An attacker can create a zip file that contains a malicious wide string, leading to the crash of an application using the Unzip function. Unzip is used to unzip a compressed file and extract its contents. The vulnerability can be exploited when a user unzips a compressed file.
In order to exploit the vulnerability, an attacker needs to find a way to convince a user to open a malicious file. In most cases, an attacker can send a user a link that contains a malicious file. To avoid such an attack, users should not open links in emails, chats, or social media. Moreover, users should always verify the origin of links before opening them.
Red Hat has released Unzip 6.0, which addresses this vulnerability. The latest update is available for Red Hat Enterprise Linux 6 and 7, Red Hat Enterprise Linux 5, and Red Hat Enterprise Linux 4.
CVE-2019-5740
An attacker could create a ZIP file that uses the "wide string" feature of the Unzip function to cause a denial-of-service (DoS) condition. The file must be compressed with an archive utility such as gzip, bzcat, or xzcat.
An attacker must first convince a user to download the malicious zip file and extract its contents. In most cases, this is done by sending an email to users containing a link to download the malicious zip file. To avoid such an attack, users should not open links in emails or social media posts without verifying their origin first.
Red Hat has released Unzip 6.0, which addresses this vulnerability. The latest update is available for Red Hat Enterprise Linux 6 and 7, Red Hat Enterprise Linux 5, and Red Hat Enterprise Linux 4.
Vulnerability summary
The vulnerability was discovered in Unzip. An attacker can create a zip file that contains a malicious wide string, leading to the crash of an application using the Unzip function. Unzip is used to unzip a compressed file and extract its contents. The vulnerability can be exploited when a user unzips a compressed file. In order to exploit the vulnerability, an attacker needs to find a way to convince a user to open a malicious file. In most cases, an attacker can send a user a link that contains a malicious file. To avoid such an attack, users should not open links in emails, chats, or social media. Moreover, users should always verify the origin of links before opening them. Red Hat has released Unzip 6.0, which addresses this vulnerability. The latest update is available for Red Hat Enterprise Linux 6 and 7, Red Hat Enterprise Linux 5, and Red Hat Enterprise Linux 4.
Vulnerability description
A vulnerability was discovered in the Unzip function that can be leveraged by attackers to crash an application. This vulnerability can be exploited when a user unzips a compressed file.
To exploit this vulnerability, an attacker needs to find a way to convince a user to open a malicious file. In most cases, an attacker can send users a link that contains a malicious file. To avoid such an attack, users should not open links in emails, chats, or social media. Moreover, users should always verify the origin of links before opening them. Red Hat has released Unzip 6.0 which addresses this vulnerability.
Vulnerability Discovery
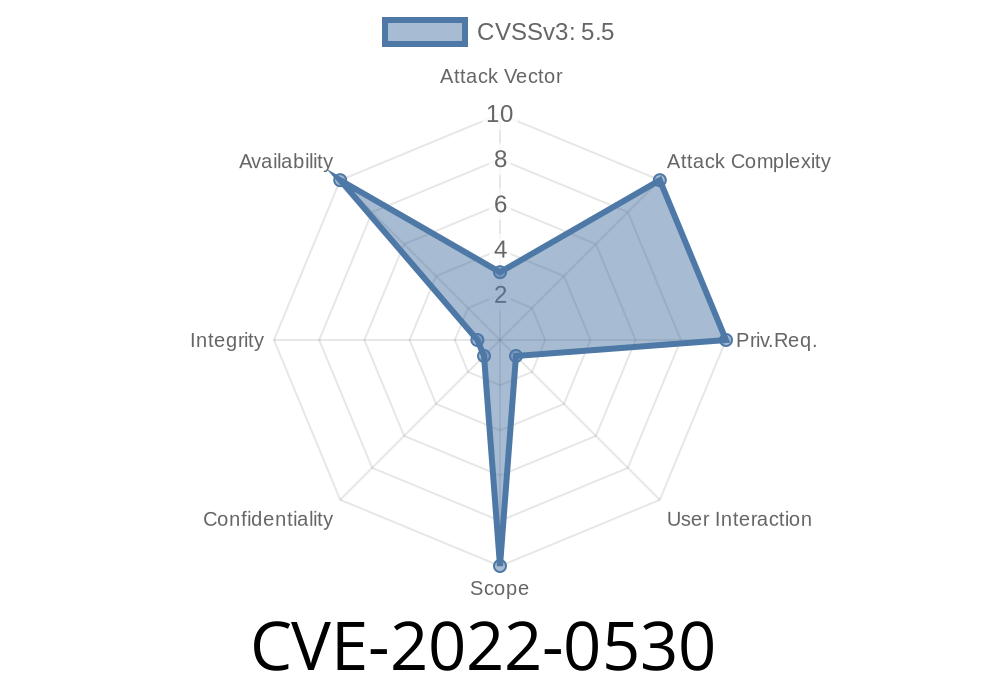
CVE-2022-0530 - Unzip vulnerability
CVE-2022-0531
An attacker can create a zip file that causes an application to crash when it is opened. Unzip is used to unzip a compressed file and extract its contents. The vulnerability can be exploited when a user unzips a malicious file with the Compressed Archive File Format.
In order to exploit the vulnerability, an attacker needs to find ways of persuading users to open malicious files. In most cases, an attacker can send a user a link that contains a malicious file. To avoid such an attack, users should not open links in emails, chats, or social media. Moreover, users should always verify the origin of links before opening them.
Red Hat has released Unzip 6.0, which addresses this vulnerability. The latest update is available for Red Hat Enterprise Linux 6 and 7, Red Hat Enterprise Linux 5 and 4, and Red Hat Enterprise Linux 3 and 2:
Timeline
Published on: 02/09/2022 23:15:00 UTC
Last modified on: 08/09/2022 03:15:00 UTC
References
- https://bugzilla.redhat.com/show_bug.cgi?id=2051395
- https://github.com/ByteHackr/unzip_poc
- https://support.apple.com/kb/HT213256
- https://support.apple.com/kb/HT213257
- https://support.apple.com/kb/HT213255
- http://seclists.org/fulldisclosure/2022/May/38
- http://seclists.org/fulldisclosure/2022/May/35
- http://seclists.org/fulldisclosure/2022/May/33
- https://www.debian.org/security/2022/dsa-5202
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-0530