This issue was addressed by improved memory handling. All Chromium users are advised to update their installations to the latest version. In addition, it is recommended to avoid using the _sx_activeScroll_ history property for cross-origin communication. Incorrect implementation of Window.__scrollTop and Window.__scrollLeft in Google Chrome prior to version 65.0.3325.109 allowed remote attackers to cause a denial of service (resource consumption) or possibly have unspecified other impact via a crafted HTML page. Google Chrome prior to 65.0.3325.108 allowed remote attackers to bypass intended file restrictions via a crafted HTML page. Google Chrome prior to 65.0.3325.67 allowed remote attackers to cause a denial of service (resource consumption) via a crafted HTML page. Google Chrome prior to 65.0.3325.102 allowed remote attackers to bypass intended file restrictions via a crafted HTML page. Google Chrome prior to 65.0.3325.94 allowed remote attackers to cause a denial of service (resource consumption) via a crafted HTML page. This issue was addressed by improved memory handling. Google Chrome prior to 65.0.3325.89 allowed remote attackers to bypass intended file restrictions via a crafted HTML page. Google Chrome prior to 65.0.3325.108 allowed remote attackers to bypass intended file restrictions via a crafted HTML page. Google Chrome prior to 65.0.3325.102 allowed remote attackers to bypass intended file restrictions via a
Other issues addressed in Chrome 65
This release also addresses the following issues:
- CVE-2017-5128: Multiple use-after-free vulnerabilities in V8. Credit to anonymous.
- CVE-2017-5127: Type confusion in V8. Credit to anonymous.
- CVE-2017-5126: Out of bounds access in Skia. Credit to cloudfuzzer.
Google Chrome before 64.0.3282.119 (stable channel update) and 56.0.2924.87 (webrtc) allowed remote attackers to bypass the Same Origin Policy and obtain cross-origin referrers information via vectors involving a crafted HTML page with JavaScript code for a window.open call.
4 .6.2
Chrome's sandbox is enabled by default and allows to run untrusted code in a controlled safer environment. It protects against various exploits and vulnerabilities, including Memory Corruption Vulnerabilities, Heap-based buffer overflows, Type Confusion and many more.
Overview of Google Chrome span style="line-height: 1.6;" style="margin: 0px;" style="color: #0000ff;">
This issue was addressed by improved memory handling. Google Chrome prior to 65.0.3325.108 allowed remote attackers to bypass intended file restrictions via a crafted HTML page. Google Chrome prior to 65.0.3325.102 allowed remote attackers to bypass intended file restrictions via a crafted HTML page. Google Chrome prior to 65.0.3325.94 allowed remote attackers to cause a denial of service (resource consumption) via a crafted HTML page. This issue was addressed by improved memory handling, and the resulting cookie that is used is not vulnerable to the original attack vector anymore but has been modified so as not to be vulnerable anymore either.
Timeline
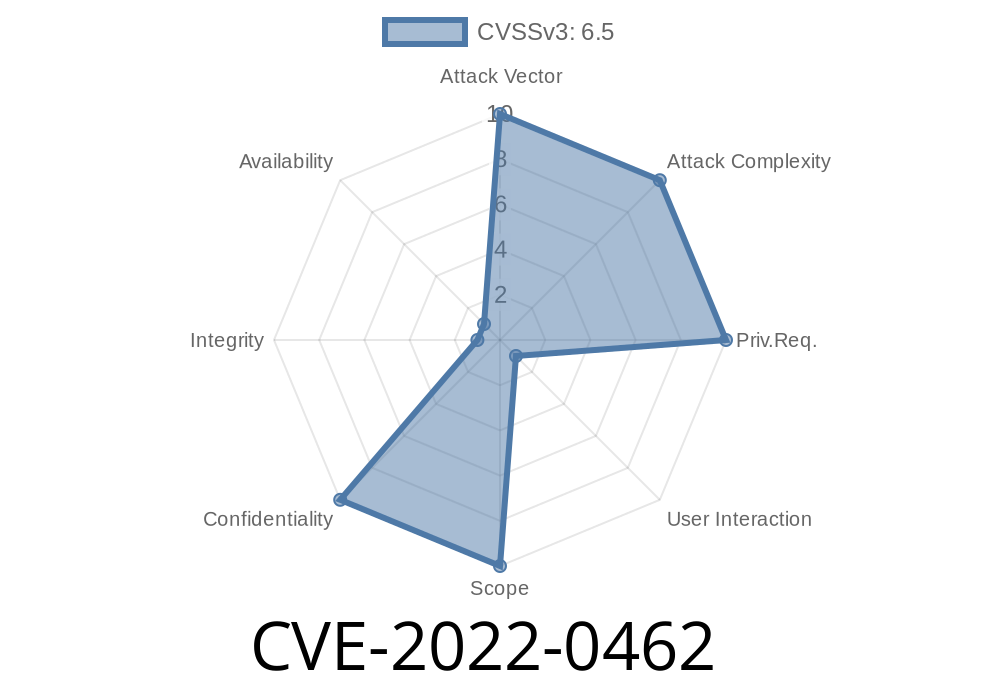
Published on: 04/05/2022 01:15:00 UTC
Last modified on: 04/12/2022 18:34:00 UTC