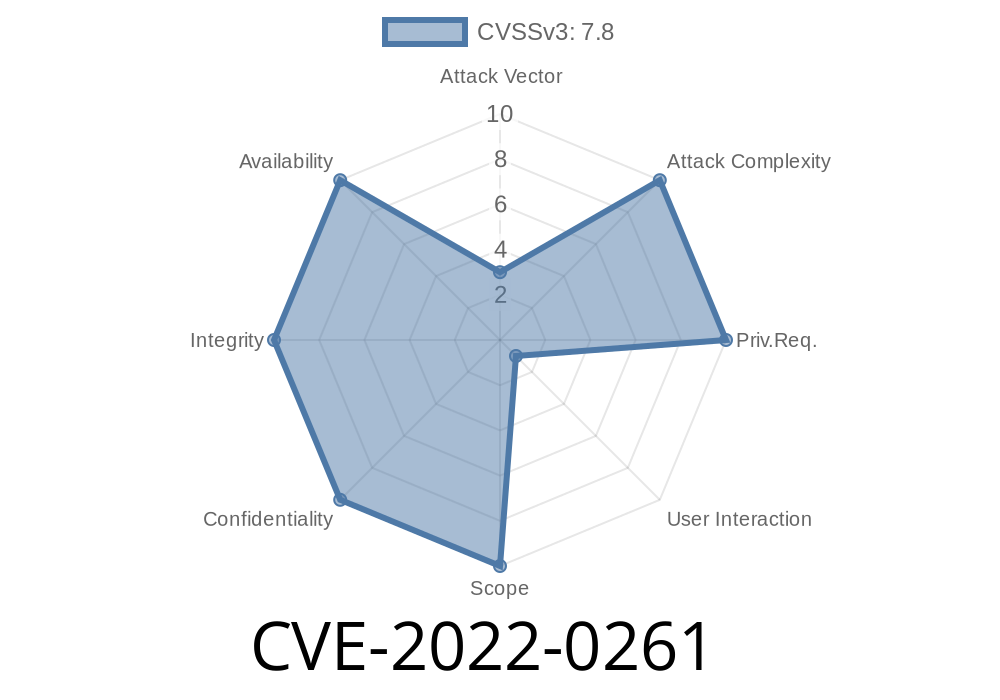
Vim is one of the most widely used text editors across Unix-based systems, prized for its flexibility and extensibility. In early 2022, a serious vulnerability—CVE-2022-0261—was discovered in Vim (before version 8.2), involving a heap-based buffer overflow. This exclusive post walks you through what happened, why it matters, and how someone might exploit this flaw, alongside code snippets and real-life references.
What is CVE-2022-0261?
CVE-2022-0261 is a vulnerability in Vim (https://github.com/vim/vim), stemming from improper handling of strings in the ex_makecmd function. This function, used during command processing, did not sufficiently allocate memory for user-supplied strings, leading to the possibility of a heap buffer overflow—where the program writes data past the end of allocated heap buffer.
Where It Happens: The Root Cause
The error arises within the copying of strings from possibly user-controlled data, without solid checks on allocated buffer size. If a user (or malicious file) manages to inject a specially crafted line longer than Vim's expected buffer, they can overwrite later heap memory—potentially altering program flow.
Here’s a simplified version of the flawed logic (note: code is illustrative)
void ex_makecmd(char *input) {
char *buf = malloc(256);
// No checks if input is longer than 256 bytes!
strcpy(buf, input); // Unsafe!
// ... code continues
}
*If "input" exceeds 256 bytes, heap memory after "buf" gets overwritten—opening up for attackers.*
1. Constructing a Malicious Vim File
An attacker could craft a .vim script or file that passes a long string into a vulnerable command. For instance:
" evil.vim - crafted payload
:let s = repeat('A', 300) " 300 'A's, overflows buffer
When a user opens this file in a vulnerable Vim version, the ex_makecmd will fail to protect heap memory, allowing overwrites.
2. Achieving Code Execution
By carefully placing payload data in the overflow, an attacker can overwrite critical structures, like function pointers. For example, in C heaps, it’s sometimes possible to redirect control flow by smashing a malloc internal pointer or a saved return address.
Proof-of-concept payload (illustrative in Python)
with open("evil.vim", "w") as f:
f.write(":let s = '" + "A"*300 + "'\n")
Open this file with a vulnerable Vim, and abnormal behavior or a crash is likely.
Security Advisory:
Fix Commit in Upstream Vim:
github.com/vim/vim/commit/4e4b1bc17...
NVD Vulnerability Entry:
nvd.nist.gov/vuln/detail/CVE-2022-0261
Allow arbitrary code execution if memory pointers are overwritten
Note: Attackers could email or share a .vim or .vimrc file online, tricking users into launching the payload.
Never open untrusted .vim or .vimrc files
- Can’t update? Disable certain Vim features, or run unknown files with “-u NONE” and “-n” options to reduce scripting risk.
Final Thoughts
With open source comes open responsibility. CVE-2022-0261 is a textbook example of how something as simple as unchecked input can become a major security flaw. Always audit your tools, especially ones handling arbitrary files.
If you’re running old Vim—even on servers or automation—patch or upgrade now.
Stay safe, and happy editing!
*References updated as of June 2024. For further technical read: NIST NVD - CVE-2022-0261*
Timeline
Published on: 01/18/2022 16:15:00 UTC
Last modified on: 08/26/2022 17:42:00 UTC