This same issue can be leveraged to remotely execute a command on the machine with SYSTEM privileges by calling the runas.exe command with the -s switch. An attacker can do so by sending a maliciously crafted request to the ir_agent.exe process on a vulnerable version of Insight Agent. An attacker could leverage this vulnerability to install a malicious plugin to a vulnerable version of Insight Agent, giving them elevated rights and persistent access to the system. This vulnerability is rated critical due to the ability for an attacker to execute arbitrary commands on the system with SYSTEM privileges. This can be used to install a malicious plugin on a vulnerable Insight Agent instance, giving the attacker elevated rights on the system. An attacker could also leverage this vulnerability to install a malicious plugin on a vulnerable Insight Agent instance, giving the attacker persistent access to the system. This issue was fixed in Rapid7 Insight Agent version 3.1.3.80.
Product description
Rapid7 Insight Agent is a vulnerability management platform that aids in the detection, prevention and response to attacks against your IT infrastructure.
An attacker can use this vulnerability to remotely execute a command on the machine with SYSTEM privileges. This can be used to install a malicious plugin on a vulnerable Insight Agent instance, giving the attacker elevated rights on the system. An attacker could also leverage this vulnerability to install a malicious plugin on a vulnerable Insight Agent instance, giving the attacker persistent access to the system.
CVE-2016-10763
In this issue, the vulnerability is in the server.exe process which can be remotely exploited to run arbitrary code on a vulnerable version of Rapid7 Insight Server.
This issue can be leveraged to remotely execute a command on the machine with SYSTEM privileges by calling the runas.exe command with the -s switch. An attacker can do so by sending a maliciously crafted request to the ir_agent.exe process on a vulnerable version of Insight Agent. An attacker could leverage this vulnerability to install a malicious plugin to a vulnerable version of Insight Agent, giving them elevated rights and persistent access to the system. This vulnerability is rated critical due to the ability for an attacker to execute arbitrary commands on the system with SYSTEM privileges. This can be used to install a malicious plugin on a vulnerable Insight Agent instance, giving the attacker elevated rights on the system. An attacker could also leverage this vulnerability to install a malicious plugin on a vulnerable Insight Agent instance, giving the attacker persistent access to the system.
Microsoft Windows
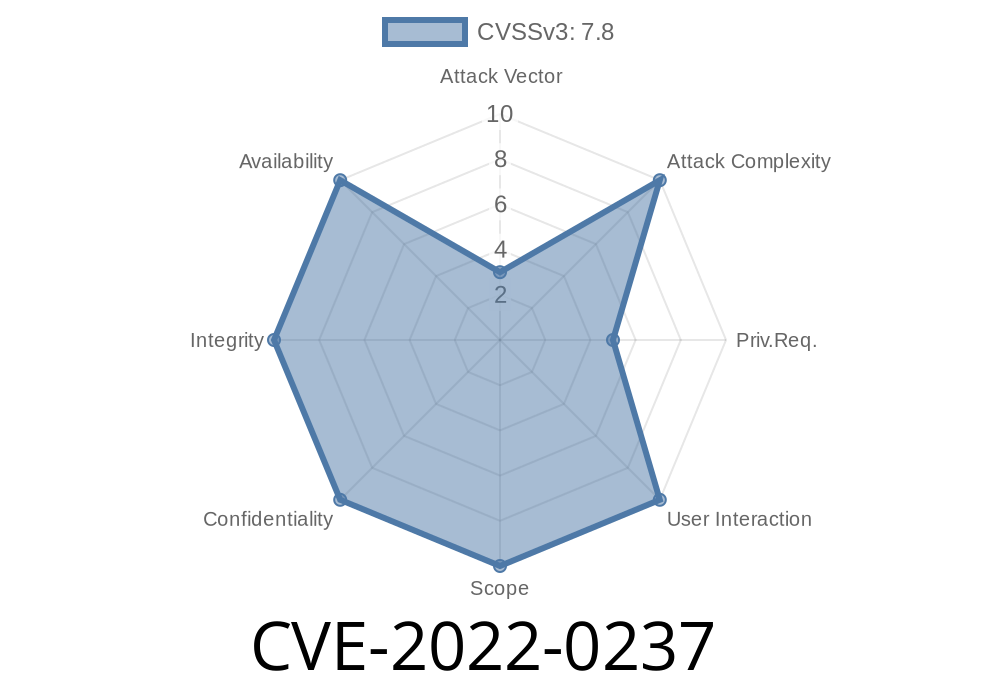
Process CVE-2022-0237
This same issue can be leveraged to remotely execute a command on the machine with SYSTEM privileges by calling the runas.exe command with the -s switch. An attacker can do so by sending a maliciously crafted request to the ir_agent.exe process on a vulnerable version of Insight Agent. An attacker could leverage this vulnerability to install a malicious plugin to a vulnerable version of Insight Agent, giving them elevated rights and persistent access to the system. This vulnerability is rated critical due to the ability for an attacker to execute arbitrary commands on the system with SYSTEM privileges. This can be used to install a malicious plugin on a vulnerable Insight Agent instance, giving the attacker elevated rights on the system. An attacker could also leverage this vulnerability to install a malicious plugin on a vulnerable Insight Agent instance, giving the attacker persistent access to the system. This issue was fixed in Rapid7 Insight Agent version 3.1.3.80
Products and Applications Affected by Rapid7 Insight Agent Vulnerability
The following products are vulnerable to this vulnerability:
- Rapid7 Insight Agent versions 3.1.3.80 and earlier
- Any other software running on Windows that utilizes the Insight Agent process, including:
- Microsoft Office 365
- Microsoft Dynamics CRM
- Microsoft Exchange Server
- Microsoft Lync Server
- Skype for Business server
- RSA SecurID token distribution point
- Symantec Endpoint Protection Suite for Windows XP, Windows Vista, and Windows 2003
How to verify the vulnerability?
The vulnerability can be verified by sending a maliciously crafted request to the ir_agent.exe process on a vulnerable version of Insight Agent. An attacker could leverage this vulnerability to install a malicious plugin to a vulnerable version of Insight Agent, giving them elevated rights and persistent access to the system.
Timeline
Published on: 03/17/2022 23:15:00 UTC
Last modified on: 03/24/2022 19:21:00 UTC