using a key with a length that is below that required for the cipher used.
Weak Key Length Validation
Validation of the key length is not performed when generating encryption keys. As a result, an attacker can generate a key with a length that is below that required for the encryption algorithm. This allows an attacker to decrypt or alter data in Red Hat Ceph Storage by using a key with a length that is below that required for the cipher used.
Vulnerability Symptoms and How to Avoid Becoming a Victim
The issue can be exploited by an attacker who has knowledge of this flaw.
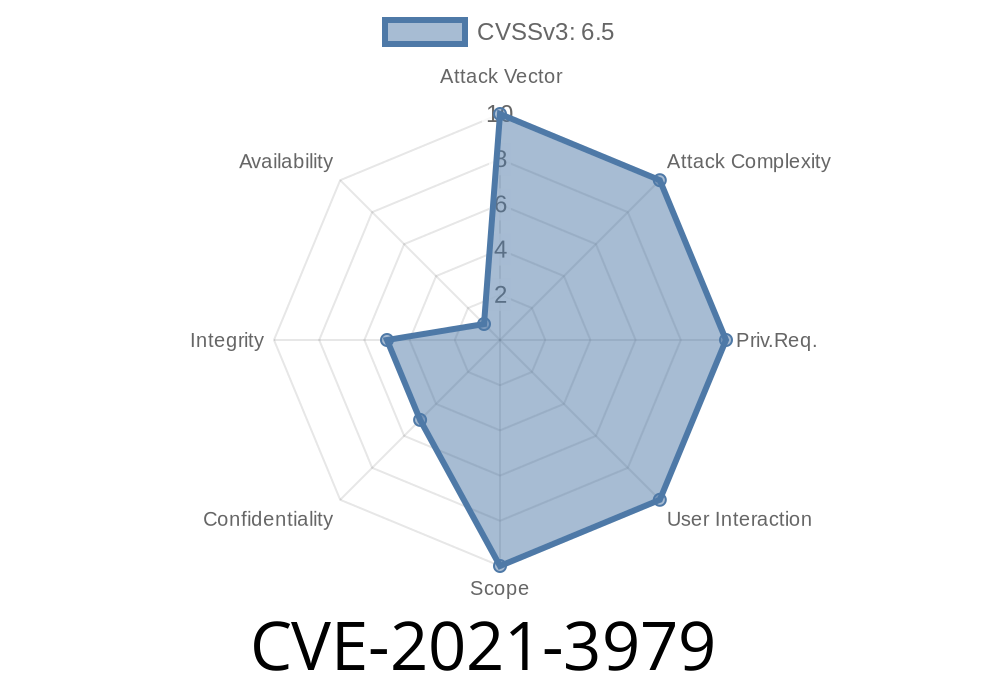
If you want to avoid becoming a victim, make sure your cluster is secure and patched against CVE-2021-3979.
Weaknesses in Network Setup
Red Hat Ceph Storage has a weakness in the network setup, which allows an attacker to view and modify data in Red Hat Ceph Storage. The weakness is due to insufficient filtering of IP packets that contain non-printable characters. As a result, an attacker with knowledge of this flaw can exploit it to view and modify data on Red Hat Ceph Storage. This vulnerability can be exploited by an attacker who successfully sends malicious packets to Red Hat Ceph Storage to view or modify data without authorization.
Red Hat's flagship open source storage product, the Red Hat Ceph Storage solution provides enterprise class storage for clusters of application servers running Red Hat Enterprise Linux or other Linux distributions such as CentOS, Scientific Linux, and Ubuntu.
The key length validation flaw in Red Hat Ceph Storage enables attackers with knowledge of the flaw to decrypt or alter data in the affected system. To mitigate this risk, Red Hat recommends disabling SSLv3 and retiring any SSLv3 enabled components from systems running Red Hat Ceph Storage
Vulnerability Scenario
An attacker can leverage this vulnerability to decrypt or alter data. Red Hat Ceph Storage is prone to a key length validation flaw, which can be exploited by an attacker to decrypt or alter data. Red Hat Ceph Storage does not validate the key length when generating encryption keys. An attacker with knowledge of this flaw can exploit it to generate a key with a length that is below that required for the encryption algorithm. As a result, the encryption key generated by Red Hat Ceph Storage is not as strong as it should be. This issues can be exploited by an attacker to decrypt or alter data in Red Hat Ceph Storage by using a key with a length that is below that required for the cipher used.
Timeline
Published on: 08/25/2022 20:15:00 UTC
Last modified on: 08/31/2022 14:42:00 UTC
References
- https://access.redhat.com/security/cve/CVE-2021-3979
- https://tracker.ceph.com/issues/54006
- https://github.com/ceph/ceph/pull/44765
- https://github.com/ceph/ceph/commit/47c33179f9a15ae95cc1579a421be89378602656
- https://bugzilla.redhat.com/show_bug.cgi?id=2024788
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2021-3979