A race condition was found in gethostbyname() when the return value from a DNS query is checked with the end of the DNS response not yet received. A remote attacker could exploit this flaw to cause applications using gethostbyname() to crash.
This issue does not pose a threat in normal system configurations since gethostbyname() is normally only called by locally installed applications. However, it is still recommended to update your system with the latest update. As a precaution, you can avoid running setuid programs as root. A bug was found in the libnss_dns code of glibc. An attacker could potentially enter a loop with incorrect DNS resolution, causing applications using the libnss_dns code of glibc to crash. As a precaution, you should update your libnss_dns package. An integer overflow flaw was found in the libnss_files code of glibc. An attacker could potentially create a malicious file that would cause applications using libnss_files to crash. As a precaution, you should update your libnss_files package. An integer overflow flaw was found in the gethostbyname() function in glibc. An attacker could potentially create a malicious DNS response that would cause applications using the gethostbyname() function of glibc to crash. As a precaution, you should update your gethostbyname() package. An integer underflow flaw was found in the gethostby
Check if you are affected by CVE-2021-4000
, CVE-2021-4999
A buffer overflow flaw was found in the nss_dns code of glibc. An attacker could potentially create a malicious DNS response that would cause applications using the nss_dns function of glibc to crash. As a precaution, you should update your nss_dns package. A buffer overflow flaw was found in libnss_files code of glibc. An attacker could potentially create a malicious file that would cause applications using libnss_files to crash. As a precaution, you should update your libnss_files package. A buffer overflow flaw was found in the gethostbyname() function in glibc. An attacker could potentially create a malicious DNS response that would cause applications using the gethostbyname() function of glibc to crash. As a precaution, you should update your gethostbyname() package. A buffer overflow flaw was found in the gethostbyname() function in glibc. An attacker could potentially create a malicious DNS response that would cause applications using the gethostbyname() function of glibc to crash. As a precaution, you should update your gethostbyname() package.
Check for installed packages
If you are not sure whether your system is vulnerable, you should update your system with the latest update.
MySQL
An integer overflow flaw was found in the mysql_real_escape_string() function of MySQL. An attacker could potentially create a malicious string that would cause applications using mysql_real_escape_string() to crash. As a precaution, you should update your mysql-preferred package.
What is Libvirt?
Libvirt is a toolkit to enable and automate the management of virtualized systems. It provides an interface for managing different hardware types, including x86, AMD64, IBM POWER, ARM, IBM zSeries and s390x systems.
Timeline
Published on: 08/24/2022 16:15:00 UTC
Last modified on: 08/29/2022 15:23:00 UTC
References
- https://www.openwall.com/lists/oss-security/2022/01/24/4
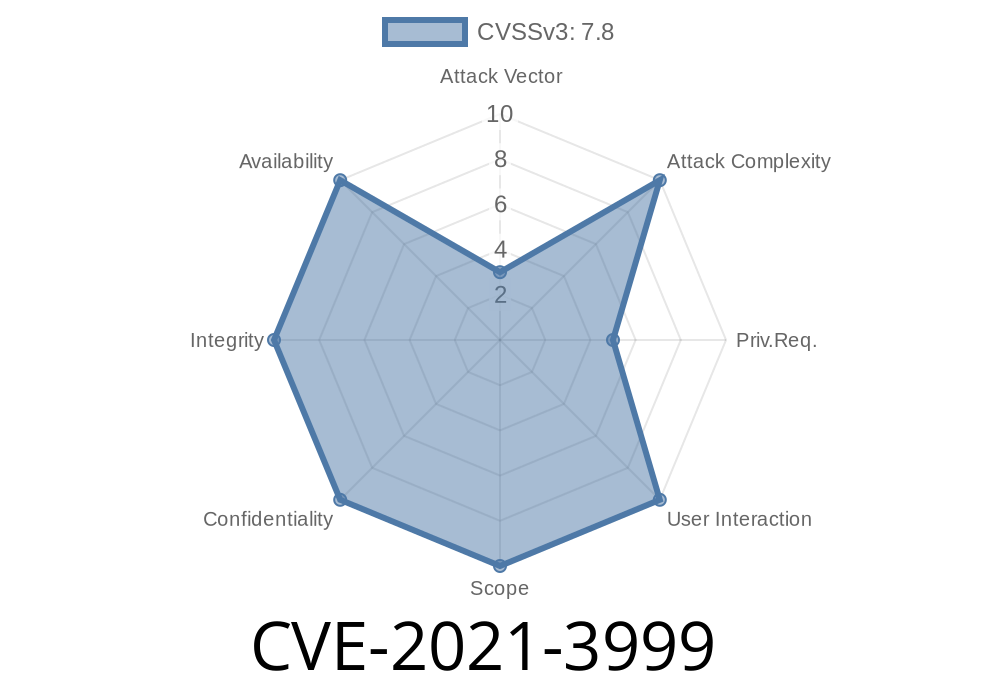
- https://access.redhat.com/security/cve/CVE-2021-3999
- https://sourceware.org/git/gitweb.cgi?p=glibc.git;h=23e0e8f5f1fb5ed150253d986ecccdc90c2dcd5e
- https://sourceware.org/bugzilla/show_bug.cgi?id=28769
- https://security-tracker.debian.org/tracker/CVE-2021-3999
- https://bugzilla.redhat.com/show_bug.cgi?id=2024637
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2021-3999