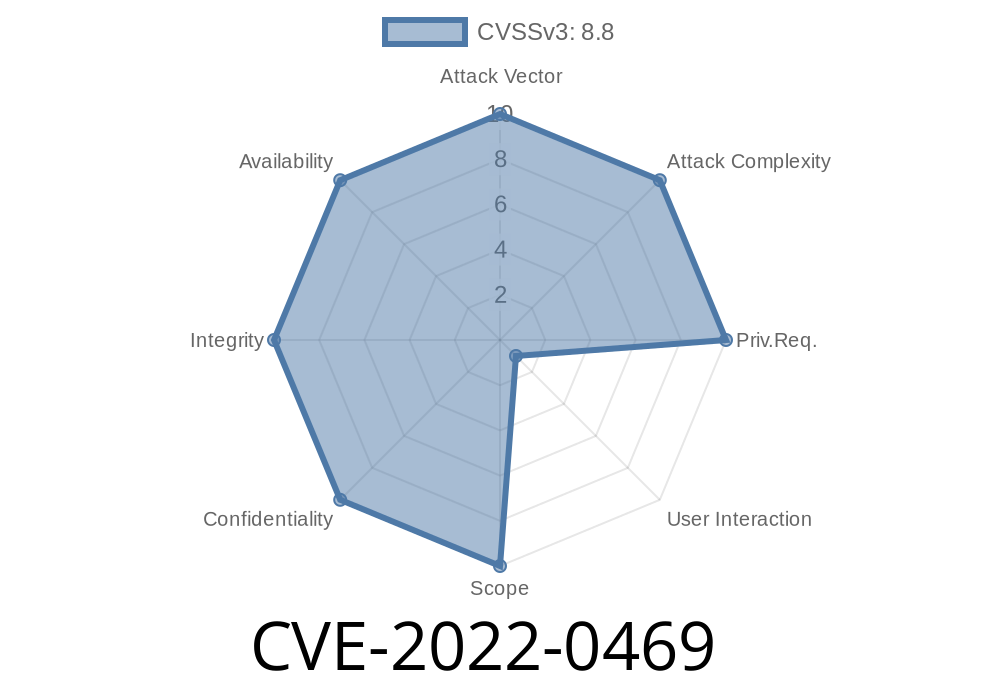
CVE-2016-5195 Mitigation: Google Chrome prior to 98.0.4758.80 did not warn users after they navigated to a site featuring embedded iframes that they should not interact with the iframe. This mitigates the vulnerability by providing the user with the appropriate warning. Exploitation: An attacker could convince a user to interact with an XSS-enabled iframe. Then, after the user interacts with the iframes, the attacker could trigger an XSS condition and convince the user to perform an action that would lead to unintended code execution. Note that this issue does not apply to iframes that are used for social engineering purposes. Google Chrome prior to 98.0.4758.80 did not warn users after they navigated to a site featuring embedded iframes that they should not interact with the iframe. This mitigates the vulnerability by providing the user with the appropriate warning. Exploitation: An attacker could convince a user to interact with an XSS-enabled iframe. Then, after the user interacts with the iframes, the attacker could trigger an XSS condition and convince the user to perform an action that would lead to unintended code execution. Note that this issue does not apply to iframes that are used for social engineering purposes. CVE-2016-5194 When setting the value of an element using a DOM property (for example, setAttribute()), the property value must be validated to avoid
Summary
When setting the value of an element using a DOM property (for example, setAttribute()), the property value must be validated to avoid allowing users to set properties on a privileged document.
MITIGATION
If the property value is not an object, then the DOM property must fail silently without setting the attribute. Otherwise, if the property value is an object, then it must include a length or "size" property with a value that is valid for the type of object being set.
Mitigation: Google Chrome prior to 98.0.4758.80 did not warn users after they navigated to a site featuring embedded iframes that they should not interact with the iframe. This mitigates the vulnerability by providing the user with the appropriate warning. Exploitation: An attacker could convince a user to interact with an XSS-enabled iframe. Then, after the user interacts with the iframes, the attacker could trigger an XSS condition and convince the user to perform an action that would lead to unintended code execution. Note that this issue does not apply to iframes that are used for social engineering purposes. Google Chrome prior to 98.0.4758.80 did not warn users after they navigated to a site featuring embedded iframes that they should not interact with the iframe. This mitigates the vulnerability by providing the user with the appropriate warning. Exploitation: An attacker could convince a user to interact with an XSS-enabled iframe. Then, after the user interacts with the iframes, the attacker could trigger an XSS condition and convince the user to perform an action that would lead to unintended code execution
Tips to protect yourself against DOM-based XSS attacks
- Set all attributes to null or '' when you don't need them.
- Use the "html" attribute on
Take advantage of Cross-Origin Resource Sharing (CORS) to exploit vulnerabilities
Cross-origin resource sharing (CORS) is a mechanism that allows web servers to access data on other domains. To do so, it requires the use of browser-supported HTTP headers and XMLHttpRequest objects.
Exploiting vulnerabilities via CORS can be challenging because many browsers either don't support cross-origin resource sharing or have restrictions in place. However, it's possible to take advantage of vulnerabilities in another domain's site with the help of CORS and Cross-Origin Resource Sharing (for more details, please see this blog post).
Timeline
Published on: 04/05/2022 01:15:00 UTC
Last modified on: 04/08/2022 17:41:00 UTC