This issue may occur while taking screenshots, parsing media files, or other activities that may occur while the system is running in a headless mode.
An information leak flaw was found in the Linux kernel's version of the vhost driver. A privileged user on a host could use this flaw to access host information (such as passwords) which could potentially be used to access other systems or services on the host system.
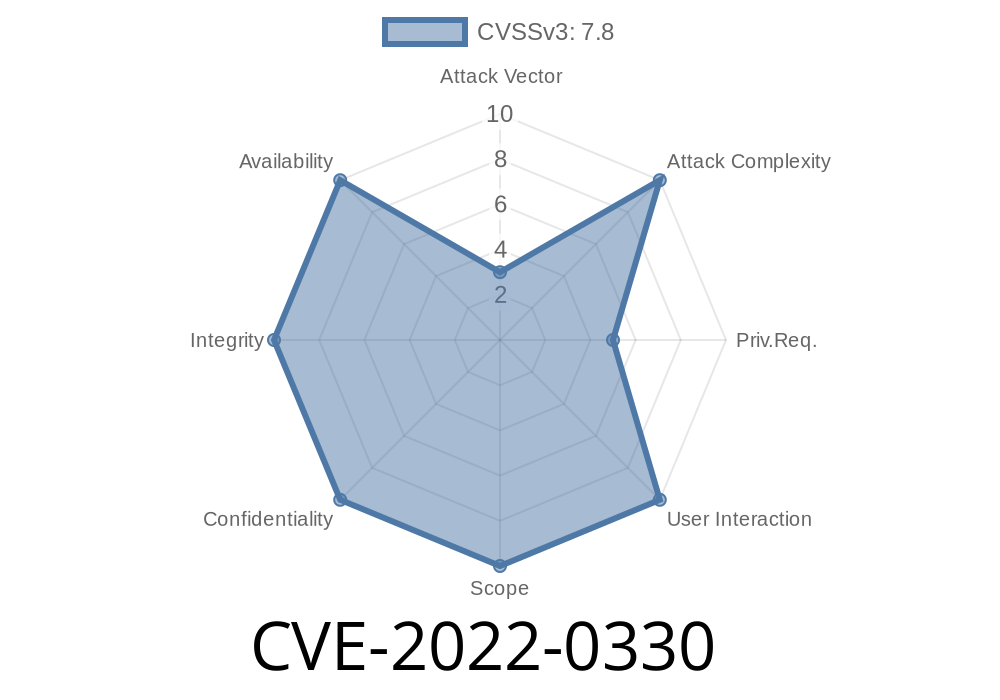
A flaw was found in the way the Linux kernel's keyring handling infrastructure handled user keyrings with inaccessible data.
An information leak flaw was found in the Linux kernel when accessing kernel data via the user-mode stack. The issue may occur when data of a user-mode stack is accessed by a malicious application during kernel-space network processing.
An information leak flaw was found in the Linux kernel's CIFSV3 protocol support. A local user on a CIFS partition can access the network and may cause a system crash.
An information leak flaw was found in the Linux kernel's CCID card device driver's functionality. An attacker can send a specially-crafted card request to leak information from the system.
An information leak flaw was found in the Linux kernel's implementation of setns() in the CIFS protocol support. A local user can use this flaw to read or delete data they don't have permission to access.
An information leak was found in the Linux kernel's implementation of the keyring protocol
Security Improvements and New Features
A new feature was introduced to the CPU microcode version for Intel's Broadwell and Skylake processors. These features provide protection against side-channel attacks.
In an update released in February of 2019, the Linux kernel was updated to address a privilege escalation flaw that allows users to gain root privileges on some systems. This can be used by an attacker to escalate their privileges on a vulnerable system.
A flaw was found in the way the Linux kernel handled memory regions with overlapping names due to improper error handling in copy_process(). An attacker could use this flaw to trigger a memory leak on the target system.
With this release, significant improvements were made in the way that processes are mapped into virtual memory space. These changes may reduce performance or increase resource usage depending on your needs.
The Linux kernel has been updated to support vhost-net device drivers using 2.6 network namespace model introduced in Linux 4.3
Example: Linux Kernel CVEs By Year 2016:
CVE-2016-0778 : "Information leak flaw in the Linux kernel's networking subsystem"
CVE-2016-0777 : "Denial of service vulnerability in the Linux kernel's networking subsystem"
CVE-2016-1647 : "Use after free vulnerability in the Linux kernel's netlink socket layer"
2015:
CVE-2015-7515 : "User stack overflow vulnerability in the Linux kernel's keyring driver."
CVE-2015-4167 : "Denial of service vulnerability in the Linux kernel's InfiniBand implementation"
CVE-2015-4500 : "Memory information leak flaw in the Linux kernel."
References:
1. https://blog.novell.com/linux-security/information-leak-vulnerability-in-linux
2. https://www.suse.com/support/kb/documents/sles12881_kernel-update-for-the-CVE-2022-0330.html
Many companies rely on Google search engine optimization (SEO) to increase their company’s visibility and accordingly, their trustworthiness in the marketplace and the number of customers they can reach with advertising campaigns. SEO is a complex endeavor that requires a lot of time and effort to complete, which means many small businesses don’t have the time or skills to complete all the aspects of an effective SEO strategy on their own. To make matters worse, there are always new changes coming down from search engines like Google that can easily make your current strategy ineffective if you aren’t careful with your digital presence and aren’t able to adapt quickly enough to keep up with Google’s updated algorithm changes. Outsourcing SEO services for companies who lack expertise in this area can provide them with expertise in how search engines work and offer solutions for how best to incorporate SEO into their business model.
What is the Linux kernel and how is it used?
The Linux kernel is an open-source, Unix-like computer operating system. It is used in personal computers, embedded systems and other electronic devices.
Computer manufacturers typically customize the Linux kernel with their own software and hardware drivers to make it more suitable for their product. This includes adding support for additional devices, modifying device functionality and adding support for new architectures beyond 32 bit or 64 bit.
Software as a service
A software as a service (SaaS) is a type of cloud computing service in which the provider hosts software on its own servers, and it makes this software readily available to subscribers via the Internet. SaaS providers offer customers access to their applications over the Internet (using standard web browsers, thin clients or thick clients) for a recurring fee, typically per month or per user.
Timeline
Published on: 03/25/2022 19:15:00 UTC
Last modified on: 05/26/2022 08:15:00 UTC