The information disclosure vulnerability exists due to the fact that the input data to the WLAN module is not sanitized before being provided to the application. Data which is supposed to be hidden from the user (such as password), may be revealed due to this issue. It is recommended to implement input sanitizing functions to prevent information disclosure. It is also recommended to limit access to the WLAN module to only those users who have a legitimate need to access this functionality. Limiting access to the WLAN module reduces the impact of this vulnerability.
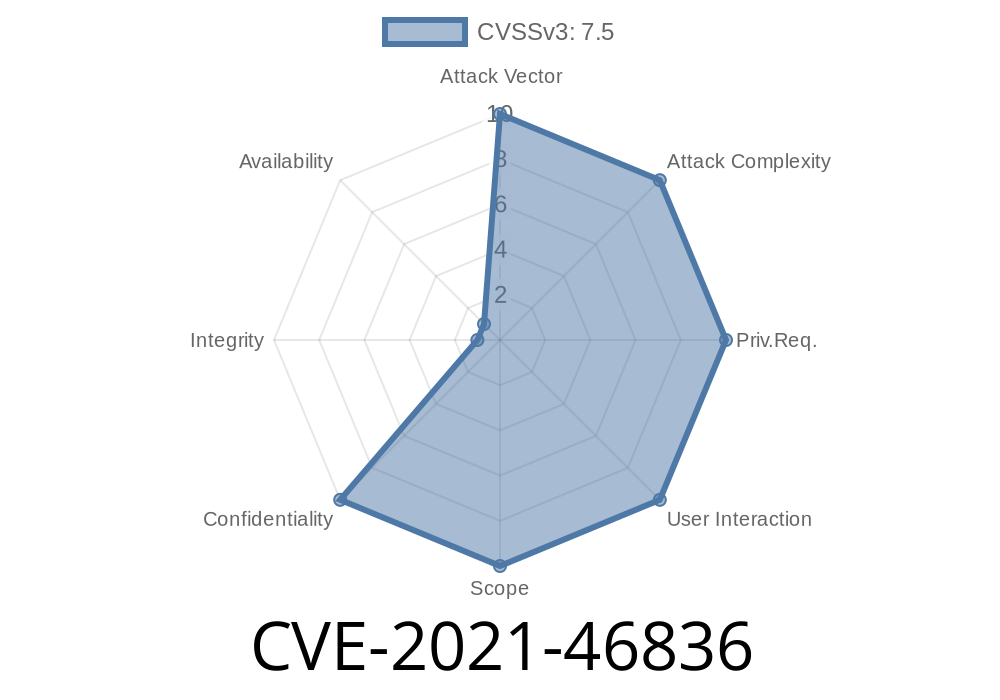
Overview: CVE-2021-46836
A vulnerability was discovered in the firmware of a product running on a WLAN module. This product is used in various commercial and industrial equipment, such as in amusement machines, cash registers, and other types of devices. The vulnerability exists due to the fact that the input data to the WLAN module is not sanitized before being provided to the application. Data which is supposed to be hidden from a user (such as password), may be revealed due to this issue. It is recommended to implement input sanitizing functions to prevent information disclosure. It is also recommended to limit access to the WLAN module to only those users who have a legitimate need to access this functionality. Limiting access to the WLAN module reduces the impact of this vulnerability.
Vulnerability Overview
The vulnerability in question is an information disclosure vulnerability. It exists due to the fact that the input data to the WLAN module is not sanitized before being provided to the application. Data which is supposed to be hidden from the user (such as password), may be revealed due to this issue. It is recommended to implement input sanitizing functions to prevent information disclosure. It is also recommended to limit access to the WLAN module to only those users who have a legitimate need to access this functionality. Limiting access to the WLAN module reduces the impact of this vulnerability
Overview of the Vulnerability
A vulnerability in the WLAN module of the product allows for information disclosure. The input data to the WLAN module is not sanitized before being provided to the application, meaning that hidden data such as password may be revealed due to this issue. It is recommended that input sanitizing functions are implemented in order to prevent this vulnerability from occurring. It is also recommended that access to the WLAN module is limited to only those users who have a legitimate need to access this functionality. This will reduce the impact of this vulnerability.
Vulnerability Scenario
A vulnerability exists in the WLAN module of an embedded device. The vulnerability is caused by improper sanitization of input data. This may lead to information disclosure if this input data is provided to a malicious application on the device.
If the device is accessible via its LAN interface, it is recommended to limit access to the WLAN module only for those users who have a legitimate need. This will reduce the impact of this vulnerability.
Timeline
Published on: 09/16/2022 18:15:00 UTC
Last modified on: 09/20/2022 16:56:00 UTC