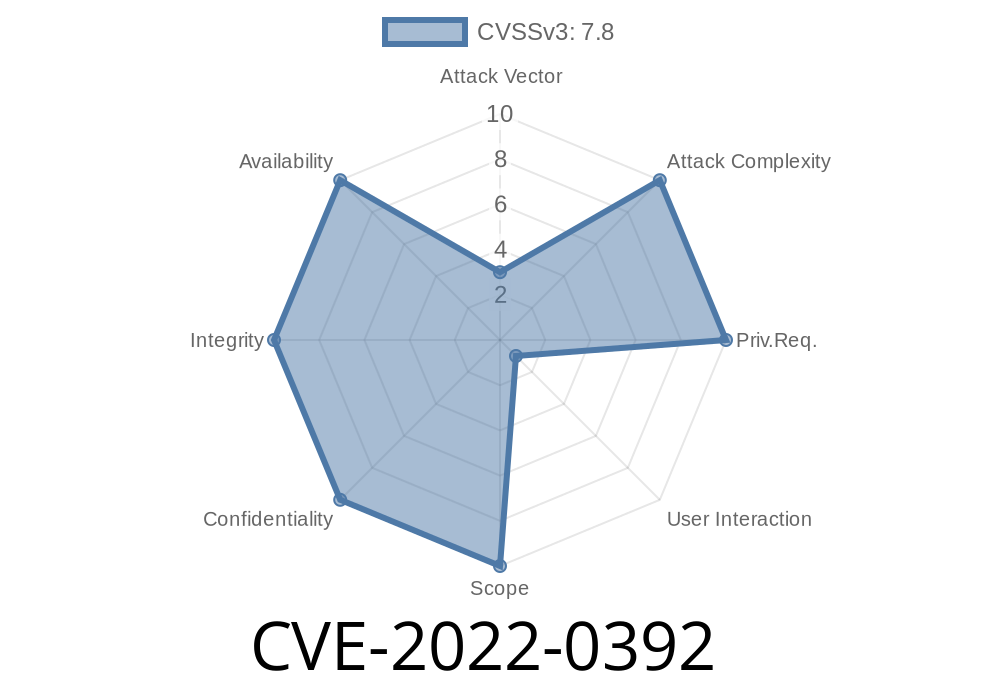
Vim, the popular text editor used by millions of developers worldwide, faced a critical security risk in early 2022. Known as CVE-2022-0392, this vulnerability let attackers exploit a heap-based buffer overflow present in specific contexts. This post offers an exclusive, easy-to-understand breakdown of how the issue happened, how attackers could exploit it, and how you can protect your system.
What Is CVE-2022-0392?
CVE-2022-0392 is a heap buffer overflow security vulnerability discovered in the Vim codebase before version 8.2. A buffer overflow means a program writes more data to a memory area than it was meant to hold, which can overwrite adjacent memory and lead to crashes, data corruption, or, in the worst case, remote code execution (RCE).
A heap-based overflow is especially serious, as it targets the dynamically allocated memory that programs depend on for flexibility.
Where Did the Flaw Happen?
The flaw was dug out by security researchers examining file reading and buffer handling code in Vim. The vulnerability happened when Vim tried to process a file or input in an unexpected way, causing its internal memory allocations (the heap) to get overwritten.
The critical function (ex_eval) responsible for handling certain evaluation commands in scripts didn’t correctly check buffer sizes before copying data. Attackers could carefully craft a file (like a Vim script or text file) that triggers the overflow.
Here’s an illustrative version (simplified for clarity) of what used to go wrong
char *buffer = malloc(256);
if (buffer == NULL) exit(1);
strcpy(buffer, input_from_file); // input_from_file is unchecked length
If input_from_file is longer than 256 bytes, it overflows buffer, overwriting adjacent heap space with attacker-controlled data.
In the real Vim 8.2 source, the bug was subtler; it combined buffer size miscalculations and unsafe memory copies within evaluation functions.
For reference, see the official commit patch
With careful manipulation, the attacker can jump to execution of code they control (shellcode).
It’s worth noting that real-world exploitation is challenging, since stack protection (ASLR, NX, etc.) and typical Vim sandboxing help, but not always. Sophisticated attackers might chain this with other bugs for reliable code execution.
A basic PoC script (not directly dangerous, for educational purposes only)
" Save as overflow.vim
let a = repeat('A', 100)
exec a
When loaded in an unpatched Vim, this could trigger a heap overflow, as the buffer handling doesn’t limit the size.
Original References & Further Reading
- NVD Entry for CVE-2022-0392
- GitHub Issue Discussion
- Full Patch and Commit
- VIM Security Notices
Conclusion
CVE-2022-0392 is a cautionary tale. Even the tools we trust most can hide dangerous bugs. Keeping tools up to date and being cautious with untrusted input are the best defenses. The Vim team responded quickly, but for a while, millions were potentially exposed.
Stay alert — even your text editor can be a target.
Timeline
Published on: 01/28/2022 22:15:00 UTC
Last modified on: 08/26/2022 17:45:00 UTC