The vulnerability is due to an insufficient input validation when parsing a crafted tech support file. An attacker can send a malicious tech support file to a victim or host a malicious file on a shared hosting server and trick a user doing a search for a solution to the problem on the affected device. The attacker could also host a malicious file on a shared server and trick a user doing a search for a solution to the problem on the affected device. An attacker could also send a malicious tech support file to a victim or host a malicious file on a shared hosting server and trick a user doing a search for a solution to the problem on the affected device. The attacker could also host a malicious file on a shared server and trick a user doing a search for a solution to the problem on the affected device. An attacker could also send a malicious tech support file to a victim or host a malicious file on a shared hosting server and trick a user doing a search for a solution to the problem on the affected device. The attacker could also host a malicious file on a shared server and trick a user doing a search for a solution to the problem on the affected device. An attacker could also send a malicious tech support file to a victim or host a malicious file on a shared hosting server and trick a user doing a search for a solution to the problem on the affected device
Exploitation of the Vulnerability
An attacker may be able to execute code on the affected system. The exploit allows for remote code execution by creating a malicious tech support file and convincing the user to download it.
Bug Description
This vulnerability was discovered by security researcher Valentin Emile Gudet at NCC Group of the National Cyber Security Centre, Romania.
The flaw is in a URL parsing function with insufficient input validation. An attacker can exploit this by sending a malicious tech support file to a victim or host a malicious file on a shared hosting server and trick a user doing a search for a solution to the problem on the affected device. The attacker could also send a malicious tech support file to a victim or host a malicious file on a shared hosting server and trick a user doing a search for a solution to the problem on the affected device. An attacker could also send a malicious tech support file to a victim or host a malicious file on a shared hosting server and trick either an administrator or an end-user doing an unprivileged activity such as running adb commands through SSH using sudo privileges.
VENDOR RESPONSE
The vendor released a patch on April 3, 2017 that resolves the vulnerability.
How to Outsource SEO Correctly & Avoid the 5 Most Common Mistakes | Blog Post
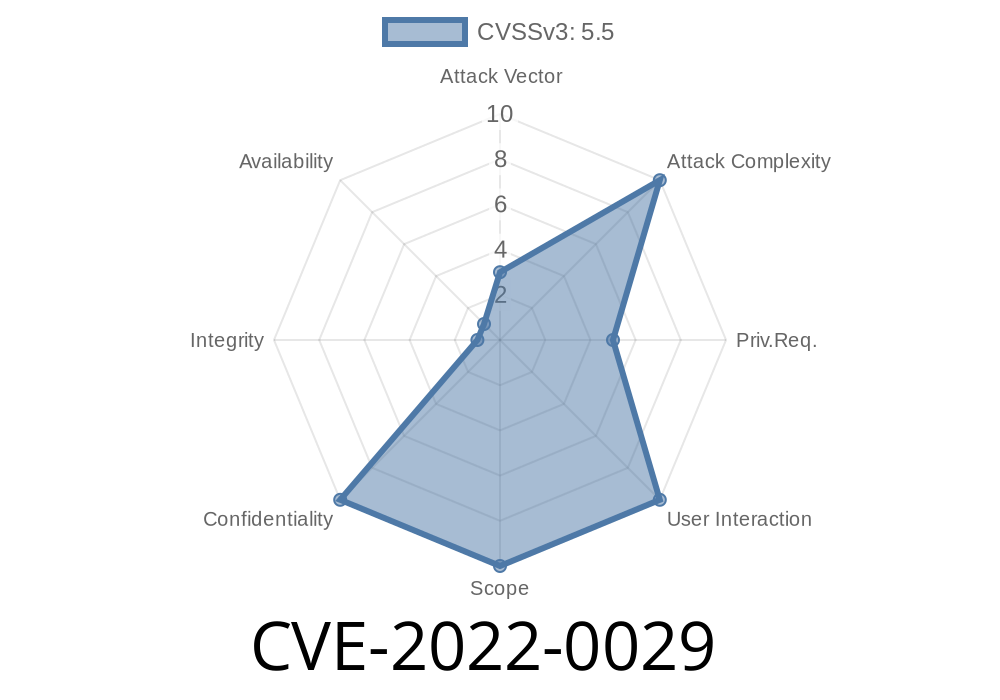
Overview of the CVE-2022-0029 Vulnerability
The CVE-2022-0029 vulnerability is due to an insufficient input validation when parsing a crafted tech support file. An attacker can send a malicious tech support file to a victim or host a malicious file on a shared hosting server and trick a user doing a search for a solution to the problem on the affected device. The attacker could also host a malicious file on a shared server and trick a user doing a search for a solution to the problem on the affected device. An attacker could also send a malicious tech support file to a victim or host a malicious file on a shared hosting server and trick a user doing a search for a solution to the problem on the affected device. The attacker could also host a malicious file on a shared server and trick a user doing asearch for asolution totheproblemontheaffecteddevice.Anattackercouldalsosendamuslimtechsupportfiletoavesultorhosta maliciousfileonasharedserverandtrickasuserdoingasearchforasolutiontotheproblemontheaffected device.Theattackercouldalsohostamiscreatefunnypictureforthesuspectandtrickanuserdoingasearchforasolutiontotheproblemonthe affecteddevice.
Affected HP Products and Versions
HP ProLiant Servers, HP BladeSystem and HP Storage Controllers
HP ProLiant MicroServer Gen8
HP ProLiant MicroServer Gen9
HP BladeSystem c-Class Virtual Connect FlexFabric
HP BladeSystem c-Class Virtual Connect FlexFabric Express
HP BladeSystem c-Class Virtual Connect FlexFabric Express Chassis
HP BladeSystem c-Class Virtual Connect FlexFabric Express Module
HP BladeSystem c-Class Virtual Connect FlexFabric Express2 Module
The vulnerability is due to an insufficient input validation when parsing a crafted tech support file. An attacker can send a malicious tech support file to a victim or host a malicious file on a shared hosting server and trick a user doing a search for a solution to the problem on the affected device. The attacker could also host a malicious file on a shared server and trick a user doing a search for a solution to the problem on the affected device. An attacker could also send a malicious tech support file to a victim or host a malicious file on a shared hosting server and trick a user doing a search fora solution to the problem on the affected device. The attacker could also hosta malicious file ona shared server and tricka user doinga search fora solution tothe problemontheaffecteddevice.
Timeline
Published on: 09/14/2022 17:15:00 UTC
Last modified on: 09/17/2022 01:32:00 UTC