It is highly recommended to upgrade immediately. Log statements with no escaping can be used to inject external script code into the application, leading to a wide range of potential attacks. For example, an un-escaped single line log statement such as 'click here' can be used to inject arbitrary script code into the application. Any application that accepts un-escaped log statements as input is vulnerable to injection attacks. In the context of Heron, log statements can be used to write data to a log file or to a database. If an application does not validate the source of data before storing it in a data source, an attacker can inject arbitrary data into the application's data source. For example, an attacker can send an un-escaped log statement such as ‘EVAL 'CODE'’ to a Heron application to launch an external program on the Heron node.
Vulnerability Details
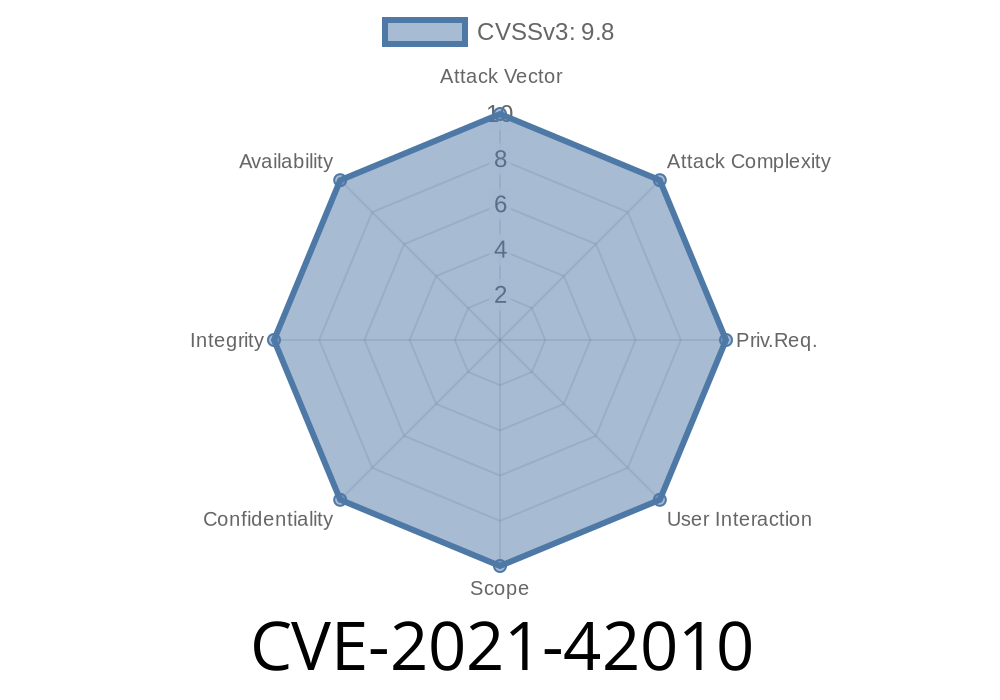
Heron is vulnerable to a wide range of attacks. Injection attacks allow attackers to inject arbitrary script code into the application, resulting in remote code execution.
Heron also contains an exploitable flaw in its log statements that allows remote code execution. The issue lies in the lack of escaping for single line log statements on Heron, meaning that any input containing a single un-escaped log statement can be used to write data to an external file or database.
References:
1. https://docs.heronplatform.com/reference/CVE-2021-42010
Timeline
Published on: 10/24/2022 14:15:00 UTC
Last modified on: 10/24/2022 18:24:00 UTC