In early 2022, Mozilla patched serious memory safety bugs in Firefox found by brilliant Mozilla developers and community contributors: Gabriele Svelto, Sebastian Hengst, Randell Jesup, Luan Herrera, Lars T Hansen, and the Mozilla Fuzzing Team. While memory bugs are a familiar foe for browser makers, CVE-2022-0511 stood out because the vulnerable code hinted at memory corruption—a flaw that, when found, often lets attackers run their own code using the victim’s browser.
Let’s break down what this bug was, how a would-be attacker could have exploited it, and what you can do to stay safe.
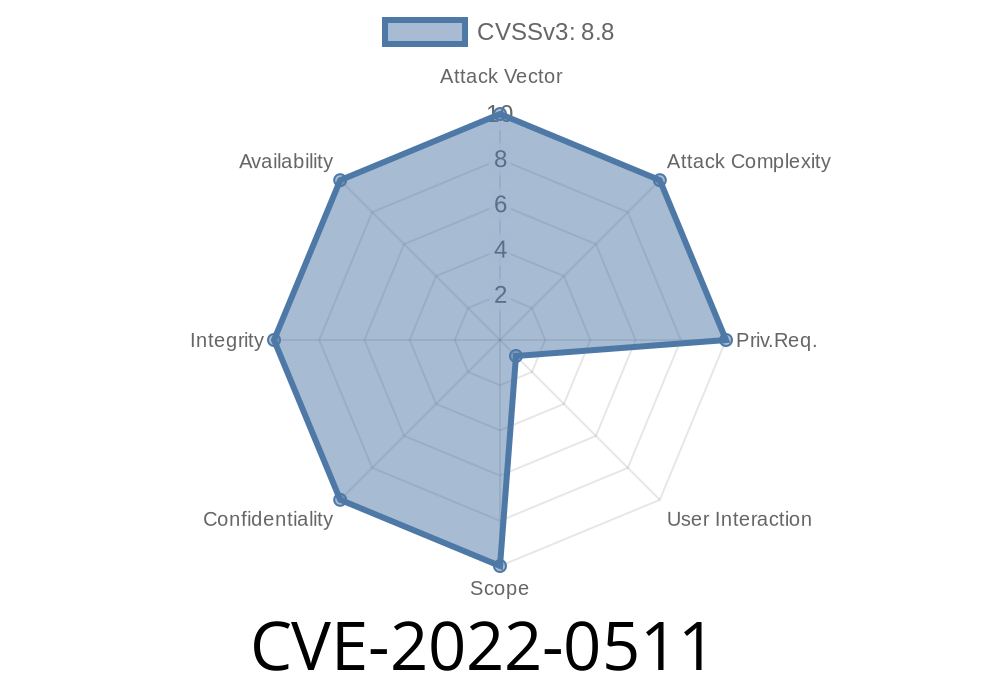
What is CVE-2022-0511?
CVE-2022-0511 is a memory safety vulnerability in versions of Mozilla Firefox before version 97, as officially described on the Mozilla Foundation Security Advisory 2022-06:
> "Mozilla developers and community members Gabriele Svelto, Sebastian Hengst, Randell Jesup, Luan Herrera, Lars T Hansen, and the Mozilla Fuzzing Team reported memory safety bugs present in Firefox 96. Some of these bugs showed evidence of memory corruption and we presume that with enough effort some of these could have been exploited to run arbitrary code."
This means that certain bugs, if “chained” together with skill, could let a hacker convince Firefox to do something it was never meant to—often opening the door to arbitrary code execution (ACE).
How Could This Be Exploited?
Memory corruption vulnerabilities are dangerous because they allow an attacker to break out of the normal execution flow of a program. In Firefox, this flaw might be triggered by convincing a user to visit a malicious website that sends specially crafted data to exploit the memory issue.
Attacker crafts a webpage that triggers the vulnerable code path in Firefox <97.
2. The page delivers malformed data or input, causing Firefox to corrupt its own memory (e.g., out-of-bounds write).
3. The attacker uses JavaScript or WebAssembly to carefully spray the browser memory (a technique called “heap spraying”) with malicious shellcode.
4. When the vulnerability corrupts memory, the attacker’s code is executed instead of regular Firefox code.
> While proof-of-concept (PoC) details have not been widely published due to the risk, the methods would be similar to other browser memory corruption exploits. For example, see HowTo: Analyse and Exploit Memory Corruption Vulnerabilities in Chrome for a technical deep dive into real-world exploitation steps in a similar browser context.
Example Code Snippet
While the exact Firefox code involved has not been disclosed, here’s a simplified pseudocode example in C++ that shows the kind of bug that can cause a memory safety issue:
void copyImageData(char* src, char* dst, int len) {
// Vulnerable: No bounds check!
for (int i = ; i < len; i++) {
dst[i] = src[i];
}
}
If an attacker controls len and can set it to a number larger than the size of the destination buffer, data is written elsewhere in memory—sometimes overwriting important control data.
In JavaScript—used to exploit such browser bugs—a heap spray might look like this
let spray = [];
for (let i = ; i < 100000; i++) {
spray.push("A".repeat(10000)); // Fill memory with data
}
The real exploit would be considerably more complex and target the vulnerable Firefox functionality, but bugs like these can and do enable remote code execution.
References and Advisory
- Mozilla Foundation Security Advisory 2022-06
- NVD listing for CVE-2022-0511
- SecurityLab: Heap Exploitation Techniques
- Mozilla Bug Tracker Example (for general examples of similar issues)
How to Protect Yourself
- Update Firefox. If you haven’t updated past Firefox 97, you are at risk! The fastest and best solution is to upgrade to the current version.
- Stay cautious on the web. Don’t click suspicious links or visit unknown sites looking for exploit PoCs.
Conclusion
CVE-2022-0511 reminds us how critical memory safety is for browsers—and how quickly attackers can leverage such bugs for dangerous attacks. Thanks to Mozilla’s dedicated fuzzers and developer community, these flaws got patched quickly. But the lesson is clear: always keep your browser updated, and know that seemingly minor bugs can have devastating impact if left unfixed.
Timeline
Published on: 12/22/2022 20:15:00 UTC
Last modified on: 12/29/2022 18:53:00 UTC