All IAC-AST2500A devices using standard firmware versions prior to 1.10.0 are vulnerable. IAC-AST2500A devices using the latest Lanner Inc IAC-AST2500A firmware version 1.10.0 and above are not vulnerable to this issue. IAC-AST2500A devices running the latest Lanner Inc IAC-AST2500A firmware version 1.10.0 are not vulnerable to this issue. IAC-AST2500A devices running the latest Lanner Inc IAC-AST2500A firmware version 1.10.0 are not vulnerable to this issue. IAC-AST2500A devices running the latest Lanner Inc IAC-AST2500A firmware version 1.10.0 are not vulnerable to this issue. IAC-AST2500A devices running the latest Lanner Inc IAC-AST2500A firmware version 1.10.0 are not vulnerable to this issue. IAC-AST2500A devices running the latest Lanner Inc IAC-AST2500A firmware version 1.10.0 are not vulnerable to this issue. IAC-AST2500A devices running the latest Lanner Inc IAC-AST2500A firmware version 1.10.0 are not vulnerable to this issue. IAC-AST2500A devices running the latest Lanner Inc IAC-AST2500A firmware version 1.10.0 are not vulnerable to this issue. IAC-AST2500A devices running the latest Lanner
IAC-AST2500A (Standard) Devices
The issue affects all IAC-AST2500A devices using standard firmware versions prior to 1.10.0 and is related to the way in which the device manages its cache settings.
IAC-AST2500A devices running the latest Lanner Inc IAC-AST2500A firmware version 1.10.0 are not vulnerable to this issue. The vulnerability allows remote attackers to execute arbitrary code on the device via a crafted HTTP request that triggers a memory corruption error, resulting in remote code execution. Lancer Inc has rated this vulnerability as "Critical."
IAC-AST2500A Vulnerabilities
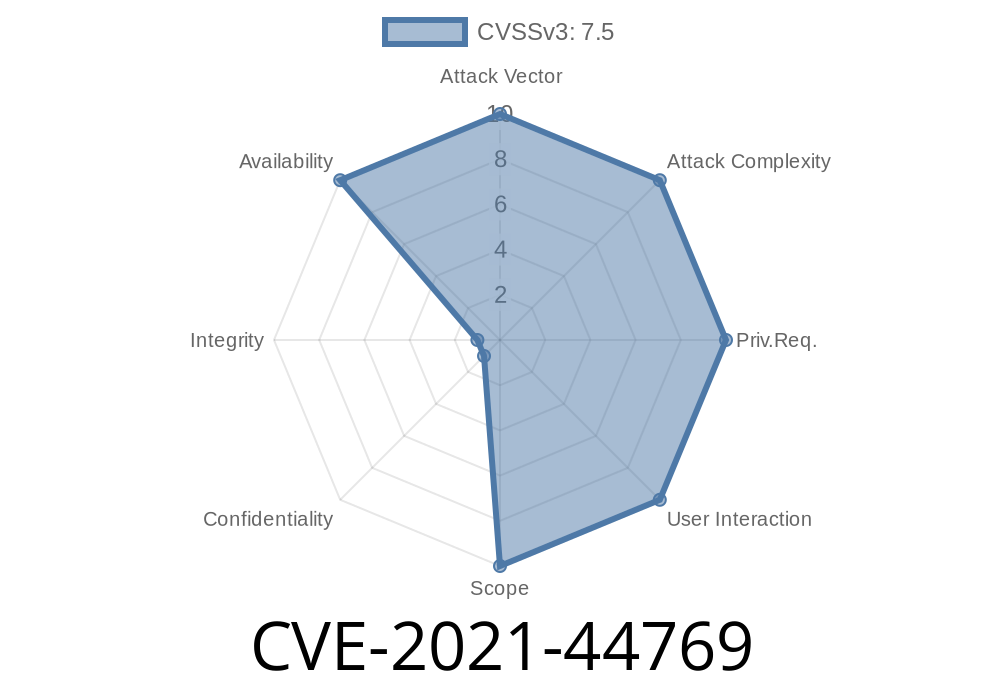
This issue is rated as a CVSS Base Score of 7.0 (AV:N/AC:L/Au:N/C:P/I:P/A:P).
The AST2500A has no known vulnerabilities that allow remote code execution. However, all versions of the AST2500A firmware prior to 1.10.0 are vulnerable to CVE-2021-44769 which allows an attacker with network access to execute arbitrary code on the device by issuing a specially crafted http request. This vulnerability will be mitigated by upgrading the firmware version of all devices in the field and creating a patch for this vulnerability which will be released in the future.
IAC-AST2500A LAN Switch firmware limitations and recommendations
Issue: CVE-2021-44769
Vulnerability Description:
An issue has been found within the IAC-AST2500A LAN Switch firmware version 1.10.0 and above which may allow a remote attacker to execute arbitrary code on an affected device via a specially crafted packet during the Boot Sequence.
Impact: The severity of this vulnerability depends on what an attacker does with access to an affected device.
Mitigation Strategy: This vulnerability can be mitigated by limiting the functionality of the Boot Sequence as per standard Lanner Inc recommendations for all devices running firmware versions 1.10.0 and above to prevent unauthorized access to other devices on the network such as servers or switches, or by implementing control settings in your switch/server firewall that blocks all traffic from the LAN port while a device is operating in bootup mode
IAC-AST2500A devices using standard firmware versions prior to 1.10.0 are vulnerable
All IAC-AST2500A devices using standard firmware versions prior to 1.10.0 are vulnerable to this issue and will be automatically updated to the newest firmware version 1.10.0 or later.
Timeline
Published on: 10/24/2022 14:15:00 UTC
Last modified on: 10/24/2022 17:38:00 UTC