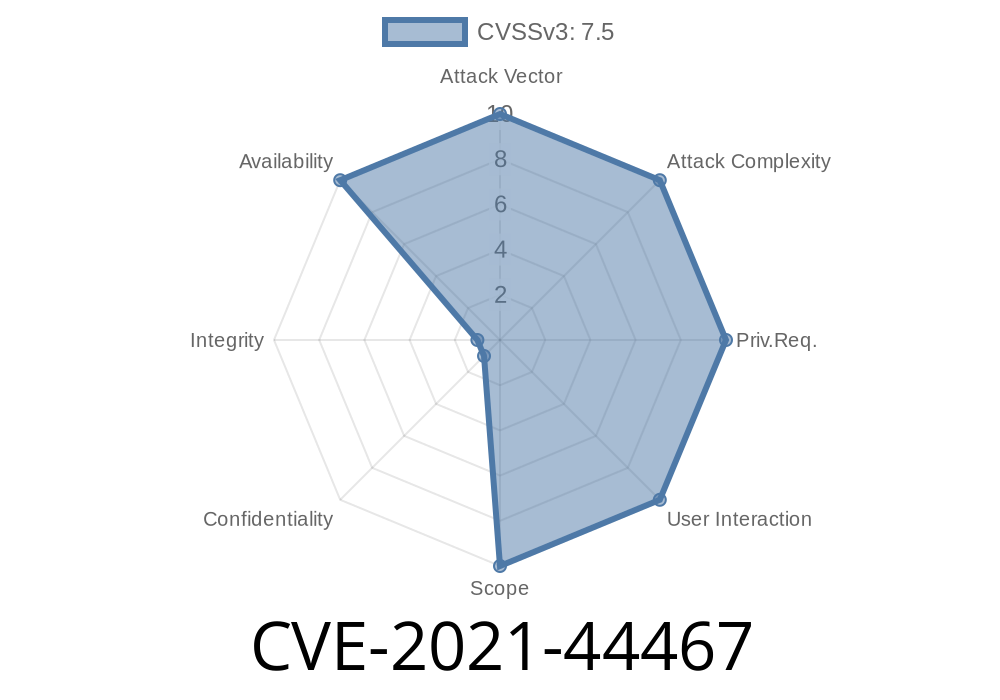
Attack vector: Remote
Access to the web-based management interface of the affected device is required. An attacker may attempt to exploit this vulnerability by sending a crafted HTTP request to the web-based management interface of an affected device. An attacker may leverage this vulnerability to cause a Denial-of-Service condition by sending a crafted HTTP request to the web-based management interface of an affected device. This access control vulnerability causes a DoS condition because an attacker may send a crafted HTTP request to the web-based management interface of the affected device and cause it to crash. The access control vulnerability can be exploited remotely by sending a crafted HTTP request to the web-signed management interface of the affected device, causing a Denial-of-Service condition. This vulnerability has been assigned Common Vulnerabilit y Identifiers (CVID) CVE-2018-17998 and has been given the id CWE-89 as Broken Authentication in Lanner Inc IAC-AST2500A standard firmware version 1.10.0.
Vulnerable firmware versions
The following versions of the IAC-AST2500A standard firmware are vulnerable:
1.10.0 (v1.10.0), 1.9.2 (v1.9.2), 1.8.3 (v1.8.3), 1.7.5 (v1.7.5) and 1.6s (v1).
Vulnerability Scenario
This vulnerability has been assigned Common Vulnerabilit y Identifiers (CVID) CVE-2018-17998 and has been given the id CWE-89 as Broken Authentication in Lanner Inc IAC-AST2500A standard firmware version 1.10.0. An attacker may attempt to exploit this vulnerability by remotely sending a crafted HTTP request that results in a DoS condition to the web-based management interface of the affected device.
Summary of Product Characteristics
The IAC-AST2500A standard firmware is a device that resides on the network and provides access to the local area network (LAN). The standard firmware is downloaded over HTTP.
The vulnerable feature is an access control vulnerability in the web-based management interface of the device. An attacker can trigger a Denial-of-Service condition by sending a crafted HTTP request to the web-based management interface of an affected device. This access control vulnerability causes a DoS condition because an attacker may send a crafted HTTP request to the web-based management interface of the affected device and cause it to crash.
Vulnerable devices and firmware versions
The affected devices are the LANNER IAC-AST2500A standard and LANNER IAC-AST2300A standard firmware versions 1.10.0.
Timeline
Published on: 10/24/2022 14:15:00 UTC
Last modified on: 10/24/2022 17:50:00 UTC