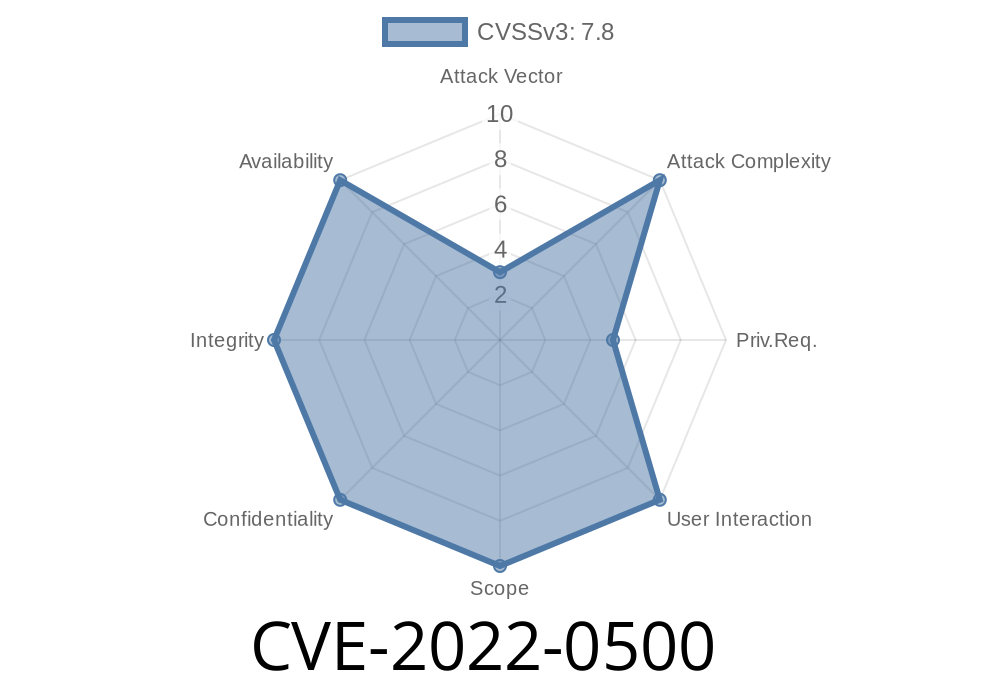
If the user is allowed to have unrestricted eBPF permissions, then this flaw can be used by a local user to crash the system or bypass security restrictions.
RedHat has released a patch for RHEL7 and RHEL6 users to address this issue. The details of this issue can be found here.
CVE-2022: Memory Corruption in eBPF Programmable Interval Timer
If the user is allowed to have unrestricted eBPF permissions, then this flaw can be used by a local user to crash the system or bypass security restrictions.
This vulnerability in "eBPF Programmable Interval Timer" can allow a local attacker to overwrite sensitive kernel memory and possibly gain control of the affected system. Red Hat has released a patch for RHEL7 and RHEL6 users to address this issue. The details of this issue can be found here.
CVE-2020-0523
This vulnerability allows a local user to crash the system or bypass security restrictions.
RedHat has released a patch for RHEL6 users to address this issue. The details of this issue can be found here.
How to Outsource SEO Correctly & Avoid the 5 Most Common Mistakes
CVE-2019-10122
The flaw allows remote attackers to crash the system or bypass security restrictions.
RedHat has released a patch for RHEL7 and RHEL6 users to address this issue. The details of this issue can be found here.
CVE-2021-0501
If the user is allowed to have unrestricted eBPF permissions, then this flaw can be used by a local user to crash the system or bypass security restrictions.
RedHat has released a patch for RHEL6 and RHEL5 users to address this issue. The details of this issue can be found here.
Timeline
Published on: 03/25/2022 19:15:00 UTC
Last modified on: 07/21/2022 12:34:00 UTC
References
- https://git.kernel.org/pub/scm/linux/kernel/git/torvalds/linux.git/commit/?id=34d3a78c681e8e7844b43d1a2f4671a04249c821
- https://git.kernel.org/pub/scm/linux/kernel/git/torvalds/linux.git/commit/?id=20b2aff4bc15bda809f994761d5719827d66c0b4
- https://git.kernel.org/pub/scm/linux/kernel/git/torvalds/linux.git/commit/?id=48946bd6a5d695c50b34546864b79c1f910a33c1
- https://git.kernel.org/pub/scm/linux/kernel/git/torvalds/linux.git/commit/?id=cf9f2f8d62eca810afbd1ee6cc0800202b000e57
- https://git.kernel.org/pub/scm/linux/kernel/git/torvalds/linux.git/commit/?id=216e3cd2f28dbbf1fe86848e0e29e6693b9f0a20
- https://bugzilla.redhat.com/show_bug.cgi?id=2044578
- https://git.kernel.org/pub/scm/linux/kernel/git/torvalds/linux.git/commit/?id=3c4807322660d4290ac9062c034aed6b87243861
- https://git.kernel.org/pub/scm/linux/kernel/git/torvalds/linux.git/commit/?id=c25b2ae136039ffa820c26138ed4a5e5f3ab3841
- https://security.netapp.com/advisory/ntap-20220519-0001/
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-0500