and we urge you to update your PAN-OS software immediately to prevent this configuration from being misused. Given the short time from discovery to release of the fix in PAN-OS, we have been made aware of a number of firewall manufacturers who are delaying or even blocking the installation of the fix from their software updates. We have been made aware of at least one firewall manufacturer who is advising customers to delay installing the security fix for a period of 30 days. The vendor of this firewall is advising customers to upgrade to an “Unified Endpoint Management” solution to ensure that the installation of the fix can go ahead.
PAN-OS Networking Security Principles
PAN-OS networking security principles help ensure that PAN-OS is secure to the network, and that traffic can flow securely between all devices in the network.
In order to maintain end-to-end security for a device, it is key that the device uses a VPN connection or an IPSec connection.
A device must have a firewall software implementation in order to be configured with traffic control rules.
A VPN technology implementation should be used on the internal interface of a device that is not configured as an IPSec endpoint.
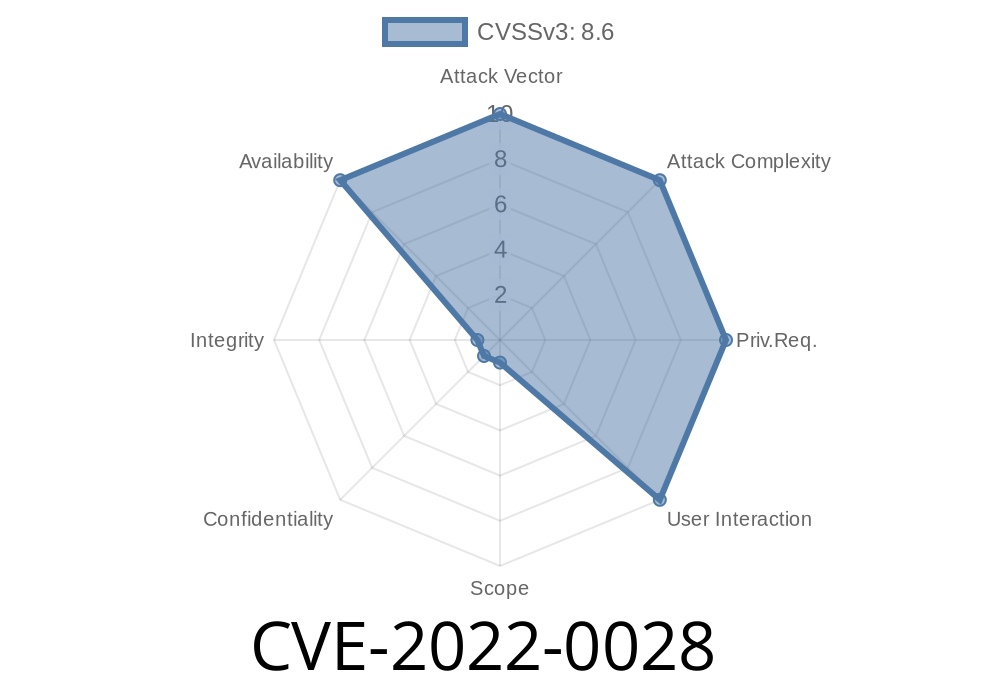
Summary of the Vulnerability
A vulnerability in the PAN-OS configuration has been identified that allows for authentication bypass. This vulnerability can allow an attacker to unauthenticated administrator access. This issue is a result of insufficient validation by the PAN-OS configuration and will be fixed soon in an upcoming release of PAN-OS.
There are multiple ways that this vulnerability can be exploited. One way is through a brute force attack (the attacker trying millions of different combinations of username and password). Another exploit is to use a social engineering attack where an attacker calls into the device using one of the default phone numbers listed in the configuration, and then asks spoofed questions that allow them to gain access without any authorization.
Mitigation Strategies for PAN-OS Software Instance Heartbeat Vulnerability
The vulnerability allows an attacker to send a malformed heartbeat packet to the affected PAN-OS software instance, which can cause the software instance to crash.
Given that there is no user authentication required in this vulnerability, we recommend performing one of the following mitigations:
- Disable feature "Heartbeat" on your PAN-OS devices by configuring them with “no feature heartbeat”. This configuration does not stop this vulnerability from being exploited should an attacker gain access to them.
- Implement a firewall rule that stops the malformed packets from reaching your IP address, such as configuring an ingress firewall policy to drop all packets with destination port 654 (Heartbeat) from all sources except localhost.
- Deploy a security patch to cover this vulnerability on your vulnerable PAN-OS software instances and then update those instances once the patch has been deployed by your firewall manufacturer or solution provider.
What to do if you have installed this fix and are experiencing problems
If you have installed this fix and are experiencing problems, please contact us for support.
Timeline
Published on: 08/10/2022 16:15:00 UTC
Last modified on: 08/16/2022 00:14:00 UTC