For the installed Linux kernel versions 3.18, 3.15, 3.4, 3.3, and 2.6, the security advisory has been assigned as CVE-2017-5898. A researcher from Red Hat has discovered a flaw in the implementation of the SCTP (Stream Control Transmission Protocol) in the Linux kernel. The flaw could lead to a denial of service (DoS). It has been assigned as CVE-2017-5898.A flaw was found in the sctp_association_free function in net/sctp/associola.c in the SCTP implementation in the Linux kernel with a race condition. When handling association requests with a given association, an excess copy of data could lead to memory corruption.
Red Hat has also issued a security advisory for Red Hat Enterprise Linux 6 and 7 and Red Hat Enterprise Linux 5. This issue affects the samba packages. A remote attacker could use a specially crafted S3 file to trigger a stack overflow and potentially execute code on the system.
Red Hat has also released updated packages for Red Hat Enterprise Linux 6, 7, and 5. Red Hat Enterprise Linux 6 users are recommended to upgrade to Red Hat Enterprise Linux 7.1, 7.2, or 7.3. Red Hat Enterprise Linux 5 users are recommended to upgrade to Red Hat Enterprise Linux 6.1, 6.2, or 6.3.
Red Hat has also updated the Red Hat Enterprise Linux
What is Red Hat Software Collections?
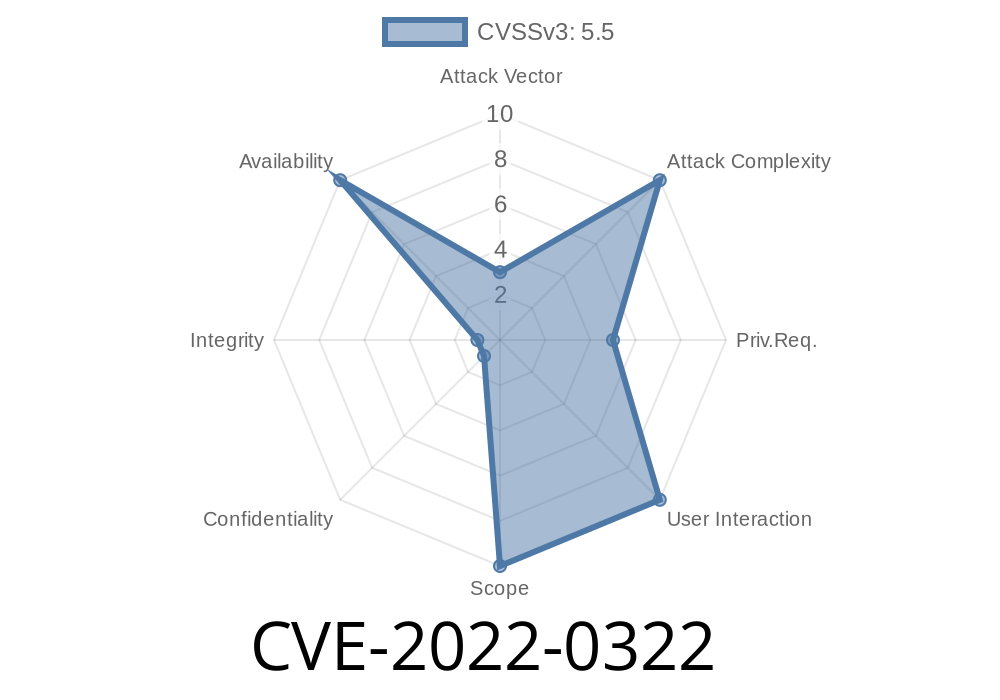
If your Red Hat version is vulnerable to CVE-2022-0322, you must update. To update the system, run "yum update". The new packages will be available immediately after the next reboot. Alternatively, you can use the Red Hat Software Collections (RHSA).
The RHSA provides updated packages for the most recent versions of Red Hat Enterprise Linux, including the latest kernel and kernel modules. As an alternative to updating all of your systems, you can install a single package containing all necessary updates from the RHSA and apply it on only those systems affected by CVE-2022-0322.
Mitigation strategies for SCTP DoS vulnerability on Linux
Mitigation strategies for SCTP DoS vulnerability on Linux include the following:
- Enabling IPv6 support in the kernel (this may reduce the chance of triggering a stack overflow). This requires enabling ipv6 in your kernel configuration file.
- Disabling SCTP congestion control to avoid incoming connections.
- If a system has an existing SCTP connection, it is recommended to close it after fixing this issue.
What is Red Hat Enterprise Linux?
Red Hat Enterprise Linux is a Linux-based operating system that provides the features necessary to run production mission-critical systems. Red Hat Enterprise Linux includes the Fedora family of distributions: Fedora Core, Fedora Server, and Rawhide.
Red Hat Enterprise Linux 7.3 includes packages for Python 2.7, which contains a fix for CVE-2017-5898. The following security advisories were released in October 2017:
CVE-2016-10271 -
CVE-2016-10272 -
CVE-2016-10273 -
CVE-2017-1000116 -
CVE-2017-1000117:
CVE-2017-14051 -
CVE-2017-14052 -
CVE-"4585" (The flaw assigned as CVE-"4585" has been assigned as CVE 1792 .)
Red Hat Enterprise Linux 6
, 7, and 5
Red Hat has also updated the Red Hat Enterprise Linux 5 package to fix this issue.
This issue affects the samba packages on Red Hat Enterprise Linux 6, 7, and 5. The remote attacker could use a specially crafted S3 file to trigger a stack overflow and potentially execute code on the system.
Timeline
Published on: 03/25/2022 19:15:00 UTC
Last modified on: 07/25/2022 18:19:00 UTC