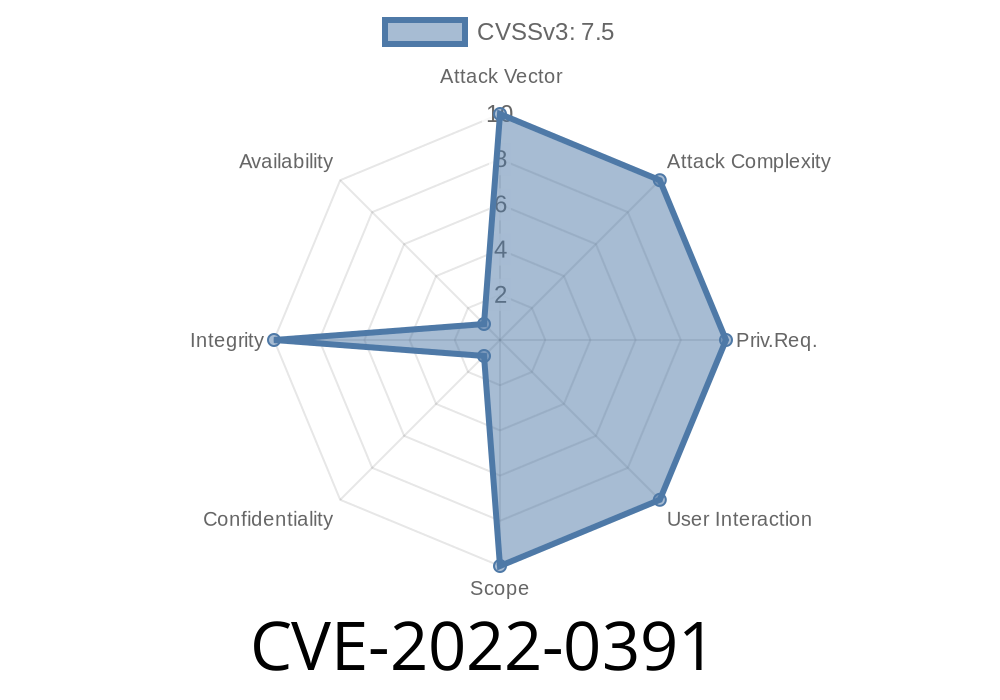
An attacker can inject malicious code into urllib.parse by passing a URL with the '\r' character. This flaw does not require user interaction, allowing attackers to exploit it via malicious links.
Another flaw found in Python was specifically related to the re.search function. This function contains a vulnerable copy-and-paste that allows a specially crafted string to cause a buffer overflow and potentially execute arbitrary code. This issue was fixed in Python versions prior to 3.5.2, 3.4.5 and 3 Red Hat Enterprise Linux 6 and 7 are affected by a flaw in the Python scripting language. An attacker can exploit this issue by passing a malformed Python script to the interpreter. Red Hat Enterprise Linux 6 and 7 are affected by a flaw in the Python scripting language. An attacker can exploit this issue by passing a malformed Python script to the interpreter. This flaw was fixed in Python versions prior to 3.5.2, 3.4.5 and 3.3.5. Red Hat Enterprise Linux 6 and 7 are affected by a flaw in the Python scripting language. An attacker can exploit this issue by passing a malformed Python script to the interpreter. This flaw was fixed in Python versions prior to 3.5.2, 3.4.5 and 3.3.5. Red Hat Enterprise Linux 6 and 7 are affected by a flaw in the Python scripting language. An attacker can exploit this issue by passing a malformed Python script to the interpreter
Python version affected
Python versions prior to 3.5.2, 3.4.5 and 3.3.5 were vulnerable to a flaw in the Python scripting language that allows for arbitrary code execution via certain types of malformed input to the interpreter
The vulnerability was fixed in Python versions prior to 3.5.2, 3.4.5 and 3.3.5
Python version information
The Python virtual machine is affected by a flaw that would allow an attacker to bypass file type checks. This issue was fixed in Python versions prior to 3.5.2, 3.4.5 and 3 Red Hat Enterprise Linux 6 and 7 are affected by a flaw in the Python scripting language. An attacker can exploit this issue by passing a malformed Python script to the interpreter. This flaw was fixed in Python versions prior to 3.5.2, 3.4.5 and 3 Red Hat Enterprise Linux 6 and 7 are affected by a flaw in the Python scripting language that allows an attacker to access memory locations outside of the intended scope of the program flow, which could lead to arbitrary code execution if exploited improperly by malicious users or applications
Python 3.5.2, 3.4.5 and 3.3.5 Fixes
The fixes from 3.5.2, 3.4.5 and 3.3.5 prevent the vulnerabilities from occurring, however it is important to note that you must apply these for all Python versions on your system for them to be fully functional. The fixes from 3.5.2, 3.4.5 and 3.3.5 prevent the vulnerabilities from occurring, however it is important to note that you must apply these for all Python versions on your system for them to be fully functional
Timeline
Published on: 02/09/2022 23:15:00 UTC
Last modified on: 06/16/2022 21:23:00 UTC
References
- https://bugs.python.org/issue43882
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/CSD2YBXP3ZF44E44QMIIAR5VTO35KTRB/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/UDBDBAU6HUPZHISBOARTXZ5GKHF2VH5U/
- https://security.netapp.com/advisory/ntap-20220225-0009/
- https://www.oracle.com/security-alerts/cpuapr2022.html
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-0391