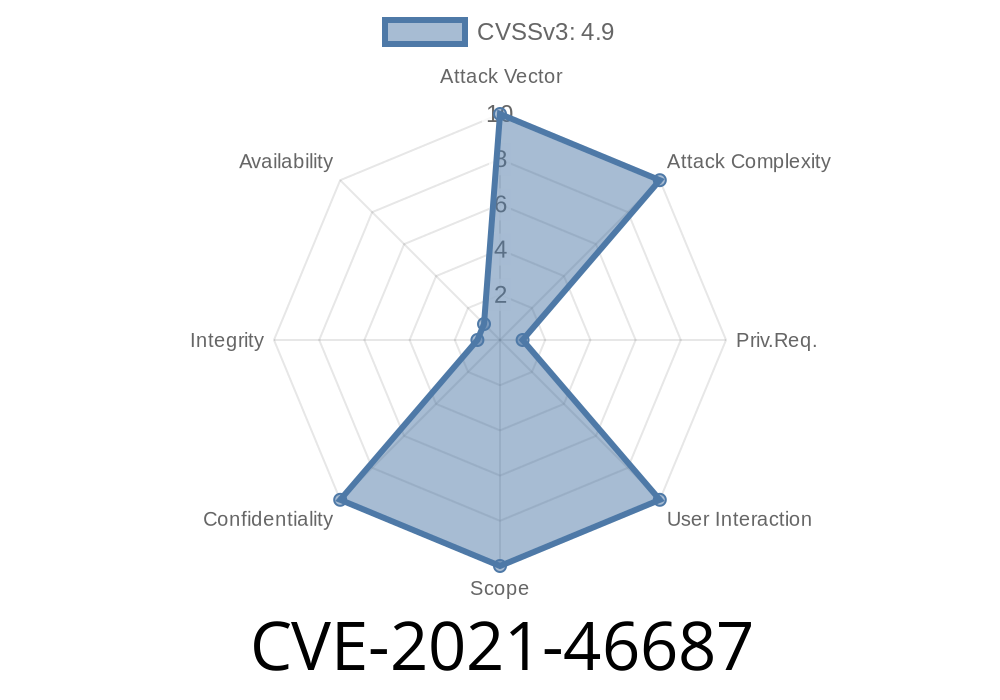
The REST API for the Project Administrator interface in JFrog Artifactory allows unauthenticated access, resulting in potential information leaks. An attacker can craft a URL to access this interface, and can then retrieve information that is typically only available to the system administrator. In some cases, the attacker can even change the settings of the project to which they have access, making it easier to exploit. The information that can be leaked through this interface includes the project name, project description, license, and project URL. This issue affects: JFrog JFrog Artifactory JFrog Artifactory versions before 7.31.10 versions prior to 7.x; JFrog Artifactory versions before 6.23.38 versions prior to 6.x. An attacker can exploit this issue to obtain information such as the project name, project description, and license information that is typically only available to the system administrator. An attacker can also change the settings of the project to which they have access, making it easier to exploit.
Vulnerability Details
The Project Administrator interface in JFrog Artifactory exposes a REST API that is not protected with authentication. This API can be accessed through an unauthenticated URL, and allows the retrieval of information that is typically only available to the system administrator. The information that can be leaked through this interface includes project name, project description, license and project URL. The issue affects: JFrog JFrog Artifactory versions before 7.31.10 versions prior to 7.x; JFrog Artifactory versions before 6.23.38 versions prior to 6.x. An attacker can exploit this issue by crafting a URL to access the REST API for the Project Administrator interface in JFrog Artifactory, and then retrieving information such as the project name, Description, and License along with URL from these exposed resources without authentication.
Overview of the Issue
CVE-2021-46687 is a vulnerability in the REST API for JFrog Artifactory. This issue affects JFrog JFrog Artifactory versions before 7.31.10 versions prior to 7.x and JFrog Artifactory versions before 6.23.38 versions prior to 6.x and allows an attacker to exploit the vulnerability by accessing information such as the project name, project description, and license information that is typically only available to the system administrator. An attacker can also change settings for the project that they have access to, making it easier to exploit.
The REST API for the Project Update interface in JFrog Artifactory allows unauthenticated access
, resulting in potential information leaks. An attacker can craft a URL to access this interface, and can then retrieve information that is typically only available to the system administrator. In some cases, the attacker can even change the settings of the project to which they have access, making it easier to exploit. The information that can be leaked through this interface includes the project name, project description, license, and project URL. This issue affects: JFrog Artifactory versions prior 7.x
An attacker can exploit this issue to obtain information such as the project name, project description, and license information that is typically only available to the system administrator. An attacker can also change the settings of the project to which they have access, making it easier to exploit.
How to check if you are vulnerable?
A JFrog Artifactory version prior to 6.23.38 is vulnerable to CVE-2021-46687.
To check if you are running a vulnerable version of Artifactory, use the following command:
docker info | grep -i jfrog-artifactory
You will see something similar to this:
"jfrog/jfrog-artifactory": "7.x"
If you do not see the word "7.x", you are not vulnerable.
Timeline
Published on: 07/06/2022 10:15:00 UTC
Last modified on: 07/13/2022 14:30:00 UTC